How Coinbase Phishers Steal One-Time Passwords
Krebs on Security
OCTOBER 13, 2021
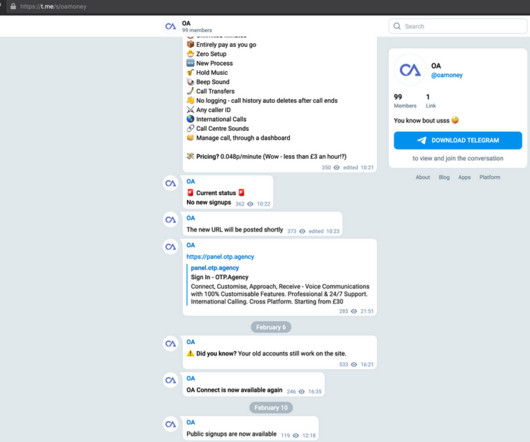
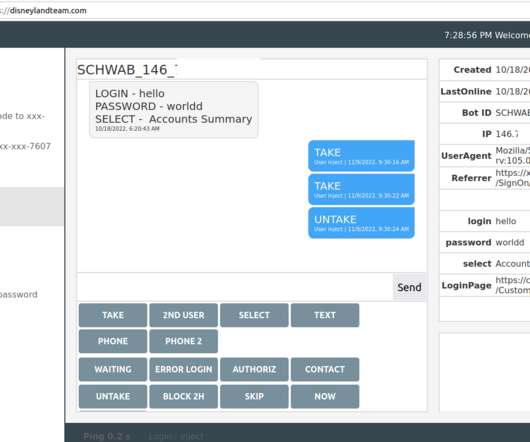
A recent phishing campaign targeting Coinbase users shows thieves are getting cleverer about phishing one-time passwords (OTPs) needed to complete the login process. In each case, the phishers manually would push a button that caused the phishing site to ask visitors for more information, such as the one-time password from their mobile app.
















Let's personalize your content