Securing the edge with Zero Trust
CyberSecurity Insiders
OCTOBER 7, 2021
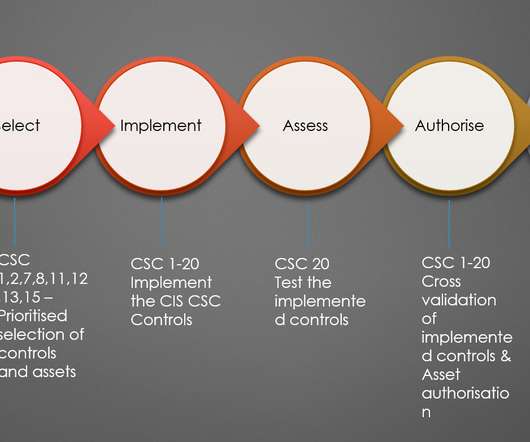
This requires data-level protections, a robust identity architecture, and strategic micro-segmentation to create granular trust zones around an Organization’s digital resources. Think of it like the government or military’s “need-to-know” policy. The Zero Trust journey. Implementing Zero Trust.

























Let's personalize your content