DDoS Mitigation Firm Founder Admits to DDoS
Krebs on Security
JANUARY 20, 2020
DDoS attacks involve flooding a target Web site with so much junk Internet traffic that it can no longer accommodate legitimate visitors.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Krebs on Security
JANUARY 20, 2020
DDoS attacks involve flooding a target Web site with so much junk Internet traffic that it can no longer accommodate legitimate visitors.

The Last Watchdog
JUNE 23, 2021
These hacking waves contribute to the harvesting of account credentials and unauthorized access to loosely-configured servers; and these ill-gotten assets can, in turn, be utilized to execute different stages of higher-level hacks, such as account takeovers and ransomware campaigns. These are simple steps to take,” he told me.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Krebs on Security
NOVEMBER 8, 2021
If it sounds unlikely that a normal Internet user could make millions of dollars unmasking the identities of REvil gang members, take heart and consider that the two men indicted as part this law enforcement action do not appear to have done much to separate their cybercriminal identities from their real-life selves. 3 was Lublin, Poland.

Security Affairs
FEBRUARY 12, 2021
Russian internet and search company Yandex discloses a data breach, a system administrator was selling access to thousands of user mailboxes. The employee was one of three system administrators with the necessary access rights to provide technical support for the service.

Krebs on Security
JULY 14, 2020
. “DNS is a foundational networking component and commonly installed on Domain Controllers, so a compromise could lead to significant service interruptions and the compromise of high level domain accounts.”
Krebs on Security
MAY 13, 2024
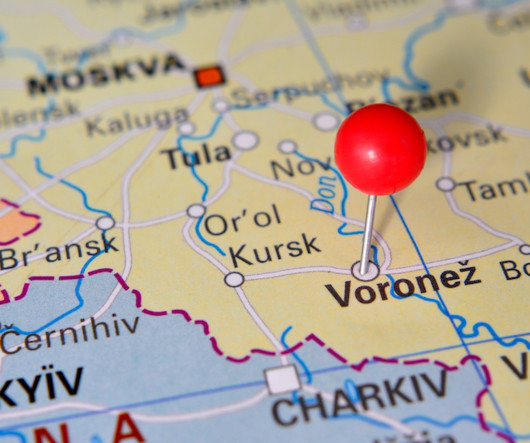
According to Constella, this email address was used in 2010 to register an account for a Dmitry Yurievich Khoroshev from Voronezh, Russia at the hosting provider firstvds.ru. 2011 said he was a system administrator and C++ coder. NeroWolfe seems to have abandoned all of his forum accounts sometime in 2016. “P.S.

Krebs on Security
SEPTEMBER 30, 2023
“The command requires Windows system administrators,” Truniger’s ads explained. Semen-7907 registered at Tunngle from the Internet address 31.192.175[.]63 was also used to register an account at the online game stalker[.]so ru account and posted as him. ru account was used without his permission.
Krebs on Security
JANUARY 7, 2020
Late last year saw the re-emergence of a nasty phishing tactic that allows the attacker to gain full access to a user’s data stored in the cloud without actually stealing the account password. com — is different from the one I saw in late December, but it was hosted at the same Internet address as officesuited[.]com
Krebs on Security
JUNE 9, 2020
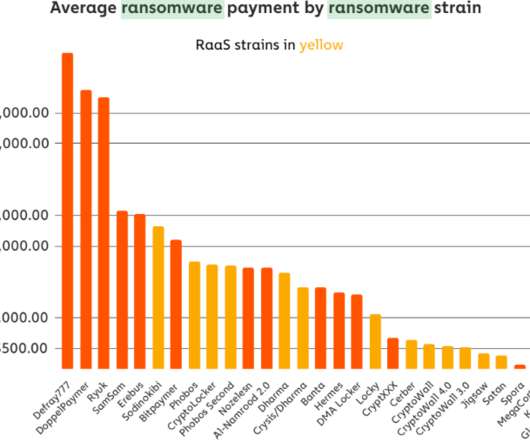
City officials now say they plan to pay the ransom demand, in hopes of keeping the personal data of their citizens off of the Internet. Nevertheless, on Friday, June 5, the intruders sprang their attack, deploying ransomware and demanding nearly $300,000 worth of bitcoin.

SecureList
DECEMBER 9, 2024
was used by tens of millions of websites approximately 4% of all sites on the internet which highlights the severity of the incident, whose full impact is yet to be determined. It is a critical tool in various fields, including system administration, development, and cybersecurity. Why does it matter?

The Last Watchdog
MARCH 4, 2019
For instance, major vulnerability was discovered lurking in the GNU C Library, or GLIBC, an open source component that runs deep inside of Linux operating systems used widely in enterprise settings. GLIBC keeps common code in one place, thus making it easier for multiple programs to connect to the company network and to the Internet.

Hot for Security
FEBRUARY 16, 2021
Yandex is an Internet company that provides users with a suite of products like Internet browsers for all major platforms, a search engine, an ad platform and an email service. It turns out that one of the three people working support for the email service, with access to people’s email accounts, used that power for profit.

Security Affairs
AUGUST 9, 2021
The Taiwanese company urges its customers to enable multi-factor authentication where available, enable auto block and account protection, and to use string administrative credentials, . System administrators that have noticed suspicious activity on their devices should report it to Synology technical support.

The Last Watchdog
JUNE 2, 2021
PKI is the authentication and encryption framework on which the Internet is built. It works by issuing digital certificates to verify the authenticity of the servers ingesting the data trickling in from our smartphones, Internet of Things sensors and the like. And threat actors have become adept at account takeovers.

Malwarebytes
JULY 29, 2021
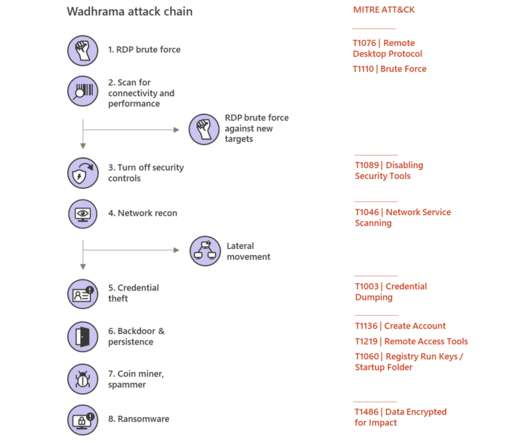
The attack could force remote Windows systems to reveal password hashes that could then be easily cracked. Microsoft quickly sent out an advisory for system administrators to stop using the now deprecated Windows NT LAN Manager (NTLM) to thwart an attack. PetitPotam. ” New mitigation details.
Security Affairs
MARCH 10, 2020
“They exhibit extensive knowledge of systems administration and common network security misconfigurations, perform thorough reconnaissance, and adapt to what they discover in a compromised network.” ” reads the post published by Microsoft. ” continues Microsoft.

Security Affairs
JUNE 8, 2022
. “Upon gaining an initial foothold into a telecommunications organization or network service provider, PRC state-sponsored cyber actors have identified critical users and infrastructure including systems critical to maintaining the security of authentication, authorization, and accounting.
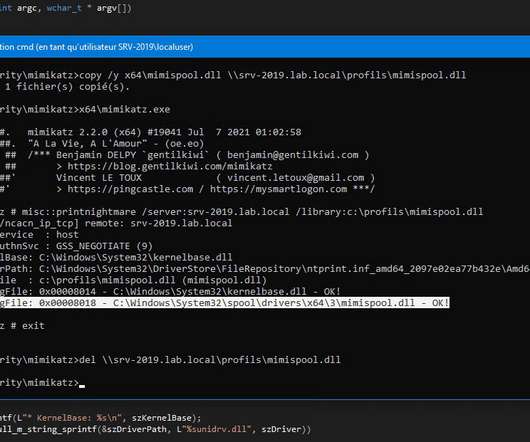
eSecurity Planet
MARCH 21, 2022
Inactive Accounts and Default Configurations. Hackers gained initial access by brute-forcing an existing account via “a simple, predictable password” to enroll a new device in the MFA procedures, the agencies said. MFA was automatically disabled because the account was inactive for a long period.

Security Affairs
AUGUST 19, 2019
Webmin is an open-source web-based interface for system administration for Linux and Unix. It allows users using web browsers to set up user accounts, Apache, DNS, file sharing and much more. Webmin, the popular open-source web-based interface for Unix admin contained a remote code execution vulnerability for more than a year.

Security Affairs
NOVEMBER 21, 2019
The Roboto botnet spreads by compromising systems by exploiting the Webmin RCE vulnerability tracked as CVE-2019-15107 to drop its downloader module on Linux servers running vulnerable installs. Webmin is an open-source web-based interface for system administration for Linux and Unix.

SecureList
OCTOBER 13, 2022
In addition, manual mitigation steps can be undertaken by system administrators to prevent successful exploitation (see below). Performing disinfection on Zimbra is extremely difficult, as the attacker will have had access to configuration files containing passwords used by various service accounts.

Webroot
APRIL 2, 2024
While RDP is a powerful tool for remote administration and support, it has also become a favored vector for brute force attacks for several reasons: Widespread use: RDP is commonly used in businesses to enable remote work and system administration.

Security Affairs
MARCH 1, 2019
According to an investigation conducted by Secureworks hackers were also able to access the hackers were also able to compromise the mail servers to obtain access to admin accounts. The hackers scan the Internet for vulnerable servers that could lead to compromising valuable targets. “In “ reports Radio-Canada.

SecureList
OCTOBER 20, 2021
Many used browsers that they were accustomed to, not browsers of choice, or default browsers set by organizations, such as the Internet Explorer. It could be compromised directly or by hacking the account of someone with access to the website management. These services, too, have been outsourced.

SecureWorld News
SEPTEMBER 15, 2020
Between January and August 2020, unidentified actors used aggregation software to link actor-controlled accounts to client accounts belonging to the same institution, resulting in more than $3.5 Some of the credentials belonged to company leadership, system administrators, and other employees with privileged access.".

Thales Cloud Protection & Licensing
OCTOBER 15, 2019
And, according to eMazzanti Technologies , “Often, information technology (IT) accounts for less than 0.1% Atlanta , Baltimore , Port of San Diego , and the island of Saint Maarten were subjected to wide scale cyber-attacks affecting vital government services and costing these municipalities millions of dollars.

eSecurity Planet
JULY 15, 2024
These include sending a malicious file that requires user execution and.URL files that route users to risky websites via Internet Explorer. This vulnerability affects all standards-compliant RADIUS clients and servers, putting enterprises that send RADIUS packets over the internet especially at risk.

eSecurity Planet
SEPTEMBER 11, 2023
9 Security Flaws Discovered in Schweitzer Power Management Products Type of attack: The security threats associated with the flaws in Schweitzer Engineering Laboratories (SEL) power management devices include remote code execution, arbitrary code execution, access to administrator rights, and watering hole attacks.

eSecurity Planet
MARCH 25, 2022
Also read : Best Internet Security Suites & Software. A few days later, IT systems started malfunctioning with ransom messages following. The system administrator did not configure standard security controls when installing the server in question. Defending Against RDP Attacks: Best Practices.

SecureList
MARCH 12, 2024
During one of the projects, an SQL injection into an application that was open to signup by any internet user let us obtain the credentials of an internal system administrator. One-Time Passwords and authentication against various resources, such as accounts or file systems, were some of the mechanisms we found to be vulnerable.

eSecurity Planet
JULY 6, 2021
Kaseya’s flagship product is a remote monitoring and management (RMM) solution called the Virtual Systems Administrator (VSA) and is the product at the center of the current attack. When administrators noticed suspicious behavior on Friday, Kaseya shut down VSA. VSA server breached. Backup data regularly.

Security Boulevard
FEBRUARY 10, 2022
The Morris Worm, ostensibly created to map the internet, ultimately brought down roughly 6000 systems. Early Internet. As the ARPANET evolved into the internet, connecting exponentially more computers throughout the world, malicious code likewise made advances. a trusted vendor.

Malwarebytes
JULY 1, 2021
For the systems that do need the Print Spooler service to be running make sure they are not exposed to the internet. Please note that stopping the service without disabling may not be enough. I realize the above will not be easy or even feasible in every case.

Herjavec Group
OCTOBER 30, 2020
Ask your school system administrators to provide you their written cybersecurity policies and procedures concerning proposed remote learning capabilities. Ask your school system administrators to provide a copy of their incident response policies and plans. School Systems and Educators. So, what to do?

Security Boulevard
DECEMBER 2, 2022
In most organization system administrators can disable or change most or all SSH configurations; these settings and configurations can significantly increase or reduce SSH security risks. Disabling root account remote login - This prevents users from logging in as the root (super user) account. Very useful.

IT Security Guru
JANUARY 12, 2021
IoT (Internet of Things) Security. System Administrator (or, sysadmin). As a CBO at Ampcus Cyber, Viral overlooks the go-to-market Strategy, channel partner programs, strategic accounts, and customer relationship management. Secure Software Development. Secure DevOps. Web/Mobile Application security.

SecureWorld News
DECEMBER 11, 2023
Additionally, digital trust involves several interconnected elements, including: • Security of Systems and Data • Privacy of Data • Transparency of Operation • Accountability when things go wrong • Reliability But why is digital trust suddenly important? What are the origins of the need for a trust framework?

NopSec
MARCH 16, 2020
Are all Microsoft(MS) Remote Desktop connections to the outside world accounted for and adequately protected? Are all the OWA – Outlook Web Access – installations accounted for and adequately protected? Are all file sharing accounts accounted for and adequately protected? Are all CMS websites accounted for?

McAfee
OCTOBER 4, 2021
It wasn’t until I started college that I started to dig deeper into operating systems, networking, and lower-level languages like C. I started to learn more about how the Internet worked and one thing led to the other. And if you need more help or advice, don’t hesitate to contact me on my Twitter account: @aboutsecurity.

eSecurity Planet
MAY 19, 2022
This cloud-centric model offers administrators granular network management opportunities while leveraging the bandwidth and reducing the cost of service delivery. With SD-WAN architectures, branch employees and remote users connect to an enterprise network through a web of connected devices over the internet. SDN vs SD-WAN.
Security Boulevard
JUNE 20, 2022
Historically, Microsoft recommended using the Enhanced Security Admin Environment (ESAE) architecture to provide a secure environment for AD administrators to prevent full compromise of a production forest in case of compromise of non-admin users. They recommend tiered administration with dedicated admin accounts.

SecureList
OCTOBER 12, 2023
PHYSICALDRIVE0" get model,name,SerialNumber >> c:userspublicd Get systeminfo cmd /c start /b systeminfo >> c:userspublicd Check current TCP ports status cmd /c netstat -anop tcp >> c:userspublicd Test internet connection cmd /c ping 8.8.8.8 -n SCRIPT_NAME%.ps1
Digital Shadows
AUGUST 17, 2021
The targeted phishing is going after folks in HR using fake but malicious resumes or payroll and accounts receivable teams to move legitimate payment accounts into attacker control. A compromised customer account might use business email compromise tactics to phish everyone in that customer’s circle.

eSecurity Planet
JULY 20, 2023
Develop and implement suitable remediation procedures in collaboration with key stakeholders such as system administrators, network engineers, and security teams. Cloud scanners use internet connection to scan multiple networks at the pace of available bandwidth, making them more flexible and scalable.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content