China-based SMS Phishing Triad Pivots to Banks
Krebs on Security
APRIL 10, 2025
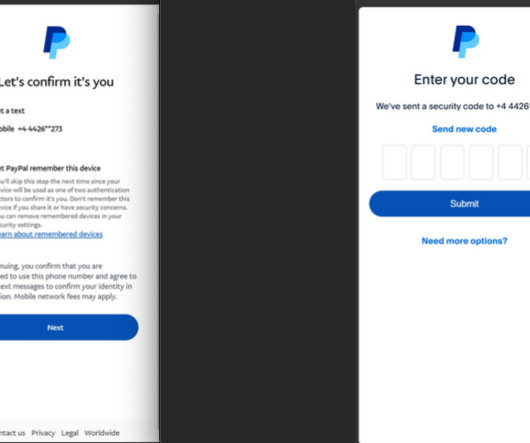
Thus, the missives bypass the mobile phone networks entirely and enjoy near 100 percent delivery rate (at least until Apple and Google suspend the spammy accounts). Phishers using multiple virtualized Android devices to orchestrate and distribute RCS-based scam campaigns. Image: Prodaft.




























Let's personalize your content