Cooking Intelligent Detections from Threat Intelligence (Part 6)
Anton on Security
DECEMBER 1, 2023
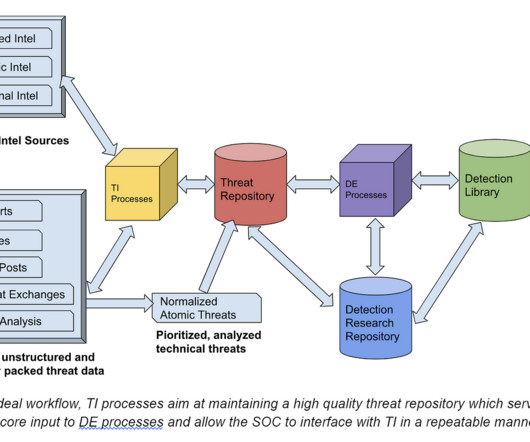
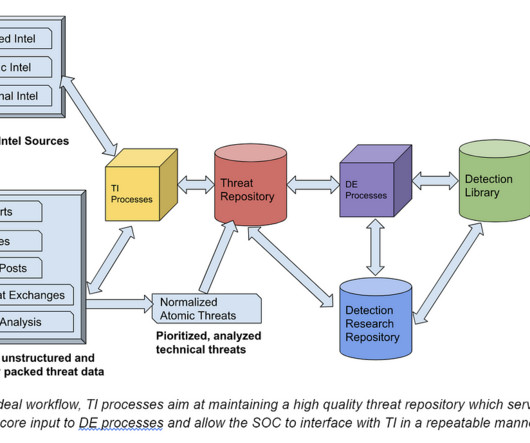
This blog series was written jointly with Amine Besson, Principal Cyber Engineer, Behemoth CyberDefence and one more anonymous collaborator. TI serves as a key input for detection engineering (DE), the team that directly benefits from its findings. OK, What does DE expect from Intel?












Let's personalize your content