Storm-050: A New Ransomware Threat Identified by Microsoft
SecureWorld News
SEPTEMBER 30, 2024
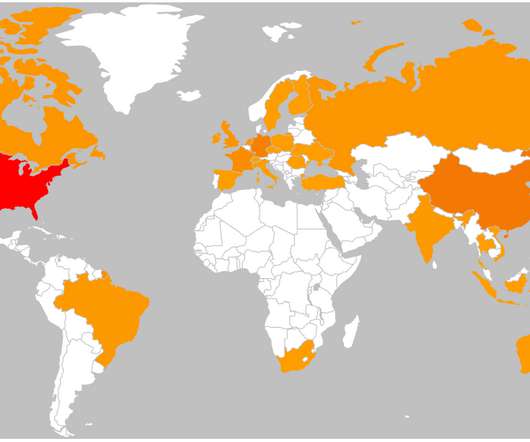
including government, manufacturing, transportation, and law enforcement. Tiquet continued: "One of the most important steps is adopting a zero trust architecture. Use multi-factor authentication to prevent unauthorized access. The group is now expanding its operations by targeting U.S.











































Let's personalize your content