Scranos – A Cross Platform, Rootkit-Enabled Spyware rapidly spreading
Security Affairs
APRIL 16, 2019
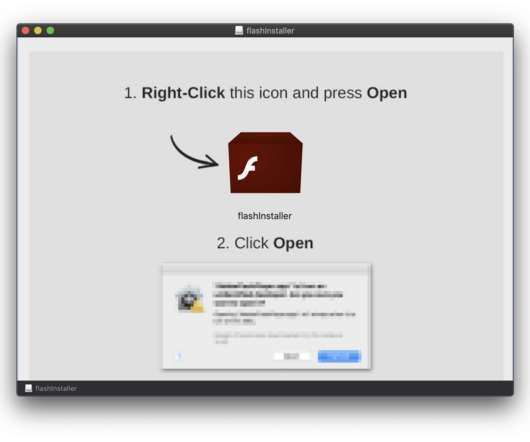
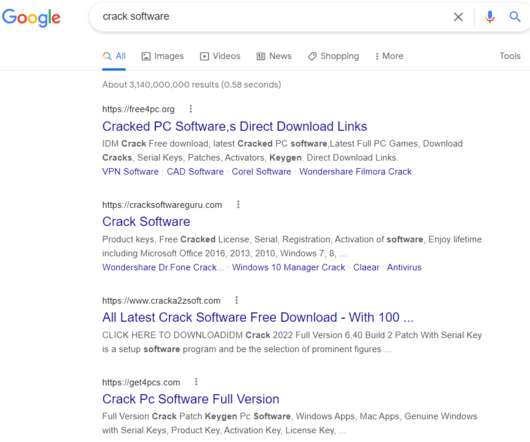
Scranos is a powerful cross-platform rootkit-enabled spyware discovered while investigating malware posing as legitimate software like video players, drivers and even anti-virus products. Although the campaign has not reached the magnitude of the Zacinlo adware campaign, it is already infecting users worldwide.”






























Let's personalize your content