Cybersecurity Training Agency Breached After Phishing Attack
Adam Levin
AUGUST 13, 2020
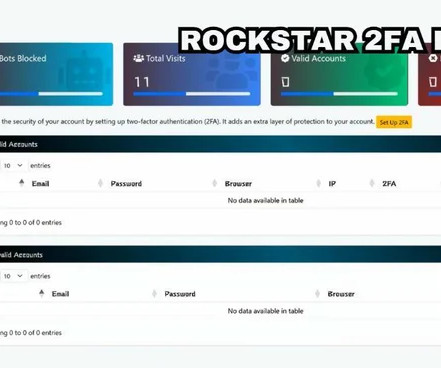
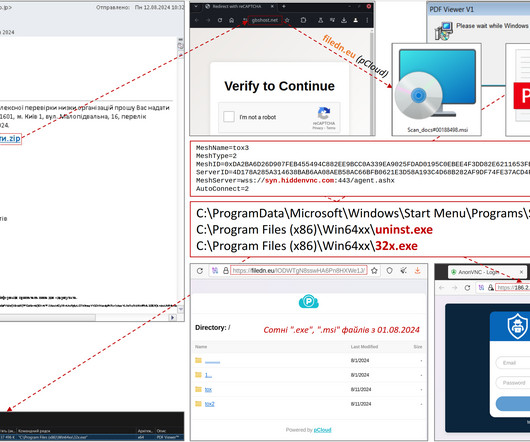
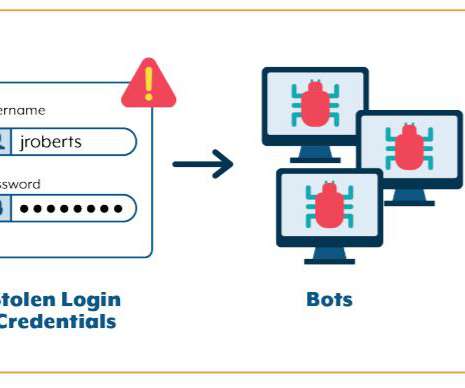
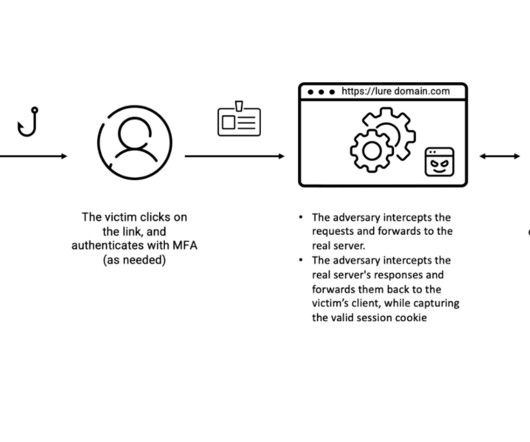
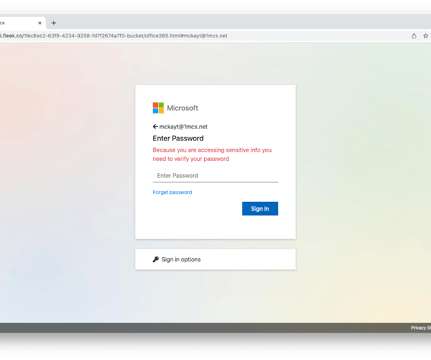
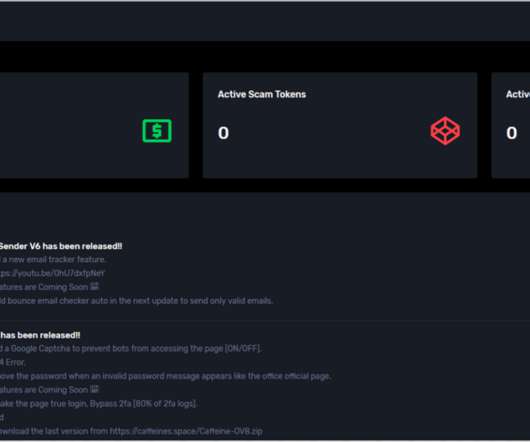
The breach has been traced back to a phishing attack that targeted an employee of the company. As a result, approximately 28,000 records of PII were forwarded to a suspicious external email address,” the company stated, adding that they have “have identified a single phishing e-mail as the vector of the attack.”.



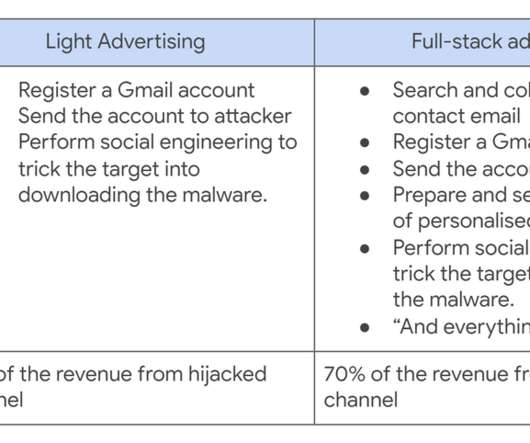
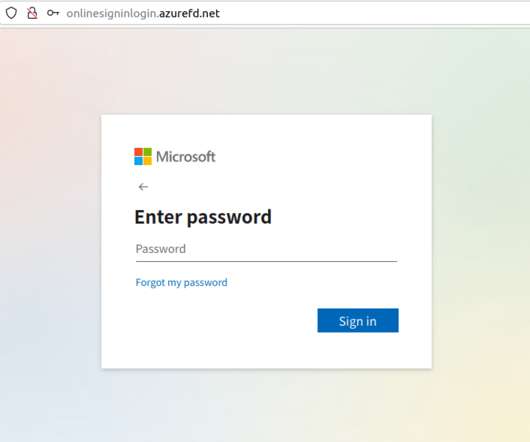




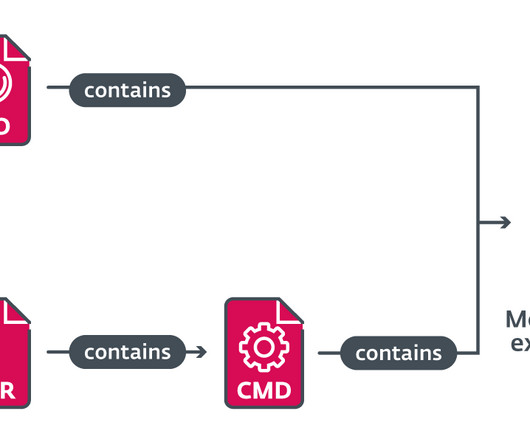
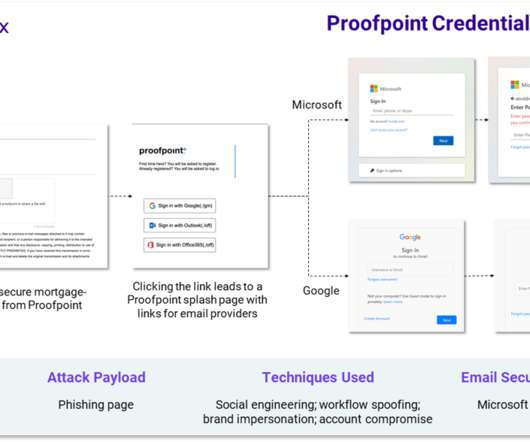



















Let's personalize your content