Inside the Massive Alleged AT&T Data Breach
Troy Hunt
MARCH 18, 2024
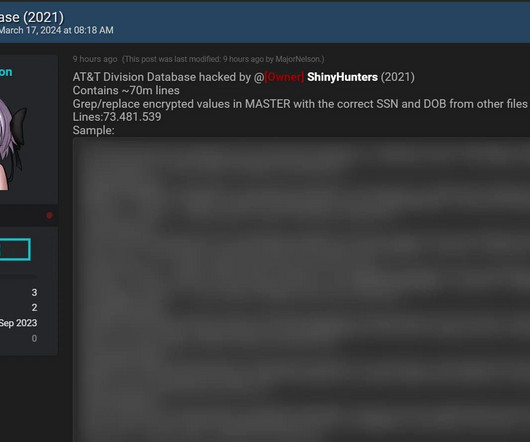
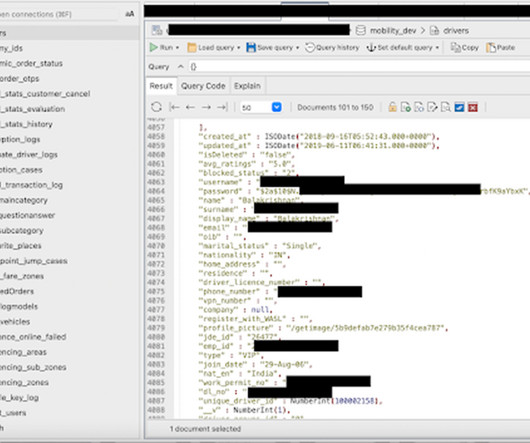
So, let's focus on what we can prove, starting with the accuracy of the data. The linked article talks about the author verifying the data with various people he knows, as well as other well-known infosec identities verifying its accuracy. The above example simply didn't have plain text entries for the encrypted data.











































Let's personalize your content