Websites Hosting Cracks Spread Malware, Adware
Trend Micro
MARCH 22, 2021
We investigated pay-per-install (PPI) websites spreading multiple malware and adware, including CopperStealer and LNKR.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Trend Micro
MARCH 22, 2021
We investigated pay-per-install (PPI) websites spreading multiple malware and adware, including CopperStealer and LNKR.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

SecureBlitz
MARCH 1, 2024
In this post, we will reveal Adware signs and effects. Adware is malicious software (malware) that prompts up ads on computer screens – usually while surfing the net. Plus, how to remove them from your web browsers. However, there is more to this program than malware.

SecureList
MARCH 12, 2021
In this article, we are going to take a look at threats for Macs with the Apple M1 chip on board. section at the end of the article for those who want to understand better the security risks of M1 malware. Adware threats for the new platform. Also, we prepared a short F.A.Q. Let’s dive in. XCSSET malware.

CSO Magazine
JUNE 10, 2022
We here at CSO have done our part: our malware explainer breaks down malware based on how it spreads (self-propagating worms , viruses piggybacking on other code, or sneakily disguised Trojans ) as well as by what it does to infected machines ( rootkits , adware , ransomware , cryptojacking , and malvertising , oh my).

CSO Magazine
FEBRUARY 22, 2023
To read this article in full, please click here Instead, the most dangerous threats come from a set of known, mature tools and tactics that an entire ecosystem of cybercriminals rely upon to take in billions of dollars a year."

Trend Micro
JUNE 22, 2021
While investigating samples of NukeSped, a remote access trojan (RAT), Trend Micro came across several Bundlore adware samples using the same fileless routine that was spotted in NukeSped.

Security Affairs
APRIL 16, 2019
The operation, partially described in a recent article by Tencent, primarily targeted Chinese territory until recently, when it broke out around the world.” Although the campaign has not reached the magnitude of the Zacinlo adware campaign, it is already infecting users worldwide.”

Schneier on Security
FEBRUARY 4, 2020
From a news article : The researchers also reported that the OkCupid app sent a user's ethnicity and answers to personal profile questions -- like "Have you used psychedelic drugs?" -- to a firm that helps companies tailor marketing messages to users.

SecureWorld News
SEPTEMBER 30, 2022
This article does a good job of updating the variant that targets devices made my Taiwanese company QNAP. Here's an article we ran in February about a Deadbolt decryption key being released. Google Play and Apple Store caught in adware scheme. See the list of the most downloaded adware apps. This article has more.
Security Affairs
JULY 14, 2021
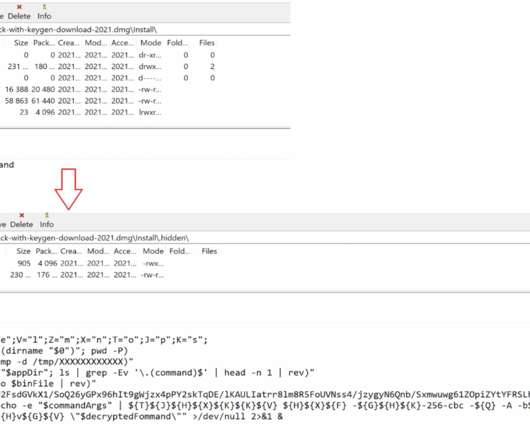
Though these scripts have slight variations, they mostly belong to a plague of adware strains— Shlayer and Bundlore. The malicious shell scripts used by Shlayer and Bundlore are usually malvertising-focused adware bundlers using shell scripts in the kill chain to download and install an adware payload. Conclusion.

Schneier on Security
DECEMBER 28, 2018
Lots of details in the article. Combined with the botnets, the ruse made it seem like millions of real people from some of the most affluent parts of the world were viewing the ads. An aphorism I often use in my talks is "expertise flows downhill: today's top-secret NSA programs become tomorrow's PhD theses and the next day's hacking tools."

Malwarebytes
MARCH 17, 2021
At first considered a reasonably dangerous threat (researchers now believe it’s a form of adware), Silver Sparrow is nevertheless a malware family of intrigue for showcasing “mature” capabilities, such as the ability to remove itself, which is usually reserved for stealth operations. Adware accounted for another 22 percent.

Malwarebytes
MAY 6, 2023
Way back in 2004, adware giants Direct Revenue went head to head in a court of law with ad company Avenue Media. The spectacularly named article “ Adware cannibals feast on each other ” describes how adware vendors thirsty for profit battled for desktop supremacy.

Malwarebytes
MAY 16, 2022
The threat actor chose to promote a legitimate security product in this case, but might as well have led visitors to potentially unwanted programs (PUPs), adware, or tech support scams. As we reported in the past, adware , search hijackers , and PUP families have added push notifications as one of their attack vectors. drakefollow[.]com

CSO Magazine
FEBRUARY 22, 2023
To read this article in full, please click here Instead, the most dangerous threats come from a set of known, mature tools and tactics that an entire ecosystem of cybercriminals rely upon to take in billions of dollars a year."

Schneier on Security
JANUARY 5, 2018
News article. Finally, based on our findings, we further develop JavaScript rewriting and API hooking based solutions (the latter implemented as a Chrome extension) to help adblockers bypass state-of-the-art anti-adblockers.

CyberSecurity Insiders
APRIL 20, 2023
In this article, we’ll explore the different types of spyware and how you can detect them on your computer. Adware- Adware is a type of spyware that displays unwanted advertisements on your computer. Adware can also track your browsing history and search queries to display ads that are more relevant to your interests.

Identity IQ
AUGUST 10, 2022
It scans your computer and other gadgets for viruses, adware and other malware you may inadvertently come across as you browse the web, download software or open email attachments. With that in mind, do you still need to buy antivirus software to protect your computer systems and data? What Does Antivirus Protection Do? .

Security Affairs
JUNE 11, 2023
Every week the best security articles from Security Affairs are free for you in your email box. A new round of the weekly SecurityAffairs newsletter arrived! Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

Security Affairs
AUGUST 13, 2023
Every week the best security articles from Security Affairs are free for you in your email box. A new round of the weekly SecurityAffairs newsletter arrived! Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

Malwarebytes
FEBRUARY 6, 2024
So in this article we’ll focus on what threats affect you directly and how you can protect yourself. Contrary to outdated beliefs, malware for Macs has always existed, it was just considered less serious since most Mac malware was adware or potentially unwanted programs (PUPs). But other threats you can do something about.

Malwarebytes
NOVEMBER 1, 2022
This follows on the heels of adware that was found on Google Play just a couple months ago from a rogue PDF reader. Our analysis of this malware starts with us finding an app named Bluetooth Auto Connect (full app information at the bottom of this article). More than just adware. Delayed ungratification.

SecureList
JULY 21, 2021
This article contains some analytical findings from Managed Detection and Response (MDR) operations during Q4 2020. Finally, Low severity is related to incidents without a significant impact, which still ought to be fixed, for example, infection with grayware, such as adware, riskware, etc. What is Kaspersky MDR. Offensive exercise.

Identity IQ
FEBRUARY 18, 2021
In this article, we’ll be covering the following topics: What are the Components of a Digital Identity? Malware is any type of software or program designed to harm a computer, steal data or hold victims to ransom such as a computer virus, Trojan horse, ransomware, spyware, wiper, worm or adware. Why is Your Digital Identity Important?

SiteLock
AUGUST 27, 2021
In this article, we’ll cover some of the most common types of malware that every website owner needs to know in order to protect their business from cyber threats, as well as how to protect you site with the right malware removal solution if your site is infected. As a website owner, chances are you’ve heard a great deal about malware.

Malwarebytes
JANUARY 28, 2021
Yet much of the bad old days of Adware/spyware from 2005 – 2008 was dependent on bad policies and leaky data sharing. This is because they claim Grindr shared user data to third parties “without legal basis”. That doesn’t sound good. What does it mean in practice? Noticing the notification. Batten down the data privacy hatches.

Trend Micro
OCTOBER 1, 2020
Linkury Adware Caught Distributing Full-Blown Malware and Cross-Platform Modular Glupteba Malware Uses ManageX.

SiteLock
AUGUST 27, 2021
Objectives include a ‘media player upgrade,’ which could be adware or worse, an exploit kit, or blackhat lead generation and survey sites promising socially desirable electronics in exchange for personal information and a nominal purchase. Malicious Redirect. End Result Of The Injected Malware.

Malwarebytes
SEPTEMBER 13, 2021
In a recent article , RiskIQ researchers unravelled a large part of the infrastructure used by Magecart Group 8 and how they migrated to different hosts in particular Flowspec and OVH over time. The RiskIQ article describes this part of the infrastructure in great details. com google-adware[.]com We will review those in Part 2.

SecureList
SEPTEMBER 24, 2024
Whether we’re browsing social media, playing video games, shopping for products, or simply reading news articles, trackers are silently monitoring our online behavior, fueling the ceaseless hum of countless data centers worldwide. However, it does not prevent websites from tracking your activities within that session.

Hacker's King
SEPTEMBER 18, 2024
In this article, we are going learn what is malware, how many types of malware and how to do analysis on malware. You may like to read more about How To Bypass Windows Password with a Bootable Pen-Drive For Free What do we discuss in this article? > In today’s digital landscape, the threat of malware is ever-present.

Spinone
DECEMBER 17, 2019
In this article, we will take a detailed look at how ransomware makes its way into your network and onto your computer and see how you can defend your data assets! Some of those fake apps steal your banking data when you try to pay for the extra functionality; others display adware or take money for scam subscriptions.

eSecurity Planet
JULY 31, 2024
Antivirus (AV) is the foundational layer of endpoint security that detects and removes dangerous software such as worms, trojans, adware, and ransomware. Kaiti Norton contributed to this article. The platform is ready to use in minutes, and annual pricing starts at $99.99 per device. What Is Antivirus Software?

Spinone
DECEMBER 23, 2019
Don’t worry, there are solutions that can make your life easier – we speak about them as a part of a strong multilayer ransomware protection strategy we talk about in this article. And yet, an antivirus program is a necessary line of defense that secures your devices from viruses, adware, worms, trojans, and others.

eSecurity Planet
JUNE 25, 2024
SWGs use signature-based and behavioral analysis techniques to proactively identify and neutralize known and developing threats, offering real-time protection against viruses, trojans, adware, and other types of malware. Drew Robb contributed to this article.

Spinone
MARCH 20, 2019
In this article, we will take a look at cyber security awareness across an SMB organization. These can include viruses, trojans, worms, spyware and adware. Why is the “human factor” an extremely important part of the security equation?

SecureList
AUGUST 12, 2021
You can read more about these vulnerabilities and their exploitation in our articles PuzzleMaker attacks with Chrome zero-day exploit chain and Zero-day vulnerability in Desktop Window Manager (CVE-2021-28310) used in the wild. As in the previous quarter, a total of 15 of the Top 20 threats for macOS are adware programs. Country*. %

eSecurity Planet
FEBRUARY 16, 2021
This article dives into the lexicon of malware, offering descriptions, protections, and examples of each. Jump ahead: Adware. As you browse the myriad of malicious software featured in this article, we offer tips for how best to defend against each type. How to Defend Against Adware. Examples of Adware Malware Attacks.

The Last Watchdog
FEBRUARY 28, 2021
This article will walk you through the various types of malware, how to identify and prevent a malware attack, and how to mitigate the risks. Malware can be categorized based on how it behaves (adware, spyware and ransomware), and how it propagates from one victim to another (viruses, worms and trojans). What is Malware .

CyberSecurity Insiders
JANUARY 31, 2021
This article will walk you through the various types of malware, how to identify and prevent a malware attack, and how to mitigate the risks. Malware can be categorized based on how it behaves (adware, spyware and ransomware), and how it propagates from one victim to another (viruses, worms and trojans). What is Malware?

Identity IQ
APRIL 29, 2021
In this article, we’ll discuss: . Adware is software designed to serve advertisements to you, either within your web browser or in other programs. Adware isn’t always bad. Some free apps, for instance, include adware as a way to make revenue from ads. Why do Cybercriminals Use Malware? How does Malware Spread?

Malwarebytes
JULY 16, 2021
The rest of this article will reference scareware programs which are intended to be malicious. Scareware is primarily used to panic or worry someone into performing a task they otherwise wouldn’t have done. There are some caveats to this, which we’ll cover below.

SecureList
NOVEMBER 23, 2021
article, we wrote that users relied on corporate laptops to play video games, watch movies and use e-learning platforms. That was the case with the latest James Bond film, No Time to Die, with cybercriminals using adware, Trojans and ransomware to steal private information and even blackmailing victims who wanted their data back.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?



Let's personalize your content