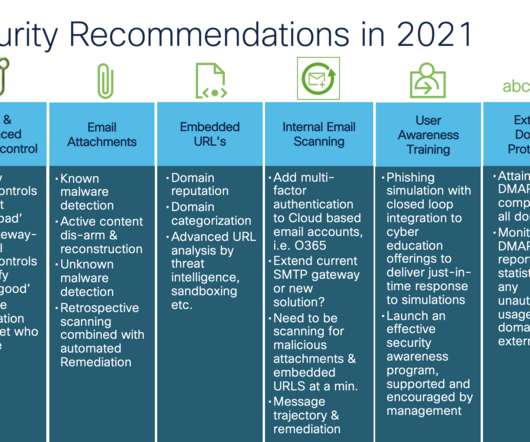
Email Security Recommendations You Should Consider from 2021
Cisco Security
AUGUST 17, 2021
With contributions from Jamal “Jay” Bethea, Cisco Secure Email Product Marketing Manager. Think email security is not complicated; think again. Email Attachments: One of two main methods to penetrate security defenses with malicious content by email.




































Let's personalize your content