Tracking Stolen Cryptocurrencies
Schneier on Security
SEPTEMBER 27, 2021
Good article about the current state of cryptocurrency forensics.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
SEPTEMBER 27, 2021
Good article about the current state of cryptocurrency forensics.

Security Affairs
OCTOBER 13, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Over 300,000!
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Graham Cluley
NOVEMBER 4, 2021
A British man has been charged by the US Department of Justice for his alleged role in stealing $784,000 worth of cryptocurrency in a series of SIM swap attacks. Read more in my article on the Tripwire State of Security blog.

Schneier on Security
NOVEMBER 16, 2023
Examples included: Azure Active Directory API Keys GitHub OAuth App Keys Database credentials for providers such as MongoDB, MySQL, and PostgreSQL Dropbox Key Auth0 Keys SSH Credentials Coinbase Credentials Twilio Master Credentials.

Schneier on Security
SEPTEMBER 18, 2019
I learned about it in this article about Phil Dougherty, who helps people recover lost cryptocurrency passwords (mostly Ethereum) for a cut of the recovered value. It's "useful for cracking passwords you kinda-remember." You tell the program what you remember about the password and it tries related passwords.

CyberSecurity Insiders
JANUARY 17, 2022
North Korea, the nation that is being led by Kim Jong UN is back into news headlines for stealing cryptocurrency worth millions through cyber attacks. The post North Korea steals $400m cryptocurrency through Cyber Attacks appeared first on Cybersecurity Insiders.

CyberSecurity Insiders
AUGUST 23, 2021
If you are a cryptocurrency enthusiast and are using any of the mining apps to earn more, then this article needs your interest. The post Google bans the following cryptocurrency apps for data security appeared first on Cybersecurity Insiders.

Graham Cluley
JUNE 3, 2021
Cybercriminals are running an online competition offering big prizes to anyone who believes they have found an unusual way to help crooks steal cryptocurrency. Read more in my article on the Tripwire State of Security blog.

Trend Micro
DECEMBER 11, 2022
We intercepted a cryptocurrency mining attack that incorporated an advanced remote access trojan (RAT) named the CHAOS Remote Administrative Tool.
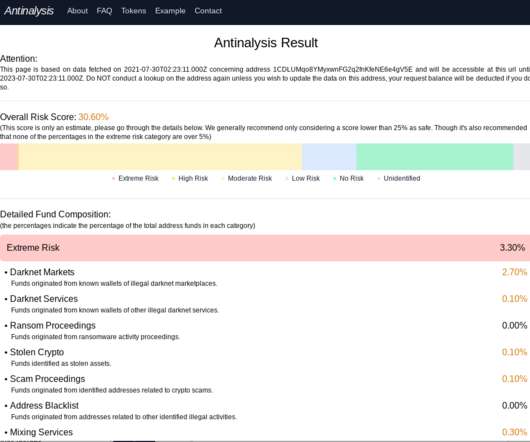
Krebs on Security
AUGUST 13, 2021
A new dark web service is marketing to cybercriminals who are curious to see how their various cryptocurrency holdings and transactions may be linked to known criminal activity. “The likes of ransomware and darknet markets rely on payments being made in Bitcoin and other cryptocurrencies. ” That may not be entirely true.

Graham Cluley
SEPTEMBER 24, 2024
Two men have been arrested by the FBI and charged in relation to their alleged involvement in a scam which saw almost a quarter of a billion dollars worth of cryptocurrency stolen from a single victim. Two men arrested one month after $230 million of cryptocurrency stolen from a single victim.

Graham Cluley
JUNE 12, 2023
Gox cryptocurrency exchange, the US Department of Justice says it has identified and charged two men it alleges stole customers' funds and the exchange's private keys. Read more in my article on the Tripwire State of Security blog. More than ten years after the hack of the now-defunct Mt.

Trend Micro
OCTOBER 3, 2022
The parasitic Water Labbu capitalizes on the social engineering schemes of other scammers, injecting malicious JavaScript code into their malicious decentralized application websites to steal cryptocurrency.

CSO Magazine
SEPTEMBER 21, 2021
The Biden administration has introduced new sanctions against cryptocurrency exchange Suex to stifle revenue for ransomware groups. To read this article in full, please click here The Treasury Department has also updated guidance to US businesses on paying ransoms to cybercriminals, saying that it “strongly discourages” such action.

Trend Micro
AUGUST 17, 2021
We recently discovered eight deceptive mobile apps that masquerade as cryptocurrency cloud mining applications where users can earn cryptocurrency by investing money into a cloud-mining operation.

Trend Micro
MARCH 23, 2022
We provide an overview of the diverse range of NFT- and cryptocurrency-related scams that malicious actors use to steal assets worldwide.

Hot for Security
JANUARY 25, 2021
Another day, and another report that a cryptocurrency exchange has been breached by malicious hackers. Indian cryptocurrency exchange BuyUCoin says that is investigating claims that sensitive data related to hundreds of thousands of its users has been published on the dark web, where it is available for free download.

Graham Cluley
FEBRUARY 28, 2024
The post asked for cryptocurrency donations "to support our mission in battling addiction." Read more in my article on the Hot for Security blog. Matthew Perry's official Twitter account was hijacked by scammers this week who attempted to solicit donations from well-meaning fans of the much-loved late actor.

CSO Magazine
FEBRUARY 17, 2022
As high-stakes cryptocurrency and blockchain projects proliferate and soar in value, it’s no surprise that malicious actors were enticed to steal $14 billion in cryptocurrency during 2021 alone. The frantic pace of cryptocurrency thefts is continuing into 2022. To read this article in full, please click here

Krebs on Security
MARCH 7, 2022
This final post on the Conti conversations explores different schemes that Conti pursued to invest in and steal cryptocurrencies. This wealth allowed Conti to do things that regular investors couldn’t — such as moving the price of cryptocurrencies in one direction or the other. “Cryptocurrency article contest! .

Graham Cluley
NOVEMBER 23, 2023
The Kimsuky hacking gang has been accused of impersonating South Korean officials and journalists in a plot to steal cryptocurrency for the North Korean regime. Read more in my article on the Hot for Security blog.
Graham Cluley
JANUARY 4, 2024
Read my article on the Tripwire State of Security blog. No one is too big, too clever, too security-savvy to avoid being duped - because it's only human to make a mistake and screw up.
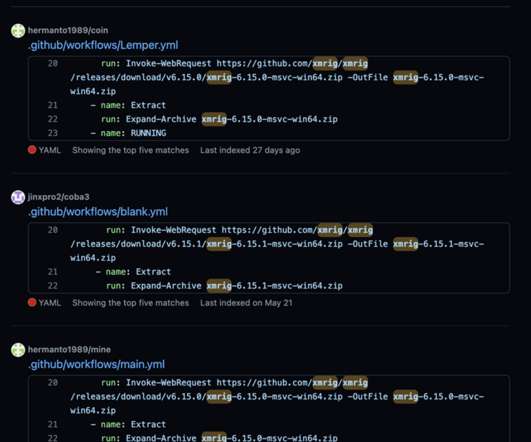
Security Affairs
JULY 12, 2022
Researchers investigated cloud-based cryptocurrency mining attacks targeting GitHub Actions and Azure VMs. Researchers from Trend Micro published a report that details cloud-based cryptocurrency mining attacks targeting GitHub Actions and Azure VMs and the threat actors behind them. ” states the report published by Trend Micro.

Security Affairs
APRIL 6, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape CISA Releases Malware Analysis Report on RESURGE Malware Associated with Ivanti Connect Secure Unboxing Anubis: Exploring the Stealthy Tactics of FIN7’s Latest Backdoor Advancements in delivery: Scripting with (..)

Security Affairs
NOVEMBER 3, 2024
Every week the best security articles from Security Affairs are free in your email box. A new round of the weekly SecurityAffairs newsletter arrived! Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

Security Affairs
NOVEMBER 17, 2024
Every week the best security articles from Security Affairs are free in your email box. A new round of the weekly SecurityAffairs newsletter arrived! Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

Schneier on Security
AUGUST 24, 2020
You can then use that key to derive master passwords for password managers, as the seed to create a U2F key for two-factor authentication, or even as the secret key for cryptocurrency wallets. Another news article. Here's the DiceKeys website and app. Here's a short video demo. Here's a longer SOUPS talk. Preorder a set here.

Security Affairs
OCTOBER 13, 2024
Every week the best security articles from Security Affairs are free in your email box. A new round of the weekly SecurityAffairs newsletter arrived! Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.
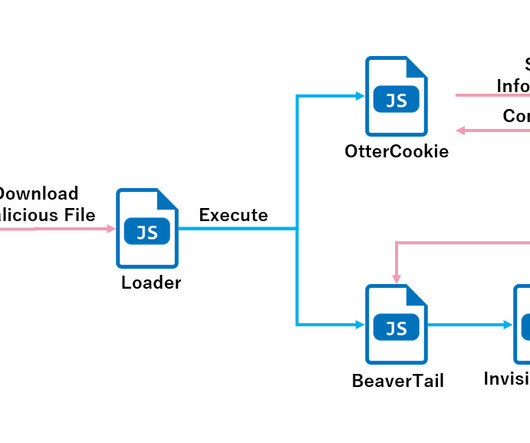
Security Affairs
DECEMBER 27, 2024
In this article, we will introduce OtterCookie, its execution flow and detailed behavior.” Threat actors used shell commands to search for cryptocurrency wallet keys in document, image, and cryptocurrency-related files, which were then sent to a remote source. ” reads the report published by NTT.
Daniel Miessler
FEBRUARY 2, 2022
There’s something strange about how our InfoSec community is reacting to cryptocurrency, NFTs, and Web3. Moxie’s article on NFTs was an interesting example in that he didn’t completely bash the whole enterprise. Image from a Coindesk article by Annie Zhang. Mostly, it’s horribly negative.

Graham Cluley
APRIL 20, 2022
Cryptocurrency wallet maker MetaMask has warned its 21 million monthly users to be wary of Apple iCloud backing up their app's data by default, after attackers successfully stole $650,000 of funds and NFTs. Read more in my article on the Hot for Security blog.

CSO Magazine
OCTOBER 25, 2022
According to data from the Rekt leaderboard , cybercriminals have stolen as much as $3 billion of investor funds through 141 various cryptocurrency exploits since January, putting 2022 on track to top 2021 levels of digital currency malfeasance. Comparitech’s cryptocurrency heists tracker indicates that since 2011, hackers have stolen $7.9

Malwarebytes
JANUARY 5, 2022
There’s a lot of concern in the cryptocurrency realm at the moment. However, as the article notes, many projects are open source. What is a rug pull in cryptocurrency? A rug pull (or “being rugged”, as they call it in cryptocurrency circles) is not a fun experience. It’s a Wild West out there.

Security Affairs
APRIL 20, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Malicious NPM Packages Targeting PayPal Users New Malware Variant Identified: ResolverRAT Enters the Maze Nice chatting with you: what connects cheap Android smartphones, WhatsApp and cryptocurrency theft?

Graham Cluley
JANUARY 13, 2023
European law enforcement agencies have dealt a blow to scammers running call centres across the continent that stole millions of Euros from cryptocurrency investors. Crime-fighting authorities teamed up to tackle organised criminal groups who tricked unwary members of the public into investing in fake cryptocurrency schemes.

Identity IQ
MAY 3, 2021
There’s no doubt about it, cryptocurrency is increasingly entering into the main fray as a currency of choice. But also on the rise are cryptocurrency-related scams. According to the “Cryptocurrency Scam Report,” published by fraud prevention company Bolster, more than 400,000 crypto scams were created over the last year.
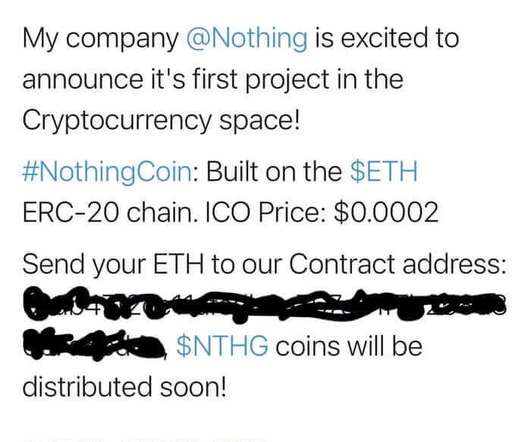
The State of Security
MAY 27, 2021
Read more in my article on the Tripwire State of Security blog. Even if you have chosen a strong, unique password for your online presence and enabled two-factor authentication it's possible that you've overlooked another way in which online criminals could commandeer your social media accounts and spam out a message to your followers.

CyberSecurity Insiders
JUNE 19, 2023
AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. While cryptocurrencies have been celebrated for their potential to revolutionize finance, their anonymous nature has also been exploited for illicit activities.

Trend Micro
FEBRUARY 8, 2023
We discovered an active campaign targeting Eastern Europeans in the cryptocurrency industry using fake job lures.
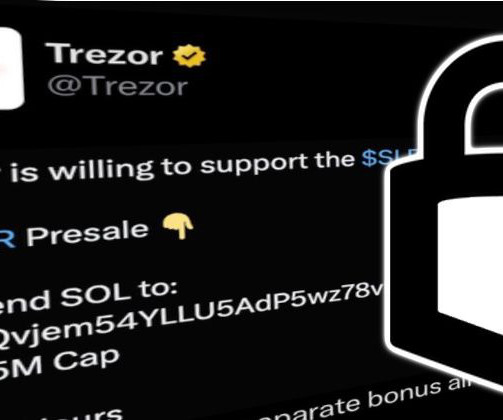
Graham Cluley
MARCH 27, 2024
Read more in my article on the Hot for Security blog. Hardware wallet manufacturer Trezor has explained how its Twitter account was compromised - despite it having sensible security precautions in place, such as strong passwords and multi-factor authentication.
Graham Cluley
AUGUST 14, 2024
Scammers are once again using deepfake technology to dupe unwary internet Facebook and Instagram users into making unwise cryptocurrency investments. Read more in my article on the Hot for Security blog.

Graham Cluley
NOVEMBER 23, 2023
US authorities have seized almost $9 million worth of cryptocurrency linked to a gang engaged in cryptocurrency investment fraud and romance scams. Read more in my article on the Tripwire State of Security blog.

Trend Micro
MARCH 28, 2022
One of the recent trends we’ve observed is the rise of cloud-based cryptocurrency-mining groups that exploit cloud resources, specifically the CPU power of deployed cloud instances, to mine cryptocurrency.

Trend Micro
JUNE 5, 2023
We have been able to uncover a massive cryptocurrency scam involving more than a thousand websites handled by different affiliates linked to a program called Impulse Project, run by a threat actor named Impulse Team.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content