CISO workshop slides
Notice Bored
AUGUST 5, 2022
A glossy, nicely-constructed and detailed PowerPoint slide deck by Microsoft Security caught my beady this morning.
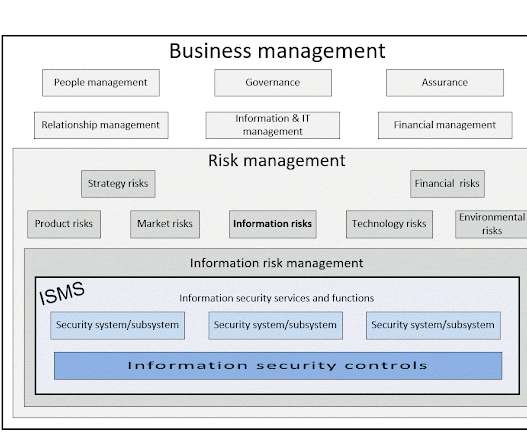
Notice Bored
AUGUST 5, 2022
A glossy, nicely-constructed and detailed PowerPoint slide deck by Microsoft Security caught my beady this morning.

Troy Hunt
JUNE 10, 2019
Increasingly, I was writing about what I thought was a pretty fascinating segment of the infosec industry; password reuse across Gawker and Twitter resulting in a breach of the former sending Acai berry spam via the latter. haveibeenpwned you guys are legends.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Herjavec Group
MAY 17, 2021
Herjavec Group supports the Assessment, Design, Deployment, and Management of your IAM solutions through a comprehensive offering including Strategic Workshops, Advisory Services, Architecture & Implementation, and Managed IAM. About CDM InfoSec Awards . Learn more? Learn more at www.cyberdefenseawards.com .

Kali Linux
MARCH 28, 2023
In information security (infosec) there is the need to be on the latest version. Writing exploits or developing infosec tools is no exception, they often need to have access to the latest libraries. ARM - multi architecture Since BackTrack 4, the option was there for ARM support. This helps make the system more robust.

ForAllSecure
SEPTEMBER 10, 2021
PPP wanted to give their past high school selves the infosec education they didn’t have. Megan Kerns of Carnegie-Mellon University joins The Hacker Mind to talk about the early days and the continued evolution of this popular online infosec competition site. in InfoSec however, learning happens 365 days a year.

NetSpi Technical
AUGUST 16, 2024
Infosec is a constant cat and mouse game, it is important to keep on top of new research and newly discovered attack surface area in order to test and detect the security flaws before the threat actors do. Don’t be afraid of sending large (4gig +) payloads for clear/white/open box testing.
Cisco Security
FEBRUARY 16, 2021
However, when you are assigning architectural controls to mitigate that risk, it lacks validation. In fact, this report will change how we think about running infosec programs.”. Attend a Threat Hunting Workshop. In time, tech refresh and threat hunting should be part of the standard security approach in all organizations.
Let's personalize your content