Facebook, Instagram, TikTok and Twitter Target Resellers of Hacked Accounts
Krebs on Security
FEBRUARY 4, 2021
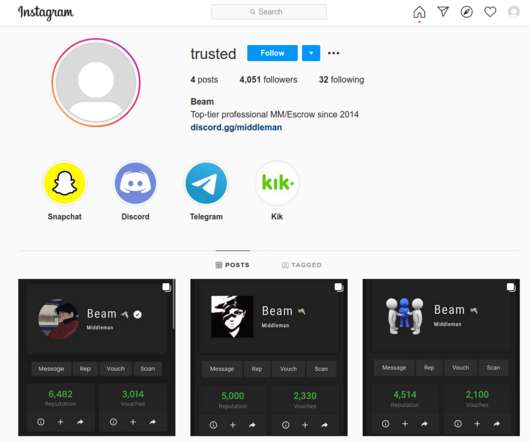
Facebook told KrebsOnSecurity it seized hundreds of accounts — mainly on Instagram — that have been stolen from legitimate users through a variety of intimidation and harassment tactics, including hacking, coercion, extortion, sextortion , SIM swapping , and swatting. THE MIDDLEMEN.


























Let's personalize your content