CVE-2024-21626: Docker Confronts Critical Container Escape Threat
Penetration Testing
JANUARY 31, 2024
In the ever-evolving world of technology, security remains a paramount concern, especially in the realm of containerization.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Penetration Testing
JANUARY 31, 2024
In the ever-evolving world of technology, security remains a paramount concern, especially in the realm of containerization.

Penetration Testing
SEPTEMBER 30, 2024
The Taiwan Computer Emergency Response Team (TWCERT/CC) has released a series of security advisories highlighting critical vulnerabilities affecting various PLANET Technology switch models.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Penetration Testing
JANUARY 19, 2024
In the vast expanse of web technology, Apache Tomcat emerges as a cornerstone, being a free and open-source implementation pivotal for the Jakarta Servlet, Jakarta Expression Language, and WebSocket technologies.

SecureList
NOVEMBER 21, 2023
In this article, we will first assess our predictions for 2023 , and then, try to figure out which trends are coming in 2024. Increase in red team penetration testing frameworks: False. This suggests that the trend of cybercriminals using penetration testing frameworks might not have been as widespread as expected in 2023.

Penetration Testing
JANUARY 21, 2024
In the interconnected realm of modern technology, where devices ranging from NAS systems to next-gen routers and headless home servers become the backbone of our digital lives, the software that powers them is of... The post CVE-2024-22416: Exposing pyLoad’s High-Risk CSRF Vulnerability appeared first on Penetration Testing.

Penetration Testing
APRIL 25, 2024
Recently, Zscaler ThreatLabz released its 2024 Phishing Report, revealing a disturbing evolution in phishing tactics fueled by generative AI technologies.

Penetration Testing
DECEMBER 21, 2023
In the shadowy realms of cyberspace, threats evolve as swiftly as the technologies they exploit. Resecurity’s insightful forecast for 2024 paints a vivid picture of the challenges that lie ahead.

The Hacker News
JUNE 11, 2024
One of the most effective ways for information technology (IT) professionals to uncover a company’s weaknesses before the bad guys do is penetration testing.
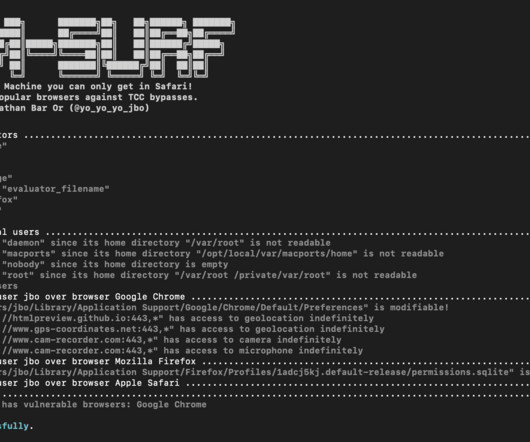
Penetration Testing
OCTOBER 17, 2024
In a significant discovery by Microsoft Threat Intelligence, a vulnerability in macOS, identified as CVE-2024-44133, has been found to bypass Apple’s Transparency, Consent, and Control (TCC) technology.

The Last Watchdog
APRIL 30, 2024
For all the discussion around the sophisticated technology, strategies, and tactics hackers use to infiltrate networks, sometimes the simplest attack method can do the most damage. Here are three strategies they should pursue in 2024 to minimize the chance of a Unitronics-style hack.

NetSpi Technical
MARCH 11, 2024
This blog will cover how we discovered CVE-2024-21378 and weaponized it by modifying Ruler , an Outlook penetration testing tool published by SensePost. SensePost released an excellent set of blogs (see references) digging into the vulnerabilities and underlying technologies as well as the exploitation tool, Ruler.

The Last Watchdog
MAY 8, 2024
May 8, 2024, CyberNewsWire — Security Risk Advisors (SRA) announces the launch of their OT/XIoT Detection Selection Workshop, a complimentary offering designed to assist organizations in selecting the most suitable operational technology (OT) and Extended Internet of Things (XIoT) security tools for their unique environments. “Our

eSecurity Planet
MAY 2, 2024
Most organizations express confidence in their current status and budgets, but also expect to experience at least one data breach in 2024. 30% data breaches and +23% ransomware for the first two months of 2024. Read on for more details on these threats or jump down to see the linked vendor reports. . +30%
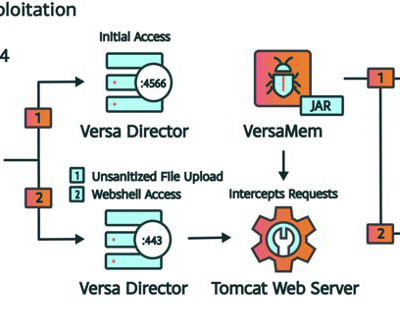
Penetration Testing
AUGUST 27, 2024
Black Lotus Labs, a threat intelligence team within Lumen Technologies, has uncovered the active exploitation of a zero-day vulnerability in Versa Director servers, identified as CVE-2024-39717.
Penetration Testing
DECEMBER 11, 2024
A collaborative research effort has exposed a significant vulnerability, designated CVE-2024-21944 and named “BadRAM,” that undermines the integrity of AMD’s Secure Encrypted Virtualization (SEV) technology.

Penetration Testing
SEPTEMBER 5, 2024
Microchip Technology, a leading American semiconductor supplier, has confirmed a significant data breach following a cyberattack in August 2024.

Penetration Testing
JULY 7, 2024
ABB, a global leader in electrification and automation technologies, has released a critical cybersecurity advisory concerning vulnerabilities in its ASPECT energy management systems.

The Last Watchdog
OCTOBER 2, 2024
2, 2024, CyberNewswire — Aembit , the non-human IAM company, today announced the appointment of Mario Duarte as chief information security officer (CISO). Duarte’s journey in cybersecurity began with a passion for penetration testing, sparked by the 1980s cult classic film WarGames. Silver Spring, MD, Oct.

The Last Watchdog
FEBRUARY 8, 2024
8, 2024 – Diversified , a leading global technology solutions provider, today announced a partnership and trio of solutions with GroCyber. About Diversified : At Diversified, we leverage the best in technology and ongoing advisory services to transform businesses. Kenilworth, NJ, Feb. Vulnerability management.

Hacker's King
OCTOBER 18, 2024
In 2024, cybersecurity and software engineering stand as two of the most critical fields shaping the tech industry. With technology advancing rapidly, both professions are highly sought after, yet cybersecurity has seen a massive surge in importance due to the increasing number of cyber threats. million cybersecurity professionals.
Penetration Testing
AUGUST 14, 2024
On August 1st, India experienced a massive disruption in its banking payment systems due to a ransomware attack on C-Edge Technologies, a service provider for several banks.

NetSpi Executives
MARCH 26, 2024
While most people may imagine mainframe computers to be an antiquated world of massive machinery, tape spools, and limited possibilities, they actually receive widespread use today in 2024 as the backbone infrastructure that allows billions of financial transactions to occur daily on a global scale.
Penetration Testing
JULY 3, 2024
Security researchers from Graz University of Technology have unveiled a novel cybersecurity threat dubbed “SnailLoad” (CVE-2024-39920).

Penetration Testing
JULY 31, 2024
Dahua Technology, a leading provider of video surveillance solutions, has released a security advisory addressing multiple vulnerabilities in their network video recorders (NVRs) and IP cameras. These vulnerabilities, with CVSS scores ranging from 4.9...

BH Consulting
JANUARY 16, 2024
Over the past two decades, we have witnessed unprecedented changes in technology. 2024: the year of the ra…nsomware? MORE SecButler from GroundSec is a free set of tools for penetration tests. MORE This podcast wonders if AI will affect the many elections happening in 2024.

eSecurity Planet
AUGUST 7, 2024
Adopts proactive security: Uses automated technologies for vulnerability scans and misconfiguration checks to identify and address threats before they arise. This includes deploying technologies for encryption, monitoring, vulnerability management, and threat detection. Prevents mishaps and reduces the severity of threats.

Malwarebytes
MARCH 22, 2024
In February 2024 the Canadian government announced plans to ban the sale of the Flipper Zero, mainly because of its reported use to steal cars. The Flipper Zero is a portable device that can be used in penetration testing with a focus on wireless devices and access control systems.

SecureWorld News
NOVEMBER 18, 2024
The report, released on November 13, 2024, underscores the urgent need for increased security measures to protect critical infrastructure. To mitigate these risks, water utilities should: Prioritize cybersecurity: Implement robust cybersecurity practices, including regular vulnerability assessments, penetration testing, and employee training.

NetSpi Executives
MARCH 26, 2024
While most people may imagine mainframe computers to be an antiquated world of massive machinery, tape spools, and limited possibilities, they actually receive widespread use today in 2024 as the backbone infrastructure that allows billions of financial transactions to occur daily on a global scale.
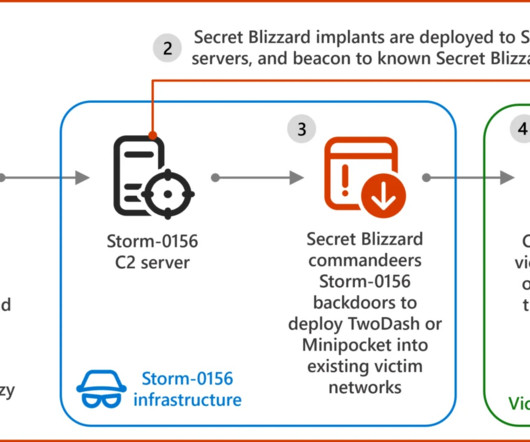
Security Affairs
DECEMBER 5, 2024
— Microsoft Threat Intelligence (@MsftSecIntel) December 4, 2024 In partnership with Black Lotus Labs, researchers confirmed Secret Blizzard is using Storm-0156 infrastructure to deploy backdoors, clipboard monitors, and other espionage tools. ” reads the report published by Microsoft.

NetSpi Executives
AUGUST 16, 2024
In cybersecurity, few events hold as much anticipation as Black Hat USA, where industry experts come together to discuss the latest trends and technologies. Automation in Penetration Testing Aaron and Vinay both observed a growing trend toward automated penetration testing.

eSecurity Planet
MAY 13, 2024
From the other end of the supply chain, many vendors build Cinterion Cellular Modems into their internet-of-things (IoT) or operations technology (OT) equipment such as sensors, meters, or even medical devices. May 5, 2024 Tinyproxy Vulnerability Potentially Exposes 50,000+ Hosts Type of vulnerability: Use after free.
Security Affairs
DECEMBER 2, 2022
Once a niche technology, drones are about to explode in terms of market growth and enterprise adoption. Naturally, threat actors follow the trend and exploit the technology for surveillance, payload delivery, kinetic operations, and even diversion. Original post at [link]. Market overview. Danger Drone platform.
Penetration Testing
JULY 17, 2024
A new study presented at the Privacy Enhancing Technologies Symposium (PETS) 2024 has revealed a vulnerability in popular VPN protocols like OpenVPN and WireGuard.

Penetration Testing
JULY 28, 2024
Taiwan’s CERT (Computer Emergency Response Team) has issued a critical warning regarding two severe vulnerabilities [1, 2] discovered in Simopro Technology’s WinMatrix IT resource management system.

Penetration Testing
JULY 1, 2024
In a significant move that underscores the critical nature of digital security, Google has announced that, starting November 1, 2024, Chrome 127 and all subsequent versions will no longer trust newly issued digital certificates... The post Google to Drop Entrust Certificates from Chrome Starting November 2024 appeared first on Cybersecurity (..)

eSecurity Planet
FEBRUARY 2, 2024
While Teslas aren’t the typical business IoT device, their connection to the internet makes them a cyber threat as much as your business’s other IoT technology. This year, electric cars were a major focal point of the 2024 event, called Pwn2Own Automotive.

Penetration Testing
OCTOBER 19, 2024
A newly disclosed vulnerability in multiple SICK products, tracked as CVE-2024-10025, has raised significant cybersecurity concerns across industries relying on the company’s automation and sensor technologies.

Penetration Testing
NOVEMBER 20, 2024
Recently, Palo Alto Networks has released an in-depth analysis of FrostyGoop, also known as BUSTLEBERM, a sophisticated malware targeting operational technology (OT). This malware gained attention in July 2024 when... The post FrostyGoop: New ICS Malware Exploits Modbus TCP Protocol appeared first on Cybersecurity News.

Penetration Testing
OCTOBER 14, 2024
In a recent vulnerability note issued by TWCERT/CC (Taiwan Computer Emergency Response Team / Coordination Center), three significant security vulnerabilities have been identified in Team+, a popular secure communication and... The post CVE-2024-9921 (CVSS 9.8): Critical Flaw Found in Popular Business Collaboration Tool Team+ appeared first (..)

Penetration Testing
DECEMBER 15, 2024
OpenAI experienced a significant service disruption on December 11, 2024, impacting all its services, including ChatGPT, the API, and Sora. The outage, lasting over four hours, was caused by a... The post OpenAI Services Hit by Major Outage Due to Telemetry Service Deployment appeared first on Cybersecurity News.
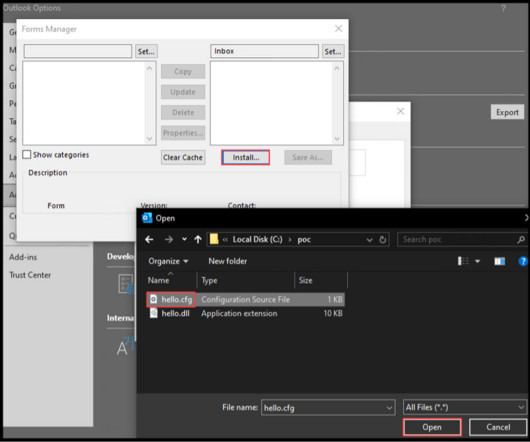
NetSpi Technical
MARCH 11, 2024
This blog will cover how we discovered CVE-2024-21378 and weaponized it by modifying Ruler , an Outlook penetration testing tool published by SensePost. SensePost released an excellent set of blogs (see references) digging into the vulnerabilities and underlying technologies as well as the exploitation tool, Ruler.

NetSpi Executives
NOVEMBER 21, 2024
TL;DR Forrester analyzed several attack surface management (ASM) vendors varying in size, type of offering, and use cases in its landscape report, The Attack Surface Management Solutions Landscape, Q2 2024. This platform model gives security teams access to key proactive security solutions in a single technology.

NetSpi Executives
NOVEMBER 21, 2024
TL;DR Forrester analyzed several attack surface management (ASM) vendors varying in size, type of offering, and use cases in its landscape report, The Attack Surface Management Solutions Landscape, Q2 2024. This platform model gives security teams access to key proactive security solutions in a single technology.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content