Rayhunter: Device to Detect Cellular Surveillance
Schneier on Security
MARCH 7, 2025
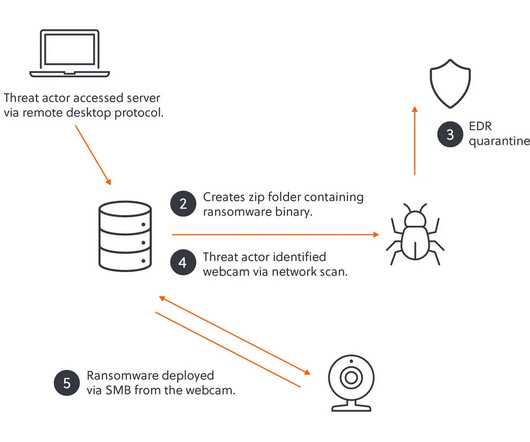
The EFF has created an open-source hardware tool to detect IMSI catchers: fake cell phone towers that are used for mass surveillance of an area. It runs on a $20 mobile hotspot.







































Let's personalize your content