2020 Workshop on Economics of Information Security
Schneier on Security
OCTOBER 14, 2020
The Workshop on Economics of Information Security will be online this year. Register here.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
OCTOBER 14, 2020
The Workshop on Economics of Information Security will be online this year. Register here.

Schneier on Security
DECEMBER 4, 2020
The workshop on Economics and Information Security is always an interesting conference. This year, it will be online. Here’s the program. Registration is free.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
DECEMBER 27, 2024
charges for allegedly threatening to release data stolen from a company in a March 2020 security breach. government has charged the Brazilian citizen Junior Barros De Oliveira, 29, with allegedly threatening to release data stolen from a company during a March 2020 security breach. A Brazilian citizen faces U.S.
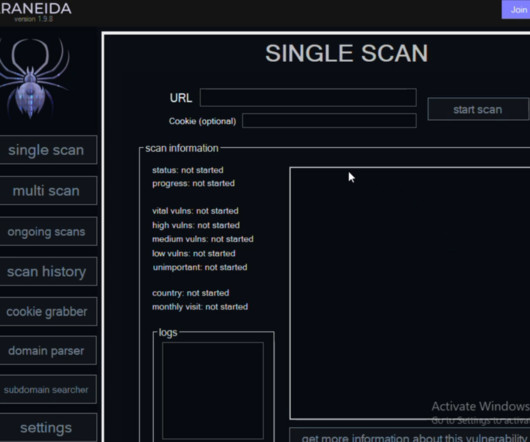
Krebs on Security
DECEMBER 19, 2024
The makers of Acunetix, Texas-based application security vendor Invicti Security , confirmed Silent Push’s findings, saying someone had figured out how to crack the free trial version of the software so that it runs without a valid license key. In early 2020, Exorn promoted a website called “ orndorks[.]com

Krebs on Security
OCTOBER 30, 2024
The chief information security officer for a large academic healthcare system affected by the breach told KrebsOnSecurity they participated in a call with the FBI and were told a third party partner managed to recover at least four terabytes of data that was exfiltrated from Change by the cybercriminal group.

Security Affairs
FEBRUARY 6, 2025
The vulnerability CVE-2020-15069 (CVSS score of 9.8) is a Remote Code Execution flaw in Microsoft Outlook. . “Successful exploitation of this vulnerability would allow an attacker to bypass the Office Protected View and open in editing mode rather than protected mode.” ” reads the advisory published by Microsoft.
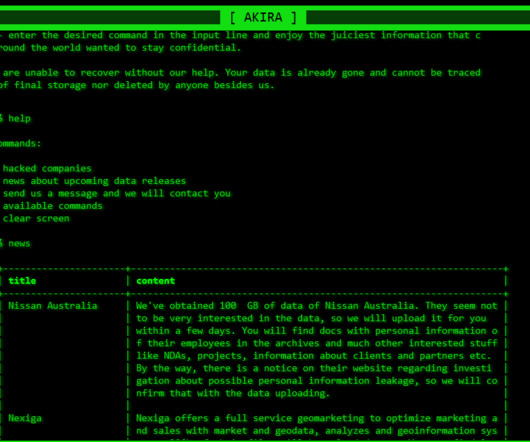
Security Affairs
FEBRUARY 17, 2024
CISA warns that the Akira Ransomware gang is exploiting the Cisco ASA/FTD vulnerability CVE-2020-3259 (CVSS score: 7.5) Cybersecurity and Infrastructure Security Agency (CISA) added a Cisco ASA and FTD bug, tracked as CVE-2020-3259 (CVSS score: 7.5), to its Known Exploited Vulnerabilities catalog. in attacks in the wild.

Security Affairs
SEPTEMBER 22, 2024
GreyNoise Intelligence firm warns of a mysterious phenomenon observed since January 2020, massive waves of spoofed traffic called Noise Storms. GreyNoise Intelligence has been tracking a mysterious phenomenon since January 2020 consisting of massive waves of spoofed traffic, tracked by the experts as ‘Noise Storms.’

Security Affairs
JANUARY 4, 2025
The botnet has been active since at least May 2020, reaching its peak with 60,000 compromised devices in June 2023. In September 2024, cybersecurity researchers from Lumens Black Lotus Labs discovered a new botnet, named Raptor Train, composed of small office/home office (SOHO) and IoT devices.
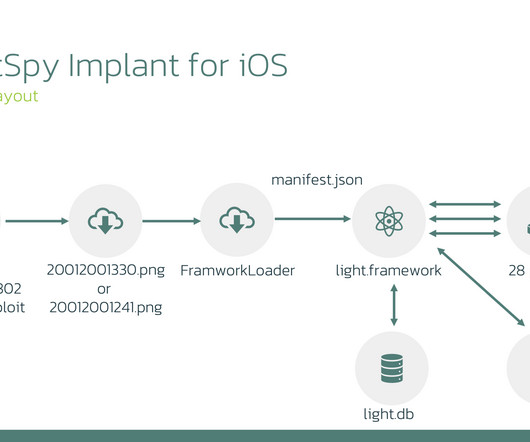
Security Affairs
NOVEMBER 1, 2024
The experts discovered five active C2 servers linked to the new version, with the latest deployment date listed as October 26, 2022, despite using a vulnerability patched in 2020. The authors utilized the publicly available Safari exploit CVE-2020-9802 for initial access and CVE-2020-3837 for privilege escalation.
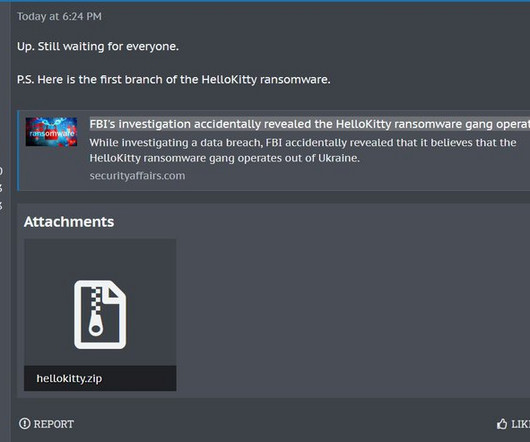
Security Affairs
OCTOBER 9, 2023
pic.twitter.com/YJavUu53v3 — vx-underground (@vxunderground) October 7, 2023 BleepingComputer was able to verify with the help of the popular malware researcher Michael Gillespie that that source code is legitimate and is related to the first version of the ransomware that was employed in 2020.

Security Affairs
JANUARY 28, 2025
The EU sanctioned three members of Russia’s GRU Unit 29155 for cyberattacks on Estonia’s government agencies in 2020. “The Council today adopted additional restrictive measures against three Russian individuals responsible for a series of cyberattacks carried out against the Republic of Estonia in 2020. .

The Last Watchdog
JANUARY 6, 2022
billion in 2020 and will grow to $16.1 Yet, according to the study by the Ponemon Institute, the number of insider leaks has increased by 47 percent in 2020 compared to 2018. But they have more disadvantages than benefits if we talk about ensuring information security. billion by 2025. Yes, they are cheap to apply.

Security Affairs
NOVEMBER 25, 2024
In September 2024, the FBI, CISA, and NSA linked threat actors from Russia’s GRU Unit 29155 to global cyber operations since at least 2020. Since 2020, the unit has expanded into offensive cyber operations aimed at espionage, reputational harm, and data destruction.

Security Affairs
MARCH 8, 2025
The company announced it will enhance security measures, improve service quality, and promptly disclose updates while maintaining customer confidentiality. In May 2020, NTT Communications (NTT Com) disclosed a data breach that impacted hundreds of customers.
Krebs on Security
MARCH 1, 2022
Shouting “Glory for Ukraine,” the Contileaks account has since published additional Conti employee conversations from June 22, 2020 to Nov. 22, 2020, the U.S. By late October 2020, Conti’s network of infected systems had grown to include 428 medical facilities throughout the United States. On Sunday, Feb.

Security Affairs
DECEMBER 23, 2024
2 NSO continued to use and make Erised available to customers even after this litigation had been filed, until changes to WhatsApp blocked its access sometime after May 2020. from April 29, 2018, to May 10, 2020). NSOs witnesses have refused to answer whether it developed further WhatsApp-based Malware Vectors thereafter.

Malwarebytes
NOVEMBER 12, 2024
In 2018, MyHeritage suffered a security incident which exposed the email addresses and hashed passwords of 92 million users. In 2020, Ancestry was acquired by investment firm Blackstone for $4.7 Since those early days, we’ve had several warnings about how submitting your genetic data can go sideways.

Security Affairs
APRIL 8, 2025
The group has been active since 2020, the operation has evolved from data theft extortion to using ransomware and initial access broker activity. “The Everest ransomware group has been active since 2020, and has engaged in data extortion and ransomware operations, along with initial access broker (IAB) activity.

The Hacker News
MAY 24, 2024
Introduction The infamous Colonial pipeline ransomware attack (2021) and SolarWinds supply chain attack (2020) were more than data leaks; they were seismic shifts in cybersecurity.

Security Affairs
OCTOBER 23, 2024
“According to the SEC’s orders, Unisys, Avaya, and Check Point learned in 2020, and Mimecast learned in 2021, that the threat actor likely behind the SolarWinds Orion hack had accessed their systems without authorization, but each negligently minimized its cybersecurity incident in its public disclosures.”
Schneier on Security
OCTOBER 13, 2020
Here’s an arson case where the FBI asked Google who searched for a particular street address: Homeland Security special agent Sylvette Reynoso testified that her team began by asking Google to produce a list of public IP addresses used to google the home of the victim in the run-up to the arson.

Security Affairs
DECEMBER 26, 2024
In April 2021, China-linked APT breached New York Citys Metropolitan Transportation Authority (MTA) network exploiting a Pulse Secure zero-day. In December 2020, Egregor ransomware operators hit Metro Vancouvers transportation agency TransLink causing the disruption of its services and payment systems.

Security Affairs
NOVEMBER 18, 2024
Below is the list of previous incidents suffered by T-Mobile: In August 2021, a security breach impacted 54 million customers. In December 2020, T-Mobile disclosed a data breach that exposed customers’ network information (CPNI). In March 2020, threat actors gained access to T-Mobile customers and employee personal info.
Security Affairs
NOVEMBER 5, 2024
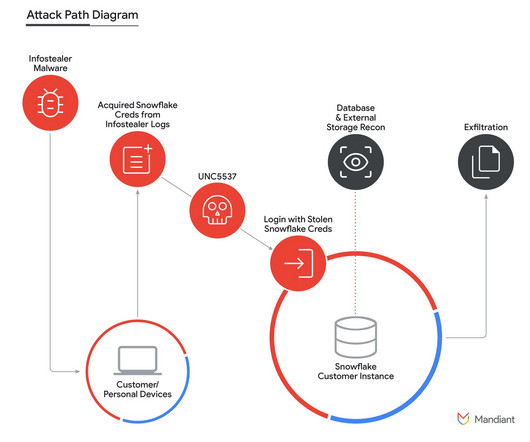
Mandiant reported that many stolen credentials dated back to 2020. This led to extensive data theft, with the attackers later attempting to extort victims and sell stolen data on criminal forums. In September, the popular cyber journalist Brian Krebs linked Mr. Moucka to crime-focused chat communities known as “The Com.”

Security Affairs
NOVEMBER 18, 2024
Privacy Shield framework in 2020. This breach involved highly sensitive information, including criminal records and medical details, marking it as one of the largest GDPR fines specifically tied to cross-border data transfers. The company faced allegations of improperly transferring sensitive data about European drivers to the U.S.

Daniel Miessler
MARCH 22, 2020
DanielMiessler) March 21, 2020. But when people remember the Great Depression of 2020, caused by a pandemic, nobody will lift a finger to stop video surveillance tech that claims to be able to spot sick people. Similar used in China [link] — Joseph Cox (@josephfcox) March 17, 2020. Busses, train stations, airports, etc.

Security Affairs
JANUARY 12, 2025
Sadeghipour made the headlines for other important disclosures, in October 2020 he was part of a team of researchers that received hundreds of thousands of dollars in bug bounties for reporting 55 vulnerabilities as part of the Apple bug bounty program. Other organizations could suffered similar issues.

Security Affairs
NOVEMBER 29, 2024
On or about June 25, 2020, Matveev and his LockBit coconspirators targeted a law enforcement agency in Passaic County, New Jersey. The DoJ unsealed two indictments charging the man with using three different ransomware families in attacks aimed at numerous victims throughout the United States.
Krebs on Security
APRIL 20, 2023
In many cases, the phony profiles spoofed chief information security officers at major corporations , and some attracted quite a few connections before their accounts were terminated. Microsoft Corp. For now, it remains unclear whether the compromised X_Trader software was downloaded by people at other software firms.
Security Affairs
DECEMBER 17, 2024
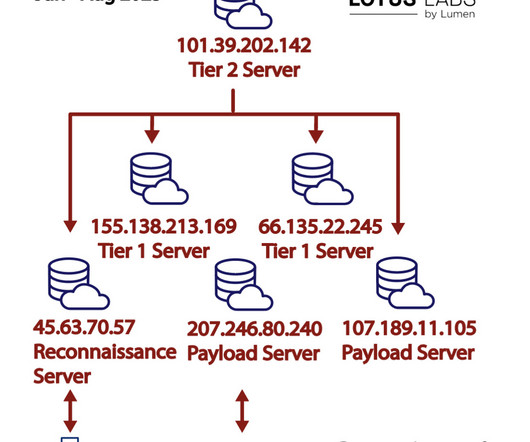
The threat actors attempted to exploit multiple vulnerabilities in DVRs, including CVE-2017-7921, CVE-2018-9995 , CVE-2020-25078, CVE-2021-33044 , and CVE-2021-36260. In March 2024, threat actors behind this campaign started targeting Internet of Things (IoT) devices in the US, Australia, Canada, New Zealand, and the United Kingdom.

Security Affairs
NOVEMBER 19, 2024
Evgenii Ptitsyn and others allegedly ran an international hacking scheme since November 2020, deploying Phobos ransomware to extort victims. .” The Russian national was allegedly involved in the development, sale, distribution, and operations of the ransomware.

Security Affairs
JUNE 21, 2024
French information security agency ANSSI reported that Russia-linked threat actor Nobelium is behind a series of cyber attacks that targeted French diplomatic entities. The French information security agency ANSSI reported that Russia-linked APT Nobelium targeted French diplomatic entities.

Schneier on Security
AUGUST 8, 2022
Twenty-six advanced to Round 2 in 2019, and seven (plus another eight alternates) were announced as Round 3 finalists in 2020. Fun fact: Those three algorithms were broken by the Center of Encryption and Information Security, part of the Israeli Defense Force. Sixty-nine were considered complete enough to be Round 1 candidates.

Security Affairs
DECEMBER 21, 2024
In August 2020, the FBI has issued a security alert about Netwalker ransomware attacks targeting U.S. million ransom to recover its files. and foreign government organizations.

Security Affairs
FEBRUARY 2, 2025
The HeartSender group has sold phishing tools to criminals since 2020, causing over $3 million in U.S. and Dutch authorities participated in the operation, the police seized the domains on January 29, 2025.

Krebs on Security
OCTOBER 28, 2020
In March 2020, KrebsOnSecurity alerted Swedish security giant Gunnebo Group that hackers had broken into its network and sold the access to a criminal group which specializes in deploying ransomware. “The harsh and unfortunate reality is the security of a number of security companies is s**t,” Arena said.

Krebs on Security
JUNE 18, 2021
The SEC said that under First American’s remediation policies, if the person responsible for fixing the problem is unable to do so based on the timeframes listed above, that employee must have their management contact the company’s information security department to discuss their remediation plan and proposed time estimate.
Security Affairs
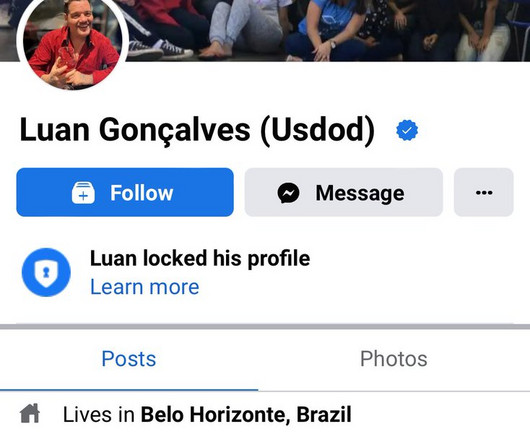
OCTOBER 16, 2024
. “A search and seizure warrant and a preventive arrest warrant were served in the city of Belo Horizonte/MG against an investigated person suspected of being responsible for two publications selling Federal Police data, on May 22, 2020 and on February 22, 2022.

Security Affairs
NOVEMBER 2, 2024
Between 2020 and 2022, attackers launched multiple campaigns to exploit zero-day vulnerabilities in publicly accessible network appliances, focusing on WAN-facing services. However, further investigation revealed a complex rootkit, “Cloud Snooper,” and a unique cloud pivoting technique via a misconfigured AWS SSM Agent.

Security Affairs
DECEMBER 2, 2021
The fifth issue added to the list of actively exploited vulnerabilities is the CVE-2020-11261 Improper Input Validation flaw that impacts multiple Qualcomm chipsets. There are indications that CVE-2020-11261 may be under limited, targeted exploitation” reads a note added to the January security bulletin last week.

Krebs on Security
OCTOBER 8, 2020
There’s an old adage in information security: “Every company gets penetration tested, whether or not they pay someone for the pleasure.” ” Many organizations that do hire professionals to test their network security posture unfortunately tend to focus on fixing vulnerabilities hackers could use to break in.

Security Affairs
JANUARY 23, 2025
Cybersecurity and Infrastructure Security Agency (CISA) adds JQuery vulnerability to its Known Exploited Vulnerabilities catalog. Cybersecurity and Infrastructure Security Agency (CISA) added a JQuery persistent cross-site scripting (XSS) vulnerability, tracked as CVE-2020-11023 (CVSS score: 6.9) In jQuery 1.0.3
Security Affairs
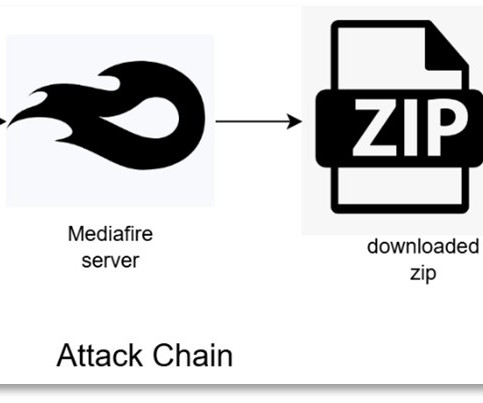
MARCH 28, 2025
The Trojan has been active since 2016, it initially targeted Brazil but expanded to Mexico, Portugal, and Spain since 2020. Forcepoint X-Labs researchers warn of new phishing campaigns targeting Latin America and Europe in new phishing campaigns.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content