Mysterious custom malware used to steal 1.2TB of data from million PCs
Security Affairs
JUNE 11, 2021
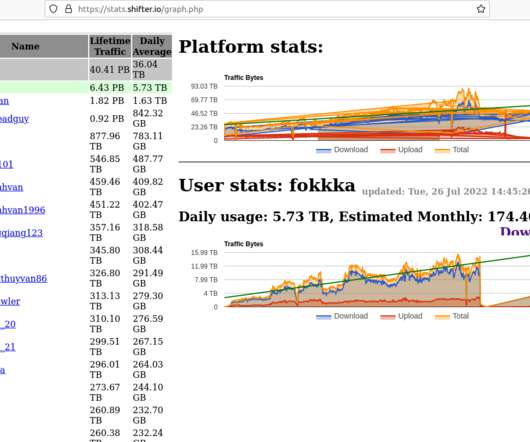
“The data was collected from 3.25 million computers. ” The experts pointed out that custom malware used to amass such kind of data is very cheap, easy to find online and customizable. How to protect your data from such kind of malware? SecurityAffairs – hacking, custom malware). million files.”










Let's personalize your content