Beyond the Surface: the evolution and expansion of the SideWinder APT group
SecureList
OCTOBER 15, 2024
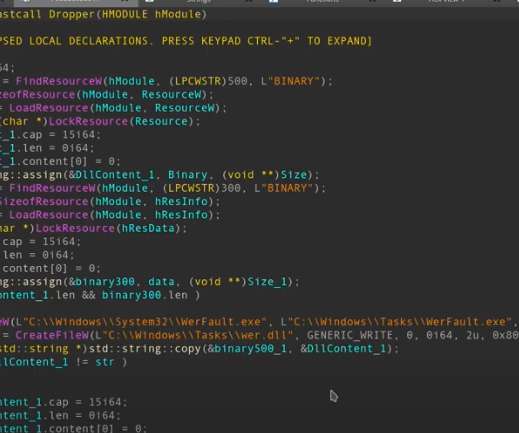
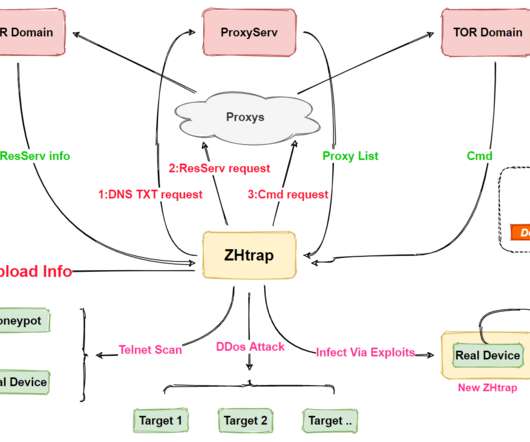
The document or LNK file starts a multi-stage infection chain with various JavaScript and.NET downloaders, which ends with the installation of the StealerBot espionage tool. All the documents use the remote template injection technique to download an RTF file that is stored on a remote server controlled by the attacker.





































Let's personalize your content