Cybercrime group FIN7 advertises new EDR bypass tool on hacking forums
Security Affairs
JULY 18, 2024
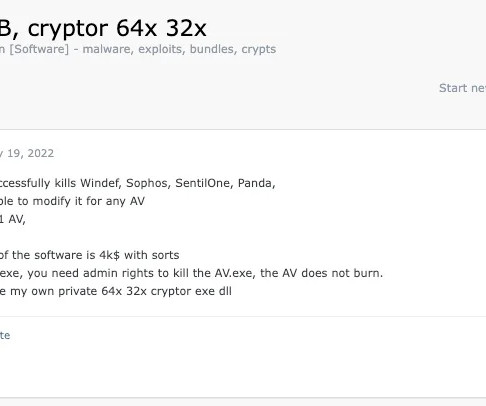
The cybercrime group FIN7 is advertising a security evasion tool in multiple underground forums, cybersecurity company SentinelOne warns. SentinelOne researchers warn that the financially motivated group FIN7 is using multiple pseudonyms to advertise a security evasion tool in several criminal underground forums.


















Let's personalize your content