SECURITY AFFAIRS MALWARE NEWSLETTER – ROUND 22
Security Affairs
DECEMBER 1, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Security Affairs
DECEMBER 1, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Adam Levin
JULY 10, 2020
A recent article released by cybersecurity and antivirus firm Bitdefender shows that 8.4 Phishing scams skyrocketed as citizens self-isolated during the lockdown, and social-engineering schemes defrauded Internet users of millions.”. For comparison, that’s a 273% increase over the first two quarters of 2019 combined.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
APRIL 2, 2021
News article : Most troublingly, Activision says that the “cheat” tool has been advertised multiple times on a popular cheating forum under the title “new COD hack.” “Guides for cheats will typically ask users to disable or uninstall antivirus software and host firewalls, disable kernel code signing, etc.”

Hacker's King
DECEMBER 16, 2024
This article provides an overview of recent cyber attacks, highlights the evolving tactics used by cybercriminals, and discusses strategies to protect against these threats. Cybercriminals are also increasingly using social media to gather intelligence, exploit personal information, and initiate attacks.

SecureWorld News
DECEMBER 30, 2024
While this article focuses on handling data breaches, a comprehensive Business Continuity Plan (BCP) encompasses a broad spectrum of risks, including pandemics, natural disasters, financial instability, and human errors. Social engineering techniques enable them to bypass technical security measures effectively.

Hacker's King
DECEMBER 17, 2024
This article explores the workings of the new Linux FASTCash variant, its implications for the financial sector, and how organizations can mitigate its risks. Stealth Capabilities : The malware is designed to avoid detection by traditional antivirus solutions, employing techniques such as process masquerading and rootkit-like functionality.

SecureList
MAY 17, 2021
In this article we analyse the technical features of the Trojan’s components, giving a detailed overview of obfuscation techniques, the infection process and subsequent functions, as well as the social engineering tactics used by the cybercriminals to convince their victims to give away their personal online banking details.
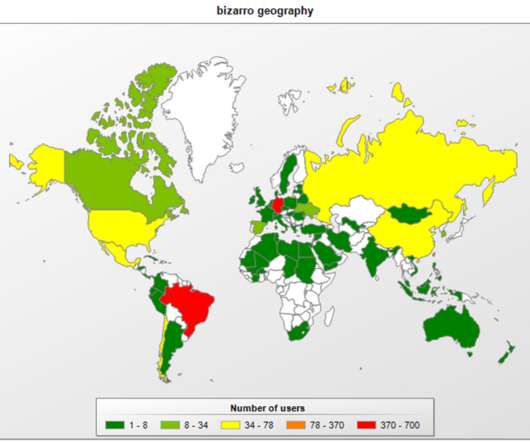
Security Affairs
MAY 17, 2021
Experts pointed out that it also leverages social engineering to trick victims into downloading a mobile app. While writing this article, we saw hacked WordPress, Amazon and Azure servers used for storing archives. Experts also noticed that the malware is also installed via a trojanized app.

CSO Magazine
NOVEMBER 21, 2022
Callback phishing – or telephone-oriented attack delivery (TOAD) – is a social engineering attack that requires a threat actor to interact with the target to accomplish their objectives. As these tools are not malicious, they’re not likely to be flagged by traditional antivirus products,” the researchers wrote.

Malwarebytes
MARCH 4, 2022
There are rootkits, Trojans, worms, viruses, ransomware, phishing, identity theft, and social engineering to worry about. Content blockers help reduce ads, Trojans, phishing, and other undesirable content that an antivirus product alone may not stop. That risk still exists, but we all face many other threats today too.

Identity IQ
JUNE 7, 2021
Misrepresentation, a form of social engineering that occurs when a hacker poses as a trusted source – such as a member of an organization’s executive team – to convince people to give up their credentials was also 15 times higher last year compared to the year before. billion malicious login attempts last year.

The Last Watchdog
MARCH 21, 2023
They may incorporate tools such as firewalls or antivirus software , which are helpful, but not the only tactics that can keep a network secure. Threat actors will still use social engineering tactics like phishing or ransomware to target businesses, steal data and earn a significant payday.

CyberSecurity Insiders
JUNE 13, 2023
This article will provide you with a comprehensive guide on how to create cybersecurity awareness and protect yourself and your digital assets from potential threats. Stay informed about the latest cyber threats, such as phishing, malware, ransomware, and social engineering attacks.

Malwarebytes
OCTOBER 29, 2021
There are rootkits, Trojans, worms, viruses, ransomware, phishing, identity theft, and social engineering to worry about. Today, content blockers have become essential to help reduce ads, Trojans, phishing, and other undesirable content that an antivirus product alone may not cover. And that’s not a comprehensive list.

Security Through Education
OCTOBER 22, 2024
This article will focus on you, and how you can “secure your world.” Report Phishing At Social-Engineer, LLC, we define phishing as “the practice of sending emails appearing to be from reputable sources with the goal of influencing or gaining personal information.” Let’s review them together!

Identity IQ
MAY 7, 2021
Social Engineering: Cybercriminals are increasingly using sophisticated social engineering tools to trick people into revealing their login credentials. The Dark Web: The dark web is where hacked accounts and stolen personal data is bought and sold. This includes bulk collections of details stolen in data breaches.
Malwarebytes
MAY 9, 2023
Malvertising seems to be enjoying a renaissance as of late, whether it is from ads on search engine results pages or via popular websites. Because browsers are more secure today than they were 5 or 10 years ago, the attacks that we are seeing all involve some form of social engineering. build1_enc_s.exe).

Security Boulevard
MARCH 5, 2025
As explained in this darkreading article , AI models can create malware that contains no malicious code at all until runtime, making it extremely hard to detect with signature-based or static analysistools. This blog examines the first vector: AI-Generated Polymorphic Malware.

Spinone
OCTOBER 10, 2019
Here you can find more than 20 news articles each week. The main focus here is the social side of data loss. This blog educates about social engineering attacks and ways to prevent them. Here you can find articles on recent cybersecurity updates. Spinbackup Blog Yep, that’s the blog you are reading now.

SecureList
JUNE 2, 2022
In this article, we will focus on one of the most groundbreaking developments: the fact that LuoYu has the ability to perform man-on-the-side attacks. This is consistent with the scenario described earlier in this article, where the target receives an infected executable instead of the normal one. Delivery method. WinDealer samples.

Responsible Cyber
JULY 13, 2024
This article explores these strategies in-depth: 1. Social Engineering Techniques Social engineering is different—it’s about manipulating people instead of hacking technology. Real-life examples show how effective social engineering can be. What makes training effective?

Identity IQ
DECEMBER 20, 2023
Major Breaches of 2023 Casino operator attacks: Casino giants MGM and Caesars were hit by disruptive cyberattacks in September involving concerning tactics such as social engineering. This signals a new era of cybercrime where private data becomes prized currency, putting every email address and credit card number at risk.

Spinone
APRIL 13, 2020
As you probably know, phishing involves various social engineering methods. You can read more about this in our article about how ransomware works. You can read more about it in our articles about ransomware and antivirus software and ransomware detection using machine learning. And not without a reason.

eSecurity Planet
MARCH 9, 2023
For this article we focused on vulnerability scanners that emphasize an MSP/MSSP offering. Multi-tenant capabilities were also considered as a factor to make this list. We excluded very capable vulnerability scanning tools such as open source tools and vendors that may have a more limited promotion of MSP/MSSP programs.

eSecurity Planet
AUGUST 26, 2022
Whereas older solutions like antivirus, firewalls, and endpoint detection and response (EDR) have long focused on threats at the network perimeter, the intent of NDR is to monitor and act on malicious threats within organization networks using artificial intelligence (AI) and machine learning (ML) analysis.

CyberSecurity Insiders
NOVEMBER 18, 2021
Numerous articles, vulnerability reports, and analytical materials prove this fact. Social engineering. This blog was written by an independent guest blogger. Most cyberattacks originate outside the organization. Obviously, it is impossible to provide protection at all stages of an attack using only one type of protection.

SecureWorld News
SEPTEMBER 27, 2023
Another might focus on the command protocols used in a specific malware, while yet another details the techniques a malicious entity employs to evade sandbox detections or antivirus software. And if a threat actor employs social engineering , the analyst might even need a basic grasp of psychology.

eSecurity Planet
OCTOBER 15, 2024
This article explores why cybersecurity for small businesses matters, common challenges, effective strategies, and essential tools to help you strengthen your defenses. Without proper training, however, they may unknowingly expose the business to risks such as phishing scams or social engineering attacks.

Hacker's King
OCTOBER 10, 2024
This article breaks down the revenue streams that keep the cybersecurity industry thriving. These software solutions range from antivirus programs and firewalls to more advanced intrusion detection systems and encryption tools. But have you ever wondered how these cybersecurity companies make money?

Zigrin Security
OCTOBER 11, 2023
In this article, we will explore the motivations of the hackers, which threat actors target which data, how to protect yourself or your organization against these threat actors, and most importantly what these threat actors do with your data. There are some other ways to make money from data described further in the article.

Identity IQ
MAY 13, 2024
Breaches can occur due to various reasons, including cyberattacks, hacking, employee negligence, physical loss of devices, and social engineering to name a few. This could also pertain to business information such as trade secrets and customer data.

Hacker's King
OCTOBER 3, 2024
This article looks at how unpatched vulnerabilities, especially on platforms like WhatsApp, are becoming a serious security concern for both individuals and businesses. You may like to read more about Social Media Botnets – Hackers leveraging bots for large-scale attacks What Are Zero-Day Exploits?

Cytelligence
FEBRUARY 25, 2023
In this article, we will explore the six types of cybersecurity, their importance, and how to prevent cyber attacks. Phishing: Phishing is a type of social engineering attack where cybercriminals trick people into giving away sensitive information such as usernames, passwords, and credit card details.

SiteLock
OCTOBER 12, 2021
This article reviews the above as well as some other security concerns. David Balaban is a computer security researcher with over 17 years of experience in malware analysis and antivirus software evaluation. Public cloud Infrastructure should be secured. Who is to ensure it? How to control cloud service providers?

Identity IQ
APRIL 12, 2023
Social Engineering Identity thieves manipulate victims’ emotions to get them to compromise their personal information. Secure Your Devices When filing your taxes online, use antivirus and anti-malware software on your computer, tablet, or smartphone. Remember, the IRS will never reach out to you through emails.

Identity IQ
JUNE 3, 2024
This article delves into the various biometric authentication methods, explaining how they work and how biometrics can help prevent identity theft. Here are some key strategies you can adopt: Be Mindful of What You Share Online: Limit the amount of personal information you share on social media or public websites.

Hacker's King
OCTOBER 7, 2024
This article delves into the importance of IPL in cybersecurity , how it’s being utilized in 2024, and how professionals and organizations alike can leverage it to create more secure environments. Attacks such as boot kits and rootkits can infiltrate the system even before antivirus programs and other protective measures come online.

Hacker's King
OCTOBER 9, 2024
Whether it’s your email client, operating system, or antivirus software, keeping everything up to date ensures you have the latest security patches. By implementing the tips below, you can effectively mitigate the risk of potential spam and protect your online activities.

Spinone
OCTOBER 16, 2019
Check out this article from the Office support team on how to install system updates on your particular Office, and always be up to date. Keep your antivirus software up to date. However, don’t forget that even an updated antivirus may not detect advanced malware strains. Backup your data with professional backup services.

eSecurity Planet
MARCH 22, 2023
This article will briefly outline the types of security needed to secure a network. Endpoint Security: Antivirus , anti-spyware , endpoint detection and response (EDR), and other controls should be deployed to secure the endpoint against compromise. and mobile (phones, tablets, etc.)

Spinone
NOVEMBER 30, 2018
In this article we will take a look at major cybersecurity risks and best practices how to reduce or avoid corporate data leakage. Phishing and Social Engineering Attacks Phishing scams , in which hackers set up fake websites and applications in order to steal passwords can allow access to sensitive information within minutes.

SiteLock
OCTOBER 21, 2021
Later in this article, I will discuss how these functions differ from what WAF can do. David Balaban is a computer security researcher with over 17 years of experience in malware analysis and antivirus software evaluation. David runs MacSecurity.net and Privacy-PC.com.

eSecurity Planet
OCTOBER 9, 2024
5 Pricing 2/5 Core Features 4/5 Additional Features 4/5 Ease of Use 4/5 Customer Support 4/5 Trustworthiness 1/5 Connectwise boasts a variety of software solutions for businesses, but its ScreenConnect service is the one I’m looking at for this article. How Can I Access Another Computer Remotely for Free?

eSecurity Planet
FEBRUARY 16, 2021
This article dives into the lexicon of malware, offering descriptions, protections, and examples of each. As you browse the myriad of malicious software featured in this article, we offer tips for how best to defend against each type. Install an antivirus solution that includes anti-adware capabilities. Jump ahead: Adware.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content