2020 Workshop on Economics of Information Security
Schneier on Security
OCTOBER 14, 2020
The Workshop on Economics of Information Security will be online this year. Register here.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
OCTOBER 14, 2020
The Workshop on Economics of Information Security will be online this year. Register here.

Schneier on Security
DECEMBER 4, 2020
The workshop on Economics and Information Security is always an interesting conference. This year, it will be online. Here’s the program. Registration is free.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
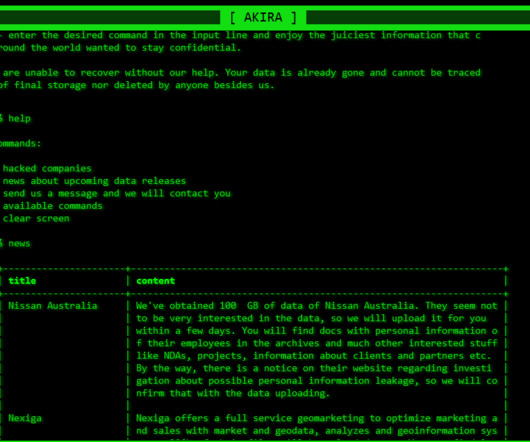
Security Affairs
FEBRUARY 17, 2024
CISA warns that the Akira Ransomware gang is exploiting the Cisco ASA/FTD vulnerability CVE-2020-3259 (CVSS score: 7.5) Cybersecurity and Infrastructure Security Agency (CISA) added a Cisco ASA and FTD bug, tracked as CVE-2020-3259 (CVSS score: 7.5), to its Known Exploited Vulnerabilities catalog. in attacks in the wild.

Schneier on Security
FEBRUARY 11, 2022
Under-resourced Information Security Managers were not performing their business as usual role (including a NIST-based cybersecurity review of systems) but were working on evaluating security controls for the COVID-19 vaccination system. Over 30,000 machines were running Windows 7 (out of support since January 2020).

Security Affairs
SEPTEMBER 22, 2024
GreyNoise Intelligence firm warns of a mysterious phenomenon observed since January 2020, massive waves of spoofed traffic called Noise Storms. GreyNoise Intelligence has been tracking a mysterious phenomenon since January 2020 consisting of massive waves of spoofed traffic, tracked by the experts as ‘Noise Storms.’
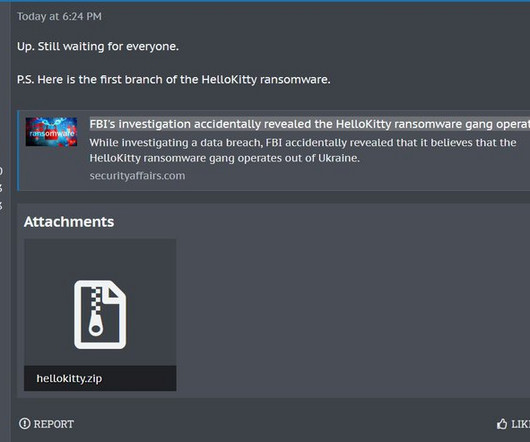
Security Affairs
OCTOBER 9, 2023
pic.twitter.com/YJavUu53v3 — vx-underground (@vxunderground) October 7, 2023 BleepingComputer was able to verify with the help of the popular malware researcher Michael Gillespie that that source code is legitimate and is related to the first version of the ransomware that was employed in 2020.

The Last Watchdog
JANUARY 6, 2022
billion in 2020 and will grow to $16.1 Yet, according to the study by the Ponemon Institute, the number of insider leaks has increased by 47 percent in 2020 compared to 2018. But they have more disadvantages than benefits if we talk about ensuring information security. billion by 2025. Yes, they are cheap to apply.
Krebs on Security
MARCH 1, 2022
Shouting “Glory for Ukraine,” the Contileaks account has since published additional Conti employee conversations from June 22, 2020 to Nov. 22, 2020, the U.S. By late October 2020, Conti’s network of infected systems had grown to include 428 medical facilities throughout the United States. On Sunday, Feb.

The Hacker News
MAY 24, 2024
Introduction The infamous Colonial pipeline ransomware attack (2021) and SolarWinds supply chain attack (2020) were more than data leaks; they were seismic shifts in cybersecurity.
Schneier on Security
OCTOBER 13, 2020
Here’s an arson case where the FBI asked Google who searched for a particular street address: Homeland Security special agent Sylvette Reynoso testified that her team began by asking Google to produce a list of public IP addresses used to google the home of the victim in the run-up to the arson.

Daniel Miessler
MARCH 22, 2020
DanielMiessler) March 21, 2020. But when people remember the Great Depression of 2020, caused by a pandemic, nobody will lift a finger to stop video surveillance tech that claims to be able to spot sick people. Similar used in China [link] — Joseph Cox (@josephfcox) March 17, 2020. Busses, train stations, airports, etc.
Krebs on Security
APRIL 20, 2023
In many cases, the phony profiles spoofed chief information security officers at major corporations , and some attracted quite a few connections before their accounts were terminated. Microsoft Corp. For now, it remains unclear whether the compromised X_Trader software was downloaded by people at other software firms.

Krebs on Security
MAY 22, 2023
pw has been registered and abandoned by several parties since 2014, but the most recent registration data available through DomainTools.com shows it was registered in March 2020 to someone in Krasnodar, Russia with the email address edgard011012@gmail.com. In May 2020, Zipper told another Lolzteam member that quot[.]pw

Security Affairs
JUNE 21, 2024
French information security agency ANSSI reported that Russia-linked threat actor Nobelium is behind a series of cyber attacks that targeted French diplomatic entities. The French information security agency ANSSI reported that Russia-linked APT Nobelium targeted French diplomatic entities.

Daniel Miessler
APRIL 9, 2020
DanielMiessler) April 3, 2020. DanielMiessler) April 6, 2020. But if you’ve been in security a while you know that vulnerabilities aren’t absent just because they aren’t being talked about. And now that they’ve had all this scrutiny, it’ll be even more secure in the coming weeks and months.

Krebs on Security
OCTOBER 28, 2020
In March 2020, KrebsOnSecurity alerted Swedish security giant Gunnebo Group that hackers had broken into its network and sold the access to a criminal group which specializes in deploying ransomware. “The harsh and unfortunate reality is the security of a number of security companies is s**t,” Arena said.

Daniel Miessler
SEPTEMBER 29, 2020
DanielMiessler) September 19, 2020. SafetyDetectives reports the average cost of a ransomware-caused downtime incident has risen from $46,800 in 2018, to $141,000 in 2019, to $283,800 in 2020. A ransomware attack against the New Orleans city government in early 2020 cost the city over $7 million dollars.

Schneier on Security
AUGUST 8, 2022
Twenty-six advanced to Round 2 in 2019, and seven (plus another eight alternates) were announced as Round 3 finalists in 2020. Fun fact: Those three algorithms were broken by the Center of Encryption and Information Security, part of the Israeli Defense Force. Sixty-nine were considered complete enough to be Round 1 candidates.

Krebs on Security
OCTOBER 30, 2024
The chief information security officer for a large academic healthcare system affected by the breach told KrebsOnSecurity they participated in a call with the FBI and were told a third party partner managed to recover at least four terabytes of data that was exfiltrated from Change by the cybercriminal group.

Security Affairs
FEBRUARY 16, 2024
Cisco addressed the flaw in May 2020. The vulnerability CVE-2024-21410 is a bypass vulnerability that can be exploited by an attacker to bypass the SmartScreen user experience and inject code to potentially gain code execution, which could lead to some data exposure, lack of system availability, or both.

Krebs on Security
JUNE 18, 2021
The SEC said that under First American’s remediation policies, if the person responsible for fixing the problem is unable to do so based on the timeframes listed above, that employee must have their management contact the company’s information security department to discuss their remediation plan and proposed time estimate.

Security Affairs
JANUARY 12, 2022
CVE-2020-5902 F5 Big-IP CVE-2020-14882 Oracle WebLogic CVE-2021-26855 Microsoft Exchange (Note: this vulnerability is frequently observed used in conjunction with CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065). Some of the hacking campaigns that were publicly attributed to Russian state-sponsored APT actors by U.S.

Security Affairs
DECEMBER 2, 2021
The fifth issue added to the list of actively exploited vulnerabilities is the CVE-2020-11261 Improper Input Validation flaw that impacts multiple Qualcomm chipsets. There are indications that CVE-2020-11261 may be under limited, targeted exploitation” reads a note added to the January security bulletin last week.

Security Affairs
OCTOBER 1, 2024
Cybersecurity and Infrastructure Security Agency (CISA) added SonicWall SonicOS, ImageMagick and Linux Kernel vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog. CVE-2020-15415 is an OS command injection vulnerability in DrayTek Multiple Vigor Routers.

Malwarebytes
NOVEMBER 1, 2023
The Securities and Exchange Commission (SEC) has announced charges against software company SolarWinds Corporation and its chief information security officer (CISO), Timothy G. Brown, for “fraud and internal control failures relating to allegedly known cybersecurity risks and vulnerabilities.”

Krebs on Security
OCTOBER 8, 2020
There’s an old adage in information security: “Every company gets penetration tested, whether or not they pay someone for the pleasure.” ” Many organizations that do hire professionals to test their network security posture unfortunately tend to focus on fixing vulnerabilities hackers could use to break in.

Security Affairs
SEPTEMBER 19, 2024
CVE-2020-14644 vulnerability (CVSS score of 9.8) The flaw was disclosed by the researcher SandboxEscaper in June, and Microsoft addressed it in the same month with the release of Patch Tuesday security updates. CVE-2020-0618 vulnerability (CVSS score of 7.8) The flaw affects 12.2.1.3.0 and 12.2.1.4.0

Schneier on Security
JUNE 8, 2021
Last year, one of us (Tarah) was listening to a NATO briefing after the end of the 2020 Cyber Coalition exercises, and asked how she and other information security researchers could volunteer to test cyber ranges used to train its cyber incident response force.

Daniel Miessler
NOVEMBER 6, 2020
I think there are four main trends that will play out in the field of information security in the next 20 years. Here’s my talk on this topic at DEFCON in 2020. Keep in mind that trend #1 will be counterbalanced by the growth of people who need basic information security help. Image from information-age.com.
Security Affairs
NOVEMBER 11, 2021
Below is the list of exploits used by the bot: Vulnerability Affected devices CVE-2020-8515 DrayTek Vigor2960 1.3.1_Beta, Vigor3900 1.4.4_Beta, and Vigor300B 1.3.3_Beta, 1.4.2.1_Beta, and 1.4.4_Beta devices CVE-2015-2051 D-Link DIR-645 Wired/Wireless Router Rev. CVE-2020-10173 Comtrend VR-3033 DE11-416SSG-C01_R02.A2pvI042j1.d26m

Security Affairs
JUNE 27, 2024
Roundcube Webmail CVE-2020-13965 (CVSS score of 6.1) Roundcube addressed the flaw in June 2020, and PoC code was released shortly thereafter. is a code injection issue in the Jai-Ext open source project. The vulnerability was fixed in August 2022, however technical details and PoC were published a few weeks later. and 1.3.12.

Security Affairs
SEPTEMBER 6, 2024
The FBI, CISA, and NSA linked threat actors from Russia’s GRU Unit 29155 to global cyber operations since at least 2020. Since 2020, the unit has expanded into offensive cyber operations aimed at espionage, reputational harm, and data destruction. These operations include espionage, sabotage, and reputational damage.
SecureList
FEBRUARY 1, 2022
However, almost as soon as development began, serious questions arose about the security of the service’s data storage and the possibility of it being misused. In 2020, Proteus went bankrupt. That’s why we decided to test our assumption and delve into the security landscape of telehealth in 2020 and 2021.
Security Affairs
SEPTEMBER 21, 2023
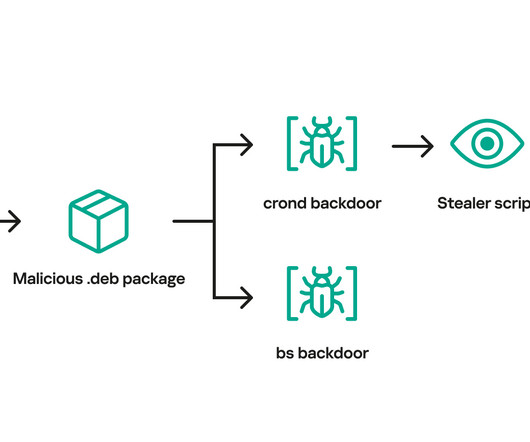
The recently discovered Free Download Manager (FDM) supply chain attack, which distributed Linux malware, started back in 2020. The maintainers of Free Download Manager (FDM) confirmed that the recently discovered supply chain attack dates back to 2020. collect) that launches the /var/tmp/crond file every 10 minutes.”
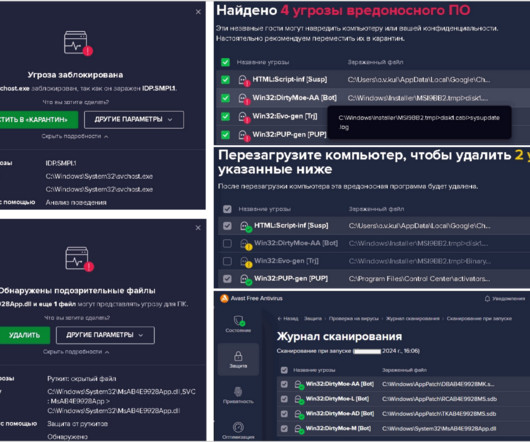
Security Affairs
FEBRUARY 2, 2024
.” In June 2021, researchers from Avast warned of the rapid growth of the DirtyMoe botnet ( PurpleFox , Perkiler , and NuggetPhantom ), which passed from 10,000 infected systems in 2020 to more than 100,000 in the first half of 2021. Experts defined DirtyMoe as a complex malware that has been designed as a modular system.

The Last Watchdog
JUNE 21, 2020
The epidemic went truly mainstream with the release of CryptoLocker back in 2013, and it has since transformed into a major dark web economy spawning the likes of Sodinokibi, Ryuk, and Maze lineages that are targeting the enterprise on a huge scale in 2020. In early 2020, several cybercriminals groups followed suit.

Security Affairs
OCTOBER 5, 2023
“The document said the exploit worked for Android versions 9 to 11, which was released in 2020, and that it took advantage of a flaw in the “image rendering library.” In 2020 and 2021, WhatsApp fixed three vulnerabilities — CVE-2020-1890, CVE-2020-1910, and CVE-2021-24041— that all involved how the app processes images.

Security Affairs
NOVEMBER 22, 2021
” said Demetrius Comes, GoDaddy’s Chief Information Security Officer. The attackers were able to access the above GoDaddy customer information using the compromised password. . “On November 17, 2021, we discovered unauthorized third-party access to our Managed WordPress hosting environment.”
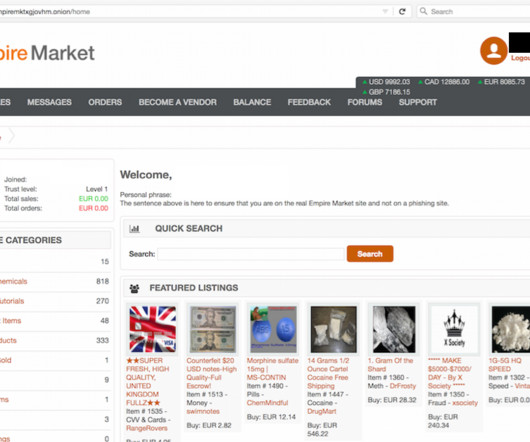
Security Affairs
JUNE 17, 2024
Two men, Thomas Pavey (aka “Dopenugget”) and Raheim Hamilton (aka “Sydney” and “Zero Angel”), have been charged in federal court in Chicago for operating the dark web marketplace “ Empire Market ” from 2018 to 2020. currency on AlphaBay before starting Empire Market.

The Last Watchdog
JANUARY 9, 2024
billion AR devices worldwide by 2024 — nearly three times the figure from 2020. Everyone in the company is responsible for maintaining information security and applying protective measures in line with established policies. These industries are growing in popularity and demand. Research suggests there will be over 1.7

Security Affairs
NOVEMBER 25, 2024
In September 2024, the FBI, CISA, and NSA linked threat actors from Russia’s GRU Unit 29155 to global cyber operations since at least 2020. Since 2020, the unit has expanded into offensive cyber operations aimed at espionage, reputational harm, and data destruction.

Security Affairs
APRIL 13, 2022
According to the advisory published by Apache, the issue addressed by the organization is a critical flaw in Apache Struts linked to a previous OGNL Injection flaw ( CVE-2020-17530 ) that wasn’t properly fixed. “The fix issued for CVE-2020-17530 ( S2-061 ) was incomplete.
Krebs on Security
DECEMBER 19, 2024
The makers of Acunetix, Texas-based application security vendor Invicti Security , confirmed Silent Push’s findings, saying someone had figured out how to crack the free trial version of the software so that it runs without a valid license key. In early 2020, Exorn promoted a website called “ orndorks[.]com
The Last Watchdog
MAY 13, 2020
Chief Information Security Officers were already on the hot seat well before the COVID-19 global pandemic hit, and they are even more so today. In its 2020 fiscal year, ending March 31, Infosys reported revenue of $12.8 Related: Why U.S. I had the chance to discuss this state of affairs with Vishal Salvi, CISO of Infosys.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content