RSAC insights: Introducing ‘CWPP’ and ‘CSPM,’ new frameworks to secure cloud infrastructure
The Last Watchdog
MAY 17, 2021
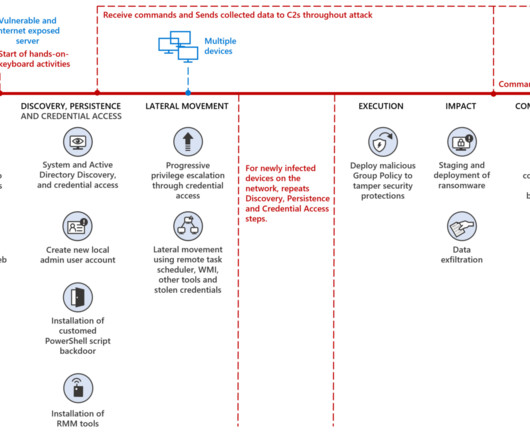
Related: How credential stuffing fuels account takeovers. In pulling off that milestone hack, Paige Thompson took advantage of CapOne’s lack of focus on cloud security as the banking giant rushed headlong into leveraging Amazon Web Services. Hunting vulnerabilities.









































Let's personalize your content