FBI: Spike in Hacked Police Emails, Fake Subpoenas
Krebs on Security
NOVEMBER 9, 2024
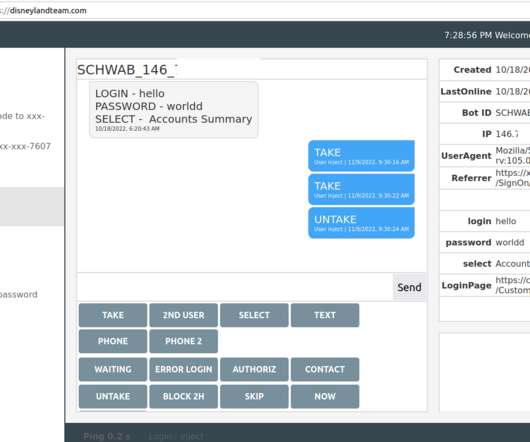
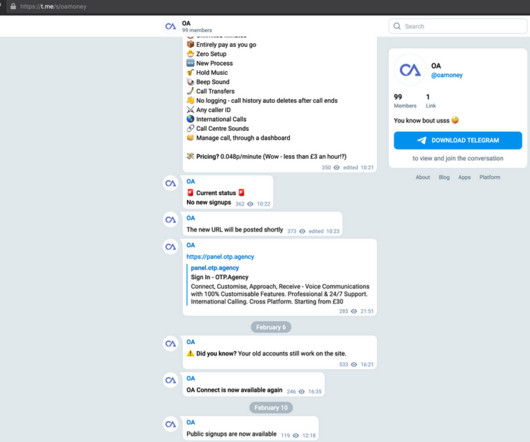
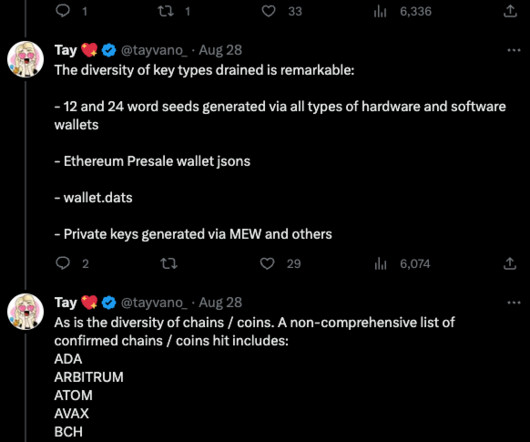
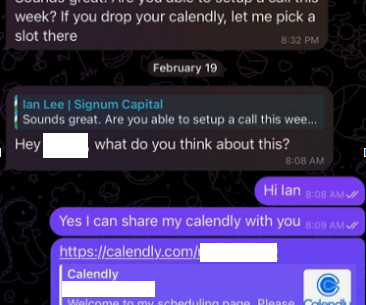
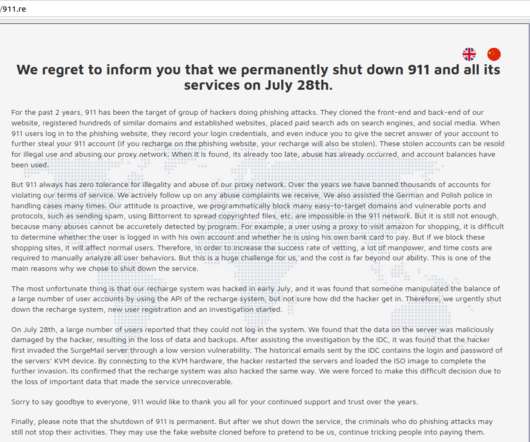
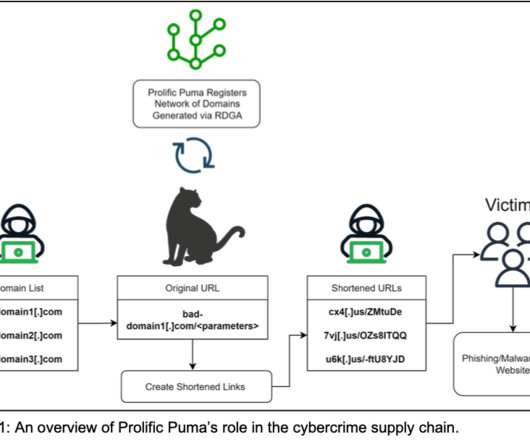
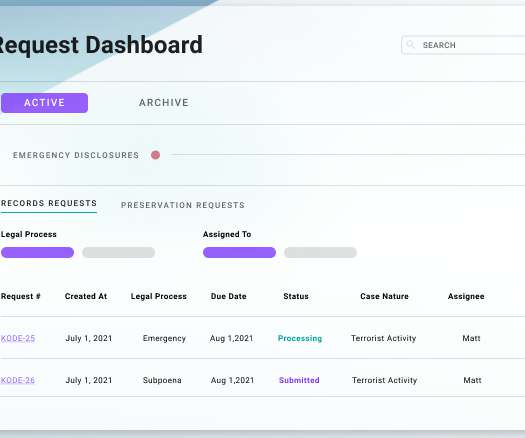
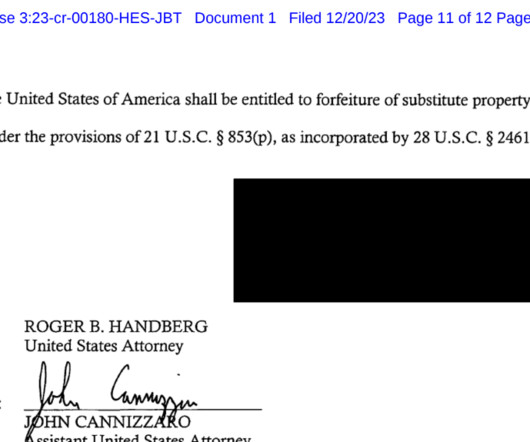
The Federal Bureau of Investigation (FBI) is urging police departments and governments worldwide to beef up security around their email systems, citing a recent increase in cybercriminal services that use hacked police email accounts to send unauthorized subpoenas and customer data requests to U.S.-based based technology companies.



















Let's personalize your content