Unleashing the Power of a Security Data Lake
SecureWorld News
APRIL 3, 2023
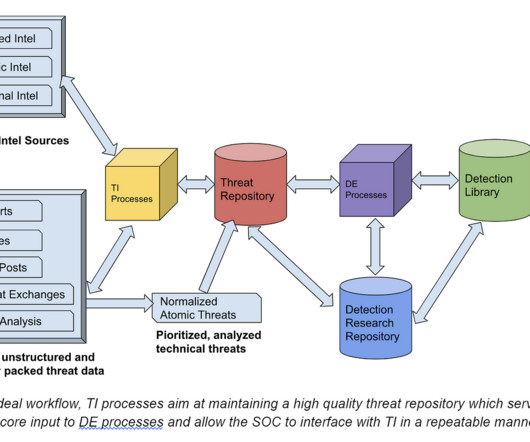
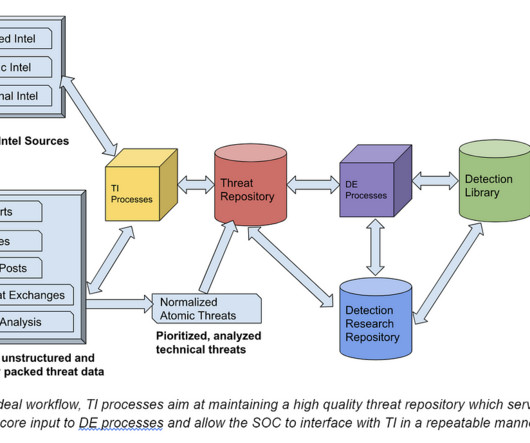
A Security Data Lake accumulates all the indicators gathered from the Security Operations Center and analyzing this data may form the basis for establishing robust information security within an organization. This problem becomes even more pronounced when dealing with vast amounts of data. Scalable architecture.










Let's personalize your content