Why big data may help you sleep better at night
Tech Republic Security
JANUARY 11, 2020
At CES 2020, Sleep Number debuted its latest smart beds, which feature climate-controlled technology that gathers data while you snooze.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
JANUARY 11, 2020
At CES 2020, Sleep Number debuted its latest smart beds, which feature climate-controlled technology that gathers data while you snooze.

McAfee
DECEMBER 4, 2020
2020 has been a tumultuous and unpredictable year, where we restructured our lives and redefined how we work and interact with each other. Although 2020 has undoubtedly been a year of trials and tribulations, I wanted to share some of McAfee’s top highlights. Ahead of the 2020 U.S. To support today’s U.S. Learn more here.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
SC Magazine
MARCH 29, 2021
Just as the threat landscape evolves, so must the technology used by the cybersecurity community to respond. FINALIST | BEST EMERGING TECHNOLOGY. FINALIST | BEST EMERGING TECHNOLOGY. FINALIST | BEST EMERGING TECHNOLOGY. FINALIST | BEST EMERGING TECHNOLOGY. FINALIST | BEST EMERGING TECHNOLOGY.

The Last Watchdog
MAY 20, 2022
Managed security services (MSS) refer to a service model that enable the monitoring and managing of security technologies, systems, or even software-as-a-service (SaaS) products. billion in 2020.”. The unification revolution of cybersecurity solutions has started – and managed security service providers are leading the way.

Anton on Security
OCTOBER 20, 2022
Why Your Security Data Lake Project Will … Well, Actually … Long story why but I decided to revisit my 2018 blog titled “Why Your Security Data Lake Project Will FAIL!” To remind, decoupled SIEM is where data storage technology (a security data lake, essentially) is built by one vendor while security brains are built by another.

Thales Cloud Protection & Licensing
FEBRUARY 24, 2020
2020 marks the launch of the Thales Data Threat Report-Global Edition for the seventh consecutive year. In previous years, we have discussed the efforts of businesses to digitally transform their processes to maintain or gain a competitive advantage and many of these transformative technologies involves moving to the cloud.
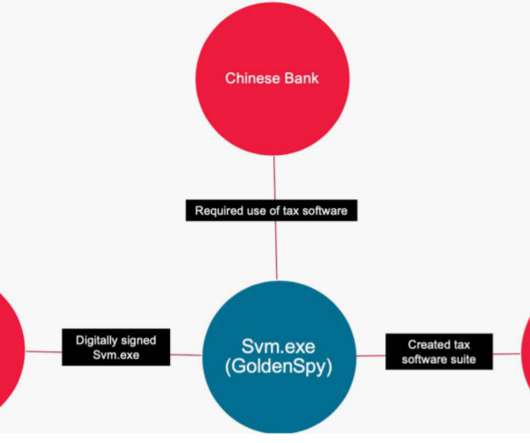
Security Affairs
JUNE 29, 2020
The campaign is active since at least April 2020, but experts found some samples that suggest the attacks begun at least December 2016. In October 2016, Chenkuo Technology announced a partnership with Aisino for “big data cooperation. ” The backdoor is digitally signed by a company named Chenkuo Network Technology.

eSecurity Planet
APRIL 26, 2022
Company Sector Year Status Isovalent Cloud security 2020 Private Illumio Cloud security 2015 Private SignalFx Monitoring 2015 Acquired: Splunk CipherCloud Cloud security 2012 Acquired: Lookout Lookout Mobile security 2011 Private. a16z Investments. PagerDuty Operations performance 2014 NYSE: PD Auth0 Identity management 2014 Acquired: Okta.

CyberSecurity Insiders
OCTOBER 20, 2021
Gartner defines XDR, or eXtended Detection and Response, as “a unified security incident detection and response platform that automatically collects and correlates data from multiple proprietary security components.” SIEMs are open-ended technologies, so they are going to be expensive to operate. Defining SIEM.

Cisco Security
MARCH 5, 2021
And according to the Radicati Secure Email Gateway Market Guide 2020, that’s where Cisco Secure Email stands out above the rest. The 2020 guide noted several key strengths that made Cisco a leader. Our cloud native solution options include: API first technology. data loss prevention. the use of global data centers.

Security Affairs
NOVEMBER 14, 2021
In 2020, the number of reports sent to ENISA about cybersecurity incidents saw an increase of 47% compared to the previous year. The level of exposure to cyber threats is increasing to the adoption of emerging technologies such as the Internet of Things (IoT), Artificial Intelligence (AI), big data, and cloud computing.

eSecurity Planet
JANUARY 28, 2021
billion in funding in 2020. This list was developed based on multiple factors, among them growth rates, recent funding rounds and innovations in new and emerging technologies. In September 2020, Axis Security raised $32 million in Series B funding, for a total of $49 million over three rounds. Jump ahead: Axis Security.

The Last Watchdog
JUNE 2, 2021
The amount of data in the world topped an astounding 59 zetabytes in 2020, much of it pooling in data lakes. We’ve barely scratched the surface of applying artificial intelligence and advanced data analytics to the raw data collecting in these gargantuan cloud-storage structures erected by Amazon, Microsoft and Google.

Thales Cloud Protection & Licensing
APRIL 25, 2022
How to protect healthcare and life-sciences data from a cyber attack pandemic. Once slow to adopt new technologies, healthcare-related industries have been rapidly embracing digitalization to enable patient-centric care that is more effective for patients and safer for patients, healthcare professionals and researchers.
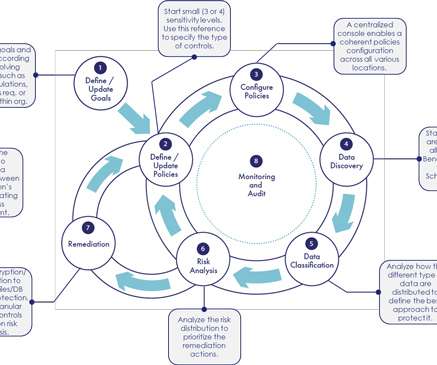
Thales Cloud Protection & Licensing
MARCH 16, 2021
The amount of data created is forecasted to grow and be spread in a wide diverse ecosystem: the cloud, on premises, in data lakes and big data. In addition, according to the “2020 Year End Report of Data Breach ” from QuickView, the number of records compromised in 2020 revealed a 141% increase compared to 2019.

Security Boulevard
FEBRUARY 24, 2021
Now, cybersecurity may just be the most important aspect of financial technology (fintech) in the modern world. With 2020 being the worst year on record in terms of files exposed in data breaches , a thorough security approach is necessary to combat modern dangers. Multi-cloud data storage.
Jane Frankland
JANUARY 22, 2021
Most people know that technology creates more jobs than any other industry and that digital is the golden thread that runs across all industries. According to the World Economic Forum, at least 133 million new roles are set to emerge globally in the next year as a result of the new division of labour between human ingenuity and technology.

NSTIC
JANUARY 28, 2020
As we celebrate Data Privacy Day 2020, let’s take a moment to reflect on the changes to privacy as a discipline — not just here at NIST, but as a community. The idea of privacy risk management was just a twinkle in our collective eye

eSecurity Planet
JANUARY 27, 2022
Gartner analyst Pete Shoard advised that being as clear as possible about your needs is key to selecting the right service, noting that offerings can range from managing a single technology to sharing the responsibility for operating a security platform to full outsourcing of security operations. DXC Technology. Secureworks.

CyberSecurity Insiders
JUNE 15, 2021
He is a recognized expert in cybersecurity and big data. Prior to founding Silverfort, Yaron served as a big data consultant for Cisco, and also worked on big data analytics and machine learning algorithm projects at Microsoft. in Computer Science from the Technion – Israel Institute of Technology.

Thales Cloud Protection & Licensing
FEBRUARY 28, 2022
According to ABI Research 41% of vehicles sold in 2020 are considered “connected,” and the number goes to 91% in the United States. Employing big data analytics to gather insights to capitalize on customer behavior, understand product performance, and predict failures. More data in more places means more risks.

Thales Cloud Protection & Licensing
MARCH 1, 2019
The report shows that 97% of enterprises adopting digital transformation technologies use sensitive data within these new environments, but only 30% use encryption to protect data in these environments. Enterprises must focus on the protection of the sensitive data itself, wherever it goes.

SecureWorld News
SEPTEMBER 14, 2021
This example might seem extreme, but for some parents this exact scenario played out after hackers managed to steal their child’s data. 2020 saw a record number of cyberattacks—and threats for school, university, and other educational institutes are growing each day. Unfortunately, there is no perfect profile for a cybercriminal.

Security Boulevard
OCTOBER 20, 2022
Long story why but I decided to revisit my 2018 blog titled “Why Your Security Data Lake Project Will FAIL!” Just as I did when I revisited my 2015 SOC nuclear triad blog in 2020 , I wanted to check if my opinions, views and positions from that time are still correct (spoiler: not exactly…). we are in 2022. Hi Alexes!).

McAfee
OCTOBER 14, 2020
However, the ability to alter reality has taken a leap forward with “deepfake” technology which allows for the creation of images and videos of real people saying and doing things they never said or did. Detrimental lies are not new. Even misleading headlines and text can fool a reader. How are Deepfakes Created?

eSecurity Planet
OCTOBER 11, 2022
Whether it’s studying the performance of your direct competitors, using predictive analytics to determine what the future may hold for your industry, or analyzing employee performance and making optimization decisions based on that information, the entire point is to take data in and use it to make better-informed decisions.

eSecurity Planet
JUNE 17, 2021
Started in 1987, the telecommunications provider has become a multinational technology whale. At just $42M, Huawei added HexaTier’s patented technology offering cloud-based databases (DBaaS) security via a reverse proxy on endpoints. IBM comes with a presence in 170 countries and is the second oldest vendor on our list.
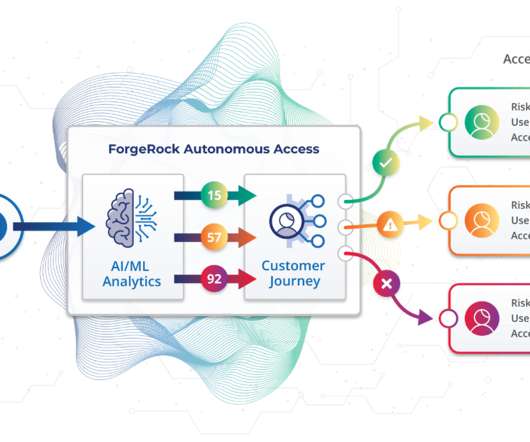
Security Boulevard
JUNE 7, 2022
Though the tools and technologies have improved enormously in the last couple of decades, enterprises remain under attack. As people conduct more and more business online — both in their personal and professional lives — cybercrime has become big business, more organized and well-funded than ever. billion breached records.

CyberSecurity Insiders
JANUARY 17, 2022
The agreement covers the North America, Latin America, and Caribbean regions, building off the momentum and success of a similar SCA that was executed in Europe in 2020. The SCA demonstrates a committed investment in cloud technology that will enable partners to expand their offerings to reach larger markets.

Thales Cloud Protection & Licensing
AUGUST 15, 2019
state to pass its own data privacy law. 1, 2020, and July 2, 2020 and that that the Attorney General is not allowed to bring enforcement actions under the CCPA until the earlier of six months after the final regulations are published. 3) Fortunately, there is a lot of overlap in data security and privacy requirements.
Thales Cloud Protection & Licensing
NOVEMBER 2, 2020
Strategies and Best Practices for Protecting Sensitive Data. Tue, 11/03/2020 - 06:29. Data has been migrating from traditional data centers to third-party hosted environments, private/public cloud infrastructures and Software-as-a-Service (SaaS) applications by leaps and bounds.

Pen Test
OCTOBER 12, 2023
This specialized form of testing has emerged as a crucial tool for evaluating the security of wireless networks and assessing their resilience against potential cyber-attacks (Davis & Brown, 2020). It underscores the vital role it plays in fortifying the burgeoning landscape of wireless technologies. What is Radio Frequency (RF)?

McAfee
AUGUST 27, 2020
But before the bad guys can launch an attack, our prevention technology comes into play to prevent ransomware from infecting the endpoint in question. McAfee leverages an integrated technology stack that includes machine learning, exploit prevention, behavioral blocking and dynamic application containment. The Power of Big Data.

CyberSecurity Insiders
JUNE 11, 2021
million in cash from this call for proposals, the second call the Institute has released since the organization’s launch in March 2020. Data-Driven Control and Coordination of Smart Converters for Sustainable Power System Using Deep Reinforcement Learning (Qianwen Xu, KTH Royal Institute of Technology). Shankar Sastry, C3.ai

Spinone
JANUARY 21, 2018
With the technologies in cloud computing moving so fast, and adoption rates increasing rapidly, we can expect to see some exciting developments in 2017. There has been criticism in recent years about the energy requirements of massive data centres and how adopting cloud technology may not be as green as it first seems.

Spinone
NOVEMBER 15, 2016
Information Technology research and advisory company, Gartner, presented its top predictions for the cybersecurity industry for 2017 earlier this year. It’s clear that more funds and resources must be dedicated to cybersecurity, with cybersecurity spending expecting to hit $170 billion by 2020.

CyberSecurity Insiders
MAY 7, 2021
xMatters’ technology will complement our successful IT alerting business, providing a natural combination to further strengthen our CEM for Digital solution. based health care providers, and 7 of the 10 largest technology companies in the world. Everbridge is based in Boston with additional offices in 20 cities around the globe.

CyberSecurity Insiders
JANUARY 20, 2022
The number of successful ransomware attacks, which encrypt computers until victims pay the attackers to unlock their data, surged last year. The number of successful ransomware attacks, which encrypt computers until victims pay the attackers to unlock their data, surged last year.

Thales Cloud Protection & Licensing
NOVEMBER 4, 2020
Thu, 11/05/2020 - 06:52. Companies and organizations, whether in the public or in the private sector, are re-establishing their business in the era of information and data revolution. businesses are taking advantage of digital technologies like cloud, mobile, and IoT to digitally transform their operations. Labelled Industry 4.0,
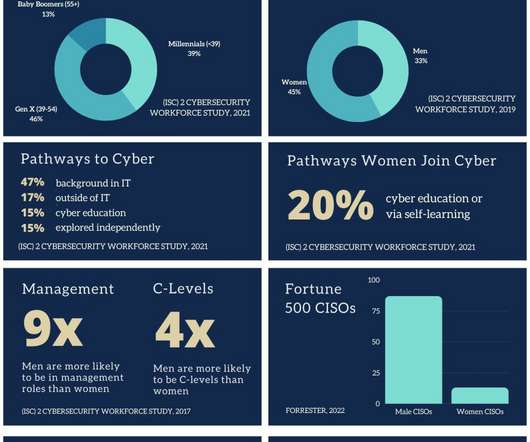
Jane Frankland
JUNE 15, 2022
I’d been instructed by one of my coaches to make some data “pop” so I could get through to people who consumed info more visually. As I was collating the data from numerous sources, I was struck by a few things. Firstly, there were big data gaps. Thirdly, how old some of the data was. DATA SOURCE.

eSecurity Planet
JANUARY 21, 2021
Archer was named a Leader in Gartner’s 2020 Magic Quadrant for IT risk management and IT vendor risk management tools. Additionally, Forrester named it a Contender in its Q1 2020 GRC Wave. Like other competitive GRC solutions, it speeds the process of aggregating and mining data, building reports, and managing files.

eSecurity Planet
JANUARY 21, 2021
Archer was named a Leader in Gartner’s 2020 Magic Quadrant for IT risk management and IT vendor risk management tools. Additionally, Forrester named it a Contender in its Q1 2020 GRC Wave. Like other competitive GRC solutions, it speeds the process of aggregating and mining data, building reports, and managing files.

The Last Watchdog
MARCH 3, 2022
The convergence of information technology (IT) and operational technology (OT) is a double-edged sword for critical infrastructure sectors – despite all its benefits, IT/OT convergence is not without its risks. According to the Identity Theft Resource Center, ransomware attacks doubled in 2020 and again in 2021.

Security Boulevard
JUNE 1, 2021
NCSC warned UK Smart Cities will be highly targeted by hackers, and as such, councils need to ensure they are properly prepared as they rollout increasingly connected and technology-reliant infrastructure. DarkSide is a ransomware-as-a-service platform, first seen advertised in August 2020 on Russian language hacking forums.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content