AI and Cyber Security: Innovations & Challenges
eSecurity Planet
SEPTEMBER 16, 2024
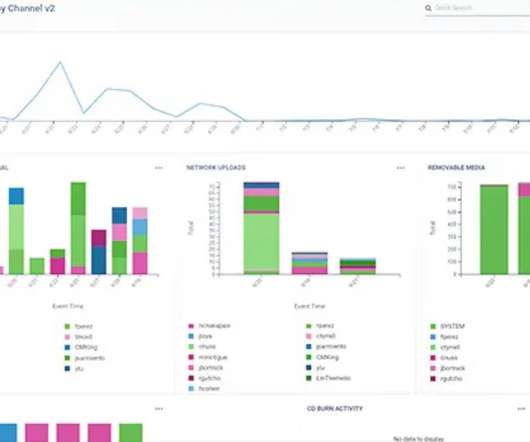
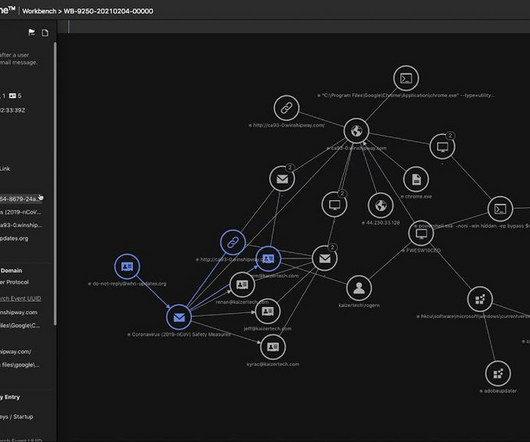
As cyber threats become increasingly sophisticated, integrating artificial intelligence (AI) into cybersecurity is more than a passing trend — it’s a groundbreaking shift in protecting our digital assets. As cyber-attacks grow increasingly complex, leveraging AI becomes crucial for staying ahead of emerging threats.


















Let's personalize your content