How to Configure a Router to Use WPA2 in 7 Easy Steps
eSecurity Planet
MARCH 3, 2023
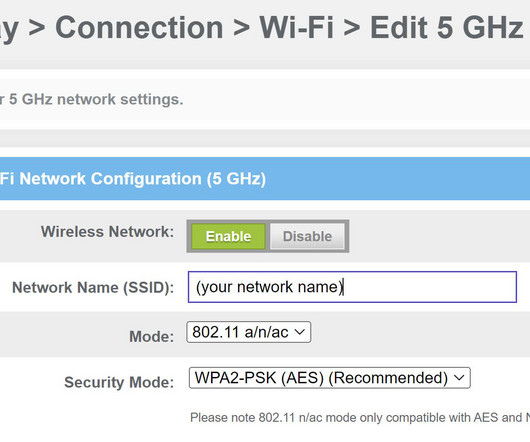
Most of us connect our mobile devices to a Wi-Fi router for internet access, but this connection can leave our network and data vulnerable to cyber threats. To protect against those threats, a Wi-Fi Protected Access (WPA) encryption protocol is recommended. Step 6: Reboot Reboot your router, if necessary, to apply the changes.

















Let's personalize your content