Convuster: macOS adware now in Rust
SecureList
MARCH 18, 2021
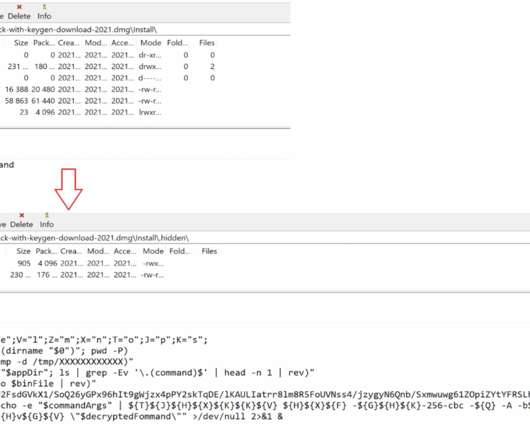
Traditionally, most malicious objects detected on the macOS platform are adware: besides the already familiar Shlayer family , the TOP 10 includes Bnodlero, Cimpli, Adload and Pirrit adware. The analysis showed these executables to be a new adware program, that has subsequently been called Convuster. Introduction. Distribution.













































Let's personalize your content