Public Surveillance of Bars
Schneier on Security
JULY 2, 2024
This article about an app that lets people remotely view bars to see if they’re crowded or not is filled with commentary—on both sides—about privacy and openness.

Schneier on Security
JULY 2, 2024
This article about an app that lets people remotely view bars to see if they’re crowded or not is filled with commentary—on both sides—about privacy and openness.

Troy Hunt
JUNE 29, 2024
Why does it need to be a crazy data breach week right when I'm struggling with jet lag?! I came home from Europe just as a bunch of the Snowflake-sourced breaches started being publicly dumped, and things went a little crazy. Lots of data to review, lots of media enquiries and many discussions with impacted individuals, breached companies, incident response folks and law enforcement agencies.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
JULY 1, 2024
A new paper , “Polynomial Time Cryptanalytic Extraction of Neural Network Models,” by Adi Shamir and others, uses ideas from differential cryptanalysis to extract the weights inside a neural network using specific queries and their results. This is much more theoretical than practical, but it’s a really interesting result. Abstract: Billions of dollars and countless GPU hours are currently spent on training Deep Neural Networks (DNNs) for a variety of tasks.

Tech Republic Security
JUNE 27, 2024
This guide covers various ransomware attacks, including Colonial Pipeline, WannaCry and LockBit, the systems hackers target and how to avoid becoming a victim and paying cybercriminals a ransom.

Speaker: Speakers:
In today's digital age, having an untrained workforce can be a significant risk to your business. Cyber threats are evolving; without proper training, your employees could be the weakest link in your defense. This webinar empowers leaders like you with the tools and strategies needed to transform your employees into a robust frontline defense against cyber attacks.

Penetration Testing
JULY 1, 2024
The Qualys Threat Research Unit (TRU) has detailed a severe security flaw, dubbed ‘regreSSHion,’ that leaves millions of Linux systems vulnerable to remote code execution. The vulnerability, identified as CVE-2024-6387, affects OpenSSH’s server (sshd)... The post CVE-2024-6387: Critical OpenSSH Unauthenticated RCE Flaw ‘regreSSHion’ Exposes Millions of Linux Systems appeared first on Cybersecurity News.

The Hacker News
JULY 1, 2024
OpenSSH maintainers have released security updates to contain a critical security flaw that could result in unauthenticated remote code execution with root privileges in glibc-based Linux systems. The vulnerability has been assigned the CVE identifier CVE-2024-6387.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
JUNE 30, 2024
Fake IT support sites promote malicious PowerShell "fixes" for common Windows errors, like the 0x80070643 error, to infect devices with information-stealing malware. [.
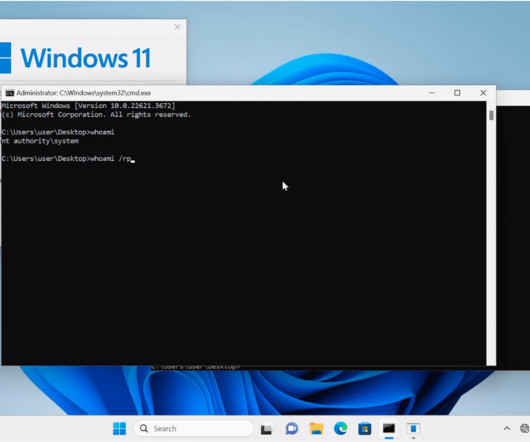
Penetration Testing
JUNE 25, 2024
A security researcher has published a proof-of-concept (PoC) exploit code targeting a recent high-severity vulnerability (CVE-2024-30088) in Microsoft Windows. This critical flaw holds a risk severity score of 7.0 and impacts systems across the... The post PoC Exploit Published for Windows Kernel Elevation of Privilege Vulnerability (CVE-2024-30088) appeared first on Cybersecurity News.

Tech Republic Security
JULY 1, 2024
Security analysts found that 52% of open-source projects are written in memory-unsafe languages like C and C++.

Schneier on Security
JUNE 25, 2024
Interesting paper about a German cryptanalysis machine that helped break the US M-209 mechanical ciphering machine. The paper contains a good description of how the M-209 works.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Boulevard
JUNE 29, 2024
AI promises considerable benefits however there’s still a lot of confusion surrounding the topic, particularly around the terms generative AI and predictive AI. The post Generative AI vs. Predictive AI: A Cybersecurity Perspective appeared first on Security Boulevard.
Bleeping Computer
JUNE 27, 2024
The remote access software company TeamViewer is warning that its corporate environment was breached in a cyberattack yesterday, with a cybersecurity firm claiming it was by an APT hacking group. [.

Malwarebytes
JUNE 28, 2024
Chinese online shopping giant Temu is facing a lawsuit filed by State of Arkansas Attorney General Tim Griffin, alleging that the retailer’s mobile app spies on users. “Temu purports to be an online shopping platform, but it is dangerous malware, surreptitiously granting itself access to virtually all data on a user’s cellphone.” Temu quickly denied the allegations.

The Hacker News
JUNE 29, 2024
Google has announced that it's going to start blocking websites that use certificates from Entrust starting around November 1, 2024, in its Chrome browser, citing compliance failures and the certificate authority's inability to address security issues in a timely manner.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Schneier on Security
JUNE 27, 2024
A group of cryptographers have analyzed the eiDAS 2.0 regulation (electronic identification and trust services) that defines the new EU Digital Identity Wallet.

Security Boulevard
JUNE 28, 2024
Chinese fast-fashion-cum-junk retailer “is a data-theft business.” The post Temu is Malware — It Sells Your Info, Accuses Ark. AG appeared first on Security Boulevard.

Bleeping Computer
JULY 1, 2024
A new OpenSSH unauthenticated remote code execution (RCE) vulnerability dubbed "regreSSHion" gives root privileges on glibc-based Linux systems.

Penetration Testing
JULY 1, 2024
The Apache Software Foundation has issued an urgent security advisory, disclosing multiple vulnerabilities in its widely used Apache HTTP Server. These flaws range from denial-of-service (DoS) attacks to remote code execution and unauthorized access,... The post Multiple Vulnerabilities in Apache HTTP Server Demand Immediate Action appeared first on Cybersecurity News.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.
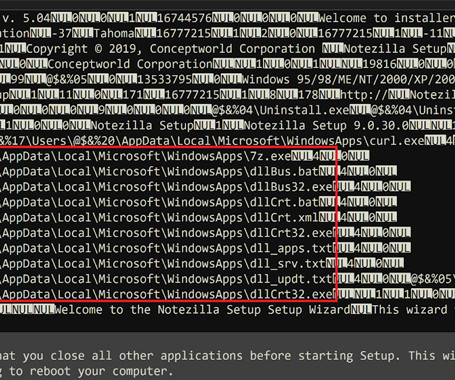
The Hacker News
JULY 1, 2024
Installers for three different software products developed by an Indian company named Conceptworld have been trojanized to distribute information-stealing malware. The installers correspond to Notezilla, RecentX, and Copywhiz, according to cybersecurity firm Rapid7, which discovered the supply chain compromise on June 18, 2024.

Schneier on Security
JUNE 28, 2024
Longtime NSA-watcher James Bamford has a long article on the reauthorization of Section 702 of the Foreign Intelligence Surveillance Act (FISA).

Security Boulevard
JUNE 25, 2024
Copying users’ files and deleting some? Even a cartoon hound knows this isn’t fine. The post Microsoft Privacy FAIL: Windows 11 Silently Backs Up to OneDrive appeared first on Security Boulevard.

Bleeping Computer
JUNE 30, 2024
The popular open source project, 'ip' had its GitHub repository archived, or made "read-only" by its developer as a result of a dubious CVE report filed for his project. Unfortunately, open-source developers have recently been met with an uptick in debatable or outright bogus CVEs filed for their projects. [.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

WIRED Threat Level
JUNE 27, 2024
AWS hosted a server linked to the Bezos family- and Nvidia-backed search startup that appears to have been used to scrape the sites of major outlets, prompting an inquiry into potential rules violations.

The Hacker News
JUNE 27, 2024
TeamViewer on Thursday disclosed it detected an "irregularity" in its internal corporate IT environment on June 26, 2024. "We immediately activated our response team and procedures, started investigations together with a team of globally renowned cyber security experts and implemented necessary remediation measures," the company said in a statement.
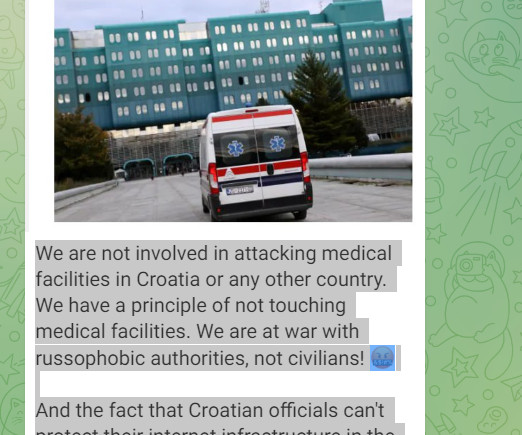
Security Affairs
JUNE 28, 2024
A cyber attack started targeting the University Hospital Centre Zagreb (KBC Zagreb) on Wednesday night, reported the Croatian Radiotelevision. A cyber attack began targeting the University Hospital Centre Zagreb (KBC Zagreb), the largest Croatian hospital, on Wednesday night, according to a report by Croatian Radiotelevision. The hospital has shut down its IT infrastructure in response to the cyber attack.

Security Boulevard
JUNE 26, 2024
30,000 websites at risk: Check yours ASAP! (800 Million Ostriches Can’t Be Wrong.) The post WordPress Plugin Supply Chain Attack Gets Worse appeared first on Security Boulevard.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.

Bleeping Computer
JUNE 29, 2024
The new Brain Cipher ransomware operation has begun targeting organizations worldwide, gaining media attention for a recent attack on Indonesia's temporary National Data Center. [.

Security Through Education
JULY 1, 2024
In the digital age, as our reliance on technology deepens, so does the creativity of malicious actors seeking to exploit vulnerabilities. One of the many growing threats to our security is SMiShing , a blend of SMS (Short Message Service) and phishing. SMiShing attacks utilize text messages to deceive individuals into divulging sensitive information or performing actions that compromise their security.

The Hacker News
JUNE 26, 2024
Apple has released a firmware update for AirPods that could allow a malicious actor to gain access to the headphones in an unauthorized manner. Tracked as CVE-2024-27867, the authentication issue affects AirPods (2nd generation and later), AirPods Pro (all models), AirPods Max, Powerbeats Pro, and Beats Fit Pro.

Security Affairs
JUNE 30, 2024
Russia-linked APT group, reportedly APT29, is suspected to be behind a hack of TeamViewer ‘s corporate network. TeamViewer discovered that a threat actor has breached its corporate network and some reports attribute the intrusion to the Russia-linked APT group APT29 (aka SVR group , BlueBravo , Cozy Bear , Nobelium , Midnight Blizzard , and The Dukes ).

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
Let's personalize your content