New 'VietCredCare' Stealer Targeting Facebook Advertisers in Vietnam
The Hacker News
FEBRUARY 21, 2024
Facebook advertisers in Vietnam are the target of a previously unknown information stealer dubbed VietCredCare at least since August 2022.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

The Hacker News
FEBRUARY 21, 2024
Facebook advertisers in Vietnam are the target of a previously unknown information stealer dubbed VietCredCare at least since August 2022.

Schneier on Security
NOVEMBER 3, 2021
It turns out that it’s surprisingly easy to create a fake Harvard student and get a harvard.edu email account. They also said that the scammers were creating the fake accounts by signing up for online classes and then using the email address that process provided to infiltrate the university’s various blogging platforms.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
JUNE 30, 2021
Facebook has filed lawsuits against two groups of suspects who took over advertising agency employees' accounts and abused its ad platform to run unauthorized or deceptive ads. [.].

The Hacker News
MARCH 13, 2023
A fake ChatGPT-branded Chrome browser extension has been found to come with capabilities to hijack Facebook accounts and create rogue admin accounts, highlighting one of the different methods cyber criminals are using to distribute malware. "By

Schneier on Security
OCTOBER 2, 2018
From Kashmir Hill : Facebook is not content to use the contact information you willingly put into your Facebook profile for advertising. This means that the junk email address that you hand over for discounts or for shady online shopping is likely associated with your account and being used to target you with ads.

Security Affairs
JANUARY 4, 2024
The X account of cybersecurity giant Mandiant was hacked, attackers used it to impersonate the Phantom crypto wallet and push a cryptocurrency scam. Crooks hacked the X account of cybersecurity firm Mandiant and used it to impersonate the Phantom crypto platform and share a cryptocurrency scam. “Sorry, change password please.”

Heimadal Security
JULY 1, 2021
Facebook is suing the suspects that took over the advertising agency employees’ accounts and managed to abuse the ad platform in order to run unauthorized or deceptive ads. The post Facebook Is Suing the Hackers That Hijacked Advertising Agencies’ Accounts appeared first on Heimdal Security Blog.

Krebs on Security
DECEMBER 2, 2020
For at least the third time in its existence, OGUsers — a forum overrun with people looking to buy, sell and trade access to compromised social media accounts — has been hacked. An offer by the apparent hackers of OGUsers, offering to remove account information from the eventual database leak in exchange for payment.
Security Affairs
NOVEMBER 11, 2020
?Ragnar Locker Ransomware operators have started to run Facebook advertisements to force their victims into paying the ransom. Ragnar Locker Ransomware operators are improving their extortion technique and started running Facebook advertisements to make pressure on their victims and force them to pay the ransom. 9, on Facebook. .

Krebs on Security
FEBRUARY 4, 2021
Facebook, Instagram , TikTok , and Twitter this week all took steps to crack down on users involved in trafficking hijacked user accounts across their platforms. Facebook said it targeted a number of accounts tied to key sellers on OGUsers, as well as those who advertise the ability to broker stolen account sales.

Krebs on Security
MARCH 10, 2020
FBI officials last week arrested a Russian computer security researcher on suspicion of operating deer.io , a vast marketplace for buying and selling stolen account credentials for thousands of popular online services and stores. also is a favored marketplace for people involved in selling phony social media accounts.

Malwarebytes
APRIL 6, 2023
After Meta (Facebook and Instagram) switched the legal basis for targeting advertising from automatic consent to opt-out, privacy watchdog noyb has built a tool for users to opt out of targeted advertising and various other claims made by Meta in an easy and legally sound way. Next you are presented with three options.

Security Affairs
JANUARY 4, 2024
An internet outage impacted Orange Spain after a hacker gained access to the company’s RIPE account to misconfigure BGP routing. The hacker, who uses the moniker ‘Snow’, gained access to the RIPE account of Orange Spain and misconfigured the BGP routing causing an internet outage. I have fixed your RIPE admin account security.
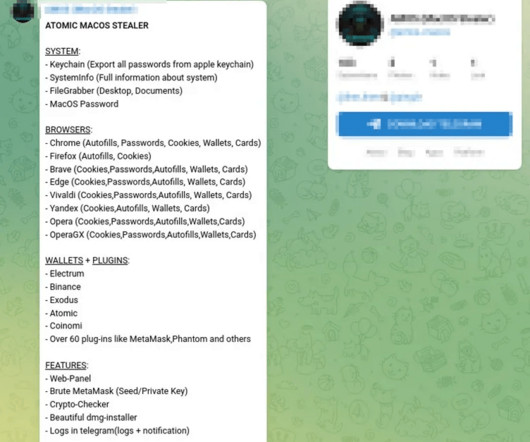
Security Affairs
APRIL 29, 2023
Atomic macOS Stealer is a new information stealer targeting macOS that is advertised on Telegram for $1,000 per month. Cyble Research and Intelligence Labs (CRIL) recently discovered a Telegram channel advertising a new information-stealing malware, named Atomic macOS Stealer (AMOS).

Malwarebytes
SEPTEMBER 1, 2023
Not long ago I wrote about a recent campaign to hold LinkedIn users' accounts to ransom. Since he doesn’t use the LinkedIn app on his mobile he checked his account on his laptop first thing in the morning. A reset of the account’s password worked, but failed to remove the unwanted active session.

Graham Cluley
JUNE 5, 2023
Twitter awarded "gold checkmark" to unofficial Disney Twitter account which posted racial slurs. Is it any wonder that Twitter's ad sales in the United Sales have plunged 59% in the past year?

Krebs on Security
MARCH 13, 2019
Online advertising firm Sizmek Inc. [ NASDAQ: SZMK ] says it is investigating a security incident in which a hacker was reselling access to a user account with the ability to modify ads and analytics for a number of big-name advertisers. The starting bid was $800. A screenshot shared by the dark web seller.

Malwarebytes
DECEMBER 16, 2021
million fine by Norwegian regulator Datatilsynet for sharing data with advertisers. Grindr disclosed information about a user’s GPS location, IP address, mobile phone advertising ID, age and gender to several third parties for marketing purposes. Dating network Grindr has been slapped with a US$7.7 No consent, no app. Shared data.

Bleeping Computer
JULY 26, 2022
A new phishing campaign codenamed 'Ducktail' is underway, targeting professionals on LinkedIn to take over Facebook business accounts that manage advertising for the company. [.].

Security Boulevard
APRIL 25, 2021
to restrict tracking by advertisers, and a discussion about why people continue to choose terrible passwords. ** Links mentioned on the show ** Instagram debuts new tool to stop abusive message salvos made through new accounts [link] Apple […].

Krebs on Security
JANUARY 25, 2024
And by most accounts, the threat from bad ads leading to backdoored software has subsided significantly compared to a year ago. “We’ve reviewed the ads in question, removed those that violated our policies, and suspended the associated accounts. million advertiser accounts. Google says it removed 5.2

Bleeping Computer
NOVEMBER 23, 2022
A cybercriminal operation tracked as Ducktail has been hijacking Facebook Business accounts causing losses of up to $600,000 in advertising credits. [.].

The Hacker News
JULY 27, 2022
Facebook business and advertising accounts are at the receiving end of an ongoing campaign dubbed Ducktail designed to seize control as part of a financially driven cybercriminal operation. "The

The Hacker News
SEPTEMBER 4, 2023
Malicious actors associated with the Vietnamese cybercrime ecosystem are leveraging advertising-as-a-vector on social media platforms such as Meta-owned Facebook to distribute malware.

Security Affairs
NOVEMBER 1, 2020
A threat actor is offering for sale account databases containing an aggregate total of 34 million user records stolen from 17 companies. A data breach broker is selling account databases containing a total of 34 million user records stolen from 17 companies. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->.

Security Affairs
AUGUST 9, 2023
Cloud account takeover scheme utilizing EvilProxy hit over 100 top-level executives of global organizations EvilProxy was observed sending 120,000 phishing emails to over a hundred organizations to steal Microsoft 365 accounts. Proofpoint noticed a worrisome surge of successful cloud account compromises in the past five months.

Security Affairs
JULY 24, 2022
million Twitter accounts that were obtained by exploiting a now-fixed vulnerability in the popular social media platform. The bug exists due to the proccess of authorization used in the Android Client of Twitter, specifically in the procces of checking the duplication of a Twitter account.” Threat actor leaked data of 5.4

The Hacker News
NOVEMBER 30, 2022
A malicious Android SMS application discovered on the Google Play Store has been found to stealthily harvest text messages with the goal of creating accounts on a wide range of platforms like Facebook, Google, and WhatsApp.

Bleeping Computer
FEBRUARY 7, 2024
A new password-stealing malware named Ov3r_Stealer is spreading through fake job advertisements on Facebook, aiming to steal account credentials and cryptocurrency. [.]

Tech Republic Security
SEPTEMBER 25, 2020
As part of the announcement, Facebook also details account followers and advertising spending pertaining to these efforts. These campaigns used tailored messages to target audiences around the globe.

Security Affairs
APRIL 13, 2020
Zoom accounts are flooding the dark web, over 500 hundred thousand Zoom accounts are being sold on hacker forums. Over 500 hundred thousand Zoom accounts are available for sale on the dark web and hacker forums. Sellers are advertising them for.0020 Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->.

Krebs on Security
MARCH 20, 2023
Image: Shutterstock Telecommunications giant AT&T disclosed this month that a breach at a marketing vendor exposed certain account information for nine million customers. AT&T’s disclosure said the information exposed included customer first name, wireless account number, wireless phone number and email address.

Adam Levin
DECEMBER 31, 2018
Since you almost certainly missed the memo (because there was never a public one), demographic data is gleaned from your browsing history and paired with your social media accounts to form a working biography of your likes and dislikes. Online advertising is a data free-for-all. It knows what worked and why.

Malwarebytes
JULY 11, 2023
Like all social media platforms, Facebook constantly has to deal with fake accounts, scams and malware. In the past few weeks, there's been a resurgence in sponsored posts and accounts that impersonate Meta/Facebook's own Ads Manager. In early June, we identified fraudulent accounts running the same scam using similar lures.

Security Affairs
SEPTEMBER 3, 2020
The Twitter account of the Indian Prime Minister Modi was hacked, attackers sent a series of tweets asking followers to donate cryptocurrency to a relief fund. The Twitter account for the personal website of the Indian Prime Minister Narendra Modi (@ narendramodi_in ) has been hacked. “We are actively investigating the situation.

Security Affairs
AUGUST 17, 2020
The Treasury Board of Canada Secretariat confirmed that thousands of user accounts for online Canadian government services were recently hacked. According to a press release issued by the Treasury Board of Canada Secretariat, thousands of user accounts for online government services were recently hacked. ” reported CBA.

Security Affairs
APRIL 14, 2020
The details of around four million users are now being shared for free on underground hacking forums, according to ZDNet that has obtained samples from different sources, exposed records include usernames, email addresses, and hashed account passwords (bcrypt hashing algorithm). ” reported ZDNet. Pierluigi Paganini.

Security Affairs
MARCH 13, 2020
Experts discovered an Android Trojan, dubbed Cookiethief , that is able to gain root access on infected devices and hijack Facebook accounts. “This way, a cybercriminal armed with a cookie can pass himself off as the unsuspecting victim and use the latter’s account for personal gain.”. How can stealing cookies be dangerous?

Security Affairs
OCTOBER 1, 2020
Twitter removed around 130 Iranian accounts for attempting to disrupt the public recent US Presidential Debate. The social media giant Twitter announced to have removed around 130 Iranian Twitter accounts that attempted to disrupt the public conversation during the recent first Presidential Debate for the US 2020 Presidential Election.

Security Affairs
FEBRUARY 8, 2020
The social network giant Facebook is still the target of hackers, its Facebook and Instagram accounts have been hijacked by the popular hacking group Our M ine. Yesterdat the popular hacking group OurMine hacked the Twitter and Instagram accounts for Facebook and Messenger. The company accounts have been quickly restored.

Security Affairs
MAY 5, 2020
GoDaddy has been notifying its customers of a data breach, threat actors might have compromised their web hosting account credentials. GoDaddy has been notifying its customers of a data breach, attackers might have compromised users’ web hosting account credentials. ” reads the data breach notice submitted by the company.

Security Affairs
MAY 6, 2020
Hackers have breached the online learning platform Unacademy and are selling the account information for close to 22 million users. Online learning platform Unacademy has suffered a data breach after a hacker gained access to their database and started selling the account information for close to 22 million users. Pierluigi Paganini.

Security Affairs
SEPTEMBER 29, 2018
The worst suspect is a disconcerting reality, Facebook admitted that advertisers were able to access phone numbers of its users for enhanced security. Researchers from two American universities discovered that that phone numbers given to Facebook for two-factor authentication were also used for advertising purposes. Pierluigi Paganini.

Security Boulevard
JUNE 22, 2023
Getting a Facebook post, profile, or page taken down because it impersonates your brand and could lead to the defrauding of your customers can seem like… The post How to Delete Fake Facebook Accounts that Impersonate your Brand appeared first on Security Boulevard.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content