New Linux Malware Shikitega Can Take Full Control of Devices
eSecurity Planet
SEPTEMBER 15, 2022
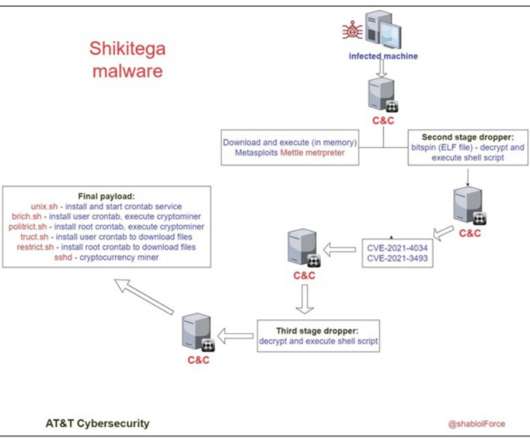
The researchers said the attackers have encoded the final payload with several layers, requiring several loops of decoding before it gets deployed, making it impossible to detect by signature-based antivirus solutions. Five Scripts Provide Persistence. How to Protect Against Shikitega.















Let's personalize your content