Weekly Update 369
Troy Hunt
OCTOBER 14, 2023
here's a blog post about how stupid class actions like this are! Protect your identity now.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Troy Hunt
OCTOBER 14, 2023
here's a blog post about how stupid class actions like this are! Protect your identity now.

Heimadal Security
JANUARY 9, 2023
An unauthorized entity has been detected suspiciously using your account. The post Air France and KLM Alert Customers of Account Security Breach: What You Need to Know appeared first on Heimdal Security Blog. As a result, we have […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
JULY 24, 2024
Reading Time: 5 min Have you received a microsoft account security alert email? Learn how to identify legitimate alerts and avoid phishing scams targeting your Microsoft account. The post Microsoft Account Security Alert Email: Recognize the Scam appeared first on Security Boulevard.

IT Security Guru
FEBRUARY 25, 2025
In this blog, well look at the concept of MFA fatigue, how bad actors exploit it, and what entities can do to strengthen defences against this cunning tactic. Cyber crooks often bank on organisations thinking of MFA as a silver bullet for account security, but it isnt.

Security Boulevard
DECEMBER 30, 2024
Reading Time: 5 min Have you received a microsoft account security alert email? Learn how to identify legitimate alerts and avoid phishing scams targeting your Microsoft account. The post Best of 2024: Microsoft Account Security Alert Email: Recognize the Scam appeared first on Security Boulevard.

Security Boulevard
JULY 9, 2021
This week let’s go back to security basics with password hygiene—the simplest, and yet often overlooked step in account security. The post Five worthy reads: Password hygiene – The first step towards improved security appeared first on ManageEngine Blog. Passwords ….

Graham Cluley
JULY 27, 2021
Twitter has revealed that the vast majority of its users have ignored advice to protect their accounts with two-factor authentication (2FA) - one of the simplest ways to harden account security. Read more in my article on the Hot for Security blog.
Security Affairs
JUNE 5, 2022
On April 25th, BAYC was hit the victim of another phishing attack, threat actors compromised its Instagram account and stole 91 NFTs, equivalent to $1,345,472.34. At this time it is unclear how the attackers have hacked the community manager’s account. Follow me on Twitter: @securityaffairs and Facebook. Pierluigi Paganini.
Anton on Security
NOVEMBER 2, 2023
This is my completely informal, uncertified, unreviewed and otherwise completely unofficial blog inspired by my reading of our eighth Threat Horizons Report ( full version ) that we just released ( the official blog for #1 report , my unofficial blogs for #2 , #3 , #4 , #5 , #6 and #7 ). as usual, shocking but not surprising.

Duo's Security Blog
MAY 21, 2024
Often the first step for an attacker with stolen credentials is to try to fraudulently register an MFA device , giving persistent access to the user’s account. In a recent blog, we discussed best practices for user enrollment, including how to prevent malicious device registration when users self-enroll.
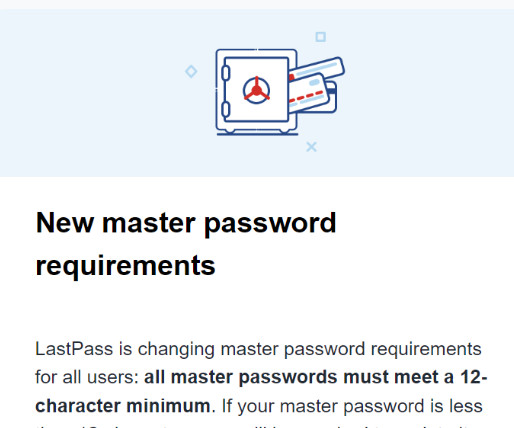
Krebs on Security
SEPTEMBER 22, 2023
Still, Palant and others impacted by the 2022 breach at LastPass say their account security settings were never forcibly upgraded. A chart on Palant’s blog post offers an idea of how increasing password iterations dramatically increases the costs and time needed by the attackers to crack someone’s master password.

Troy Hunt
JULY 8, 2019
Shortly after that blog post I launched Pwned Passwords with 306M passwords from previous breach corpuses. I made the data downloadable and also made it searchable via an API, except there are obvious issues with enabling someone to send passwords to me even if they're hashed as they were in that first instance.

Heimadal Security
SEPTEMBER 21, 2021
The post What is Doxxing and How to Avoid It (UPDATED 2021) appeared first on Heimdal Security Blog. Doxxing is analyzing information posted online by the victim in order to identify and later harass that person. What is doxxing? The term “doxxing” […].

Heimadal Security
SEPTEMBER 1, 2021
The post How to Recover Your Gmail, Yahoo, Microsoft, Facebook, Twitter or Instagram Account appeared first on Heimdal Security Blog. Big companies know this and have come up with ways […].

Heimadal Security
MARCH 17, 2022
In this article, you will find the definition of network security, […]. The post Network Security 101 – Definition, Types, Threats, and More appeared first on Heimdal Security Blog.

Heimadal Security
MARCH 11, 2022
Find out more about what software as a service model means and how you can efficiently protect your SaaS applications and implement cloud SaaS security. The post SaaS Security: How to Protect Your Enterprise in the Cloud appeared first on Heimdal Security Blog. What Is Software as a Service?

Heimadal Security
AUGUST 13, 2021
But we have to be more serious about home network security and do more than just setting a simple password. Securing the home network has […]. The post How to Enhance Your Home Network Security appeared first on Heimdal Security Blog.

Malwarebytes
OCTOBER 7, 2021
It’s simple, and it dramatically decreases the chance of someone else accessing an account.
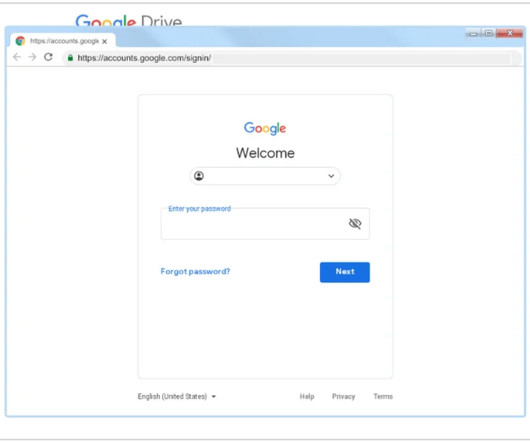
Security Affairs
APRIL 6, 2023
ARCHIPELAGO “browser-in-the-browser” phishing page The ARCHIPELAGO group has shifted its phishing tactics over time to avoid detection, the attackers use phishing messages posing as Google account security alerts.

Heimadal Security
JULY 15, 2021
Session Hijacking Types appeared first on Heimdal Security Blog. We have gathered all you need to know about what is session hijacking, how session hijacking works, and session […]. The post What Is Session Hijacking.

Heimadal Security
APRIL 29, 2022
Account Takeover Examples The five most frequently met account takeover examples are malware replay attacks, social engineering, man-in-the-middle attacks, credential […]. The post Account Takeover Definition. Account Takeover Prevention appeared first on Heimdal Security Blog.

Heimadal Security
FEBRUARY 18, 2022
The post 10 Common Network Vulnerabilities and How to Prevent Them appeared first on Heimdal Security Blog. So, if you want to find out what they are and what makes them particularly dangerous for […].

Heimadal Security
FEBRUARY 15, 2022
A vulnerability is a flaw in computer security, that leaves the […]. The post Vulnerability Assessment 101 appeared first on Heimdal Security Blog. What Are Vulnerabilities?

Heimadal Security
JULY 2, 2021
Now, an update from this week says that you can authenticate using the security keys as the only 2FA method, as the phone number or other factors are not required anymore. The post Two-Factor Authentication Simplified: Security Keys Are Now the Only Twitter 2FA Method appeared first on Heimdal Security Blog.

Heimadal Security
NOVEMBER 3, 2021
The post What Is Email Security? appeared first on Heimdal Security Blog. The massive number of organizations that routinely use email can be linked to its simplicity and overall utility. […].

Heimadal Security
FEBRUARY 20, 2022
And because you’ve seen just how easy it is to set up a new user account on Windows, in wishing not to disregard my fellow Mac users, I’ve decided to write another short and sweet piece on how to create a new user on your Mac machine. The post How to Create a New User on Mac appeared first on Heimdal Security Blog.

Heimadal Security
APRIL 16, 2021
The post Everything You Need to Know About the 2021 Facebook Data Breach appeared first on Heimdal Security Blog. Although the data is 2 years old, the 2021 Facebook data breach is an extremely serious matter, since the leaked data is still valuable to cybercriminals who use people’s personal information to […].

Heimadal Security
AUGUST 4, 2021
The post Ransomware-as-a-Service (RaaS) – The Rising Threat to Cybersecurity appeared first on Heimdal Security Blog. Considering how lucrative e-crime has become, ‘busnifying’ malware would be […].

Heimadal Security
APRIL 19, 2021
The post Between November 2020 and February 2021, Vermont Health Connect Has Suffered 10 Data Breaches appeared first on Heimdal Security Blog. According to almost 900 pages of public documentation, names, health care plans, annual revenue, birth dates, and other sensitive data were compromised in these data breaches. At […].

Heimadal Security
MARCH 5, 2021
When a RAT reaches your computer, it allows the hacker to easily access your local files, secure login authorization, and other sensitive information, or use that connection to download viruses you could unintentionally pass […]. appeared first on Heimdal Security Blog. The post What is a Remote Access Trojan (RAT)?

Heimadal Security
FEBRUARY 12, 2021
The post Malicious Insider Explained: The Call is Coming from Inside the House appeared first on Heimdal Security Blog. How can you successfully discover and mitigate a malicious insider threat before it’s too late? In the following lines, […].

SecureWorld News
MARCH 10, 2021
Out of an abundance of caution, and with a strong bias toward account security, we’ve invalidated all sessions on GitHub.com created prior to 12:03 UTC on March 8 to avoid even the remote possibility that undetected compromised sessions could still exist after the vulnerability was patched.

Malwarebytes
MAY 7, 2021
If your account is “ appropriately configured ”, you’ll be ushered into a land of extra security measures. That’s how you eventually do end up with major campaigns, with more work for law enforcement and security researchers to figure out who the new kids on the block are. Step up, and lock down.

Heimadal Security
FEBRUARY 4, 2021
After careful thought and consideration and perhaps several cups of coffee, I have decided to tackle the most common and uncommon myths surrounding email security. The post We Have Debunked 5 Myths About Email Security appeared first on Heimdal Security Blog. So, in today’s article, we’ll […].
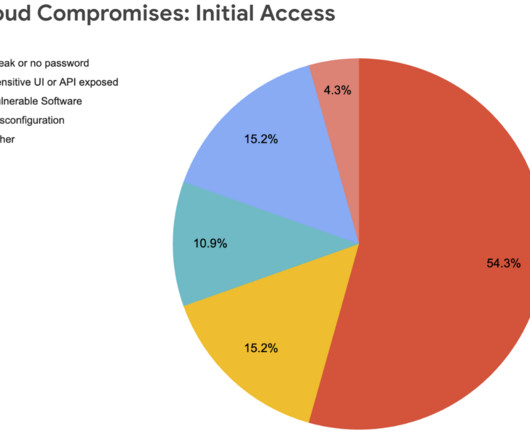
Security Boulevard
NOVEMBER 3, 2023
This is my completely informal, uncertified, unreviewed and otherwise completely unofficial blog inspired by my reading of our eighth Threat Horizons Report ( full version ) that we just released ( the official blog for #1 report , my unofficial blogs for #2 , #3 , #4 , #5 , #6 and #7 ).

Duo's Security Blog
SEPTEMBER 5, 2024
Once the dormant accounts have been identified, it’s straightforward to limit or cut off access where necessary. What is the benefit of remediating dormant or inactive accounts?

SecureWorld News
AUGUST 28, 2023
The emails in the campaign purported to be from Microsoft, and they claimed that the recipient needed to update their account security settings or activate two-factor authentication (2FA)/multi-factor authentication (MFA) within 72 hours. This phishing scam is a reminder of the dangers of QR codes.

Heimadal Security
FEBRUARY 3, 2021
Things to Consider Before Investing appeared first on Heimdal Security Blog. First and foremost, Bitcoin came out as an antagonist to centralized banking. In all intents and purposes, […]. The post Is Bitcoin Safe?
Google Security
MAY 11, 2022
Posted by Daniel Margolis, Software Engineer, Google Account Security Team Every year, security technologies improve: browsers get better , encryption becomes ubiquitous on the Web , authentication becomes stronger. This blog will deep dive into the method of phishing and how it has evolved today.

Security Boulevard
JANUARY 9, 2024
This critical vulnerability, discovered by security researchers following a disclosure on Telegram by a threat actor known as Prisma on Oct. 20, 2023, poses a substantial risk to user sessions and account security. Tell me more about the.

Heimadal Security
FEBRUARY 24, 2021
For cybercriminals, privileged user accounts are nothing more than profitable targets. appeared first on Heimdal Security Blog. Because they have elevated permissions in […]. The post What is Privilege Management?

SecureWorld News
SEPTEMBER 18, 2024
The following steps to enhance security could be listed for any blog post about any industry, but there are a couple specific to industries like food service: Encryption: Encrypting customer payment information is crucial for protecting sensitive data. With the introduction of PCI DSS 4.0, As PCI DSS 4.0

Duo's Security Blog
JANUARY 11, 2024
This feature significantly reduces user frustration and enhances account security. Offering a smooth, smart solution, Duo SSO ensures a secure and hassle-free environment for user accounts.

Malwarebytes
AUGUST 31, 2022
The attack is a devious way to try and compromise player accounts, making use of free item promises and bogus QR codes. The developers announce these changes on their blog, The Lodestone. In terms of additional account security, you can make use of a One Time Password to further bolster your security defences.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content