Senators Urge FTC to Probe ID.me Over Selfie Data
Krebs on Security
MAY 18, 2022
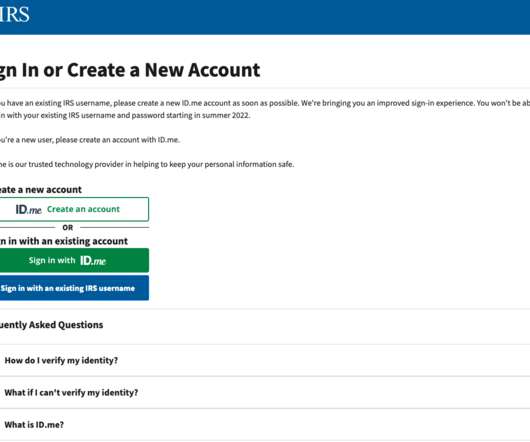
for “deceptive statements” the company and its founder allegedly made over how they handle facial recognition data collected on behalf of the Internal Revenue Service , which until recently required anyone seeking a new IRS account online to provide a live video selfie to ID.me. ” But several days after a Jan.


















Let's personalize your content