Would You Have Fallen for This Phone Scam?
Krebs on Security
APRIL 28, 2020
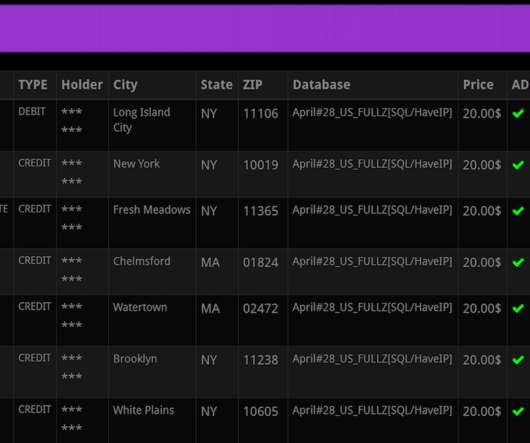
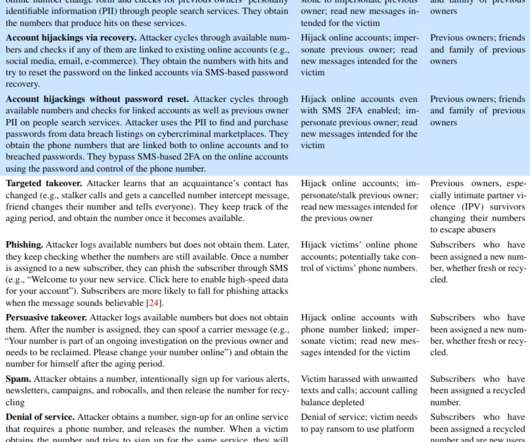
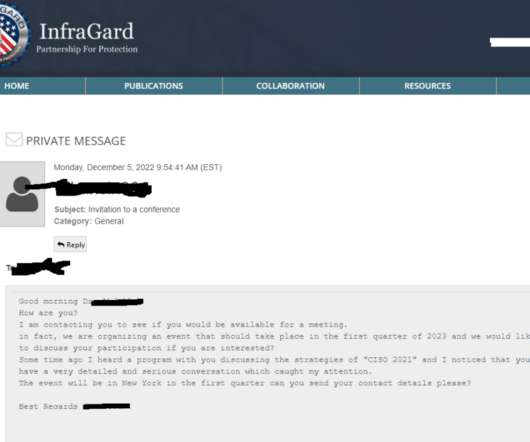
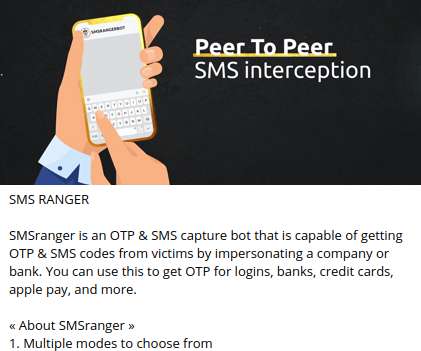
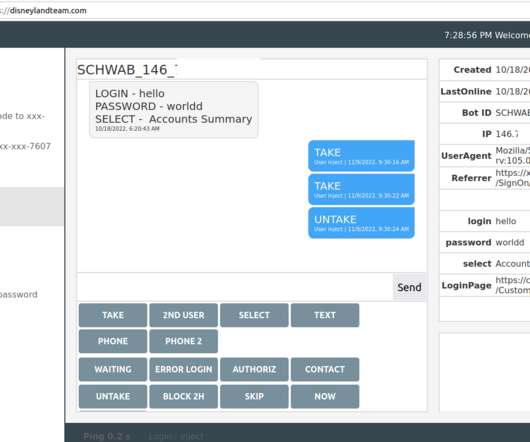
You may have heard that today’s phone fraudsters like to use use caller ID spoofing services to make their scam calls seem more believable. “After we figured out what was going on, we were left asking ourselves how the crooks had obtained her last three transactions without breaking into her account online. .











Let's personalize your content