New SteelFox Trojan mimics software activators, stealing sensitive data and mining cryptocurrency
SecureList
NOVEMBER 6, 2024
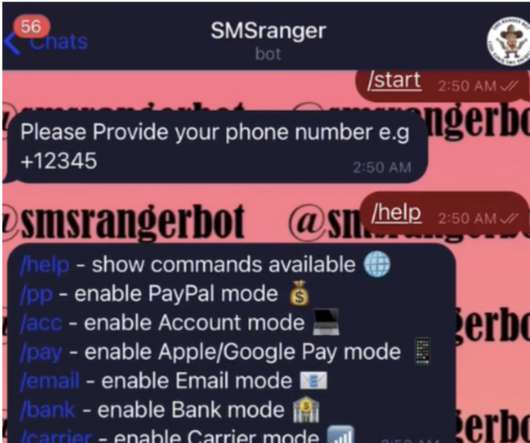
Type of data Details Browser data Cookies, credit cards, location, search history Software Installed software, antivirus solutions, running services, installed addons System info Build date (if possible), version, revision, installation date Network info Wireless interfaces, networks and passwords (extracted as plaintext) SIM SIM-card data (if applicable) (..)














Let's personalize your content