ZuoRAT Malware Is Targeting Routers
Schneier on Security
JUNE 30, 2022
Dubbed ZuoRAT, the remote access Trojan is part of a broader hacking campaign that has existed since at least the fourth quarter of 2020 and continues to operate.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
JUNE 30, 2022
Dubbed ZuoRAT, the remote access Trojan is part of a broader hacking campaign that has existed since at least the fourth quarter of 2020 and continues to operate.

McAfee
AUGUST 23, 2020
“Features are a nice to have, but at the end of the day, all we care about when it comes to our web and cloud security is architecture.” – said no customer ever. As a result, organizations are coming around to the realization that digital transformation demands a corresponding network and security architectural transformation.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CyberSecurity Insiders
MAY 18, 2022
In 2020, the SolarWinds supply chain attack opened backdoors into thousands of organizations (including government agencies) that used its services, while late last year, the far-reaching Log4J exploit exploded onto the scene. So why aren’t more organizations taking advantage of protective DNS? The issue likely comes down to awareness.
Security Affairs
MARCH 16, 2021
The shell script downloads several Mirai binaries that were compiled for different architectures, then it executes these binaries one by one. “The attacks are still ongoing at the time of this writing. “The attacks are still ongoing at the time of this writing.
Security Affairs
NOVEMBER 1, 2021
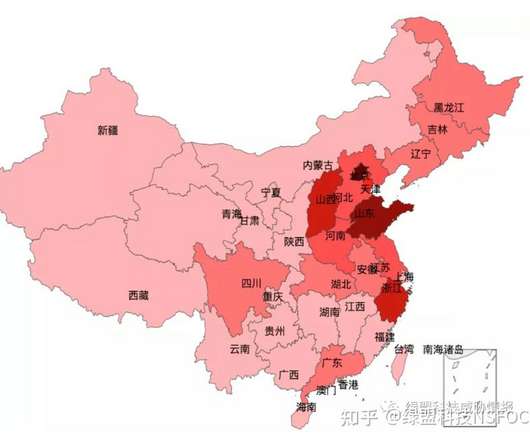
On 2020-01-02, CNCERT reported that “the number of Bot node IP addresses associated with this botnet exceeds 5 million. The botnet leverages a robust architecture based on a combination of third-party services, P2P, and Command & Control servers.

eSecurity Planet
SEPTEMBER 3, 2022
For example, the 2016 DDoS attack on the Dyn managed domain name service (DNS) caused the DNS service to fail to respond to legitimate DNS inquiries and effectively shut down major sites such as PayPal, Spotify, Twitter, Yelp, and many others. Also read: How to Secure DNS. In 2020 the U.S. Types of DDoS Attacks.

eSecurity Planet
SEPTEMBER 24, 2021
Architecture: Identifies network resources and connectivity requirements for agents. InsightIDR comes with several dashboard views that give administrators visibility into network activity like firewall traffic, blocked traffic by port and IP, total DNS traffic, and DNS queries. Rapid7 Competitors. The Forrester Wave.

eSecurity Planet
JANUARY 14, 2022
NetScout’s latest Threat Intelligence Report found more DDoS attacks in the first half of 2021 compared to the whole of 2020. Since 2020, through various waves of DDoS extortion campaigns we’ve witnessed, this trend holds true. It is architected for nonstop DNS availability and high performance, even across the largest DDoS attacks.

SC Magazine
MAY 3, 2021
Jeremy Brown helped Trinity Cyber develop counter maneuvers for a DNS exploit requiring deep parsing of a certain kind of traffic, deploying it to all clients in less than two days. They developed a powerful new approach to intrusion prevention system as-a-service, delivered through a service edge architecture and patent-pending technology.

ForAllSecure
MARCH 24, 2020
or-later Section: utils Architecture: x86_64 Installed-Size: 11797 Filename: attr_2.4.48-2_x86_64.ipk The modification to /etc/hosts is required to emulate a man-in-the-middle (or compromised DNS) situation. both released on February 1st 2020. A typical entry in Packages looks like this: Package: attr Version: 2.4.48-2

eSecurity Planet
MAY 19, 2022
Already a leading SD-WAN pick, the HPE subsidiary boosted its market position with acquisitions of security vendor Cape Networks in 2018 and WAN specialist Silver Peak Systems in 2020. infographic from Cisco laying out its SD-WAN architecture. Features: Juniper Session Smart Routers and SASE. Features: Versa SASE.

eSecurity Planet
DECEMBER 23, 2020
The COVID-19 pandemic of 2020 has forced enterprises of all sizes and industries to adopt new work approaches that keep employees safe at home while ensuring productivity and security. To accommodate this increased demand, organizations can optimize VPN server use by using traffic steering at the DNS layer.
Security Affairs
OCTOBER 20, 2021
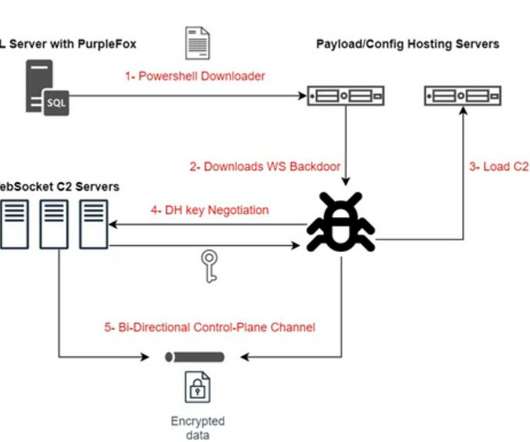
The payload fetched by the PowerShell targets 64-bit architecture systems, it is a long script consisting of three components: Tater (Hot Potato – privilege escalation) PowerSploit Embedded exploit bundle binary (privilege escalation). Most of the servers are located in China and belong to the infrastructure of the PurpleFox botnet.

McAfee
SEPTEMBER 14, 2021
Inspecting the File (COFF) header, we observed the file’s compilation timestamp: TimeDateStamp: 05/12/2020 08:23:47 – Date and time the image was created. The PlugX families we observed used DNS [ T1071.001 ] [ T1071.004 ] as the transport channel for C2 traffic, in particular TXT queries. malware: Mozilla/5.0 Windows NT 6.3;

SecureList
MAY 31, 2021
While investigating attacks on the defense industry in mid-2020, we were able to observe the complete life-cycle of an attack, uncovering more technical details and links to the group’s other campaigns. Our recommendations for staying safe from attacks using these vulnerabilities can be found here.

ForAllSecure
MARCH 24, 2020
or-later Section: utils Architecture: x86_64 Installed-Size: 11797 Filename: attr_2.4.48-2_x86_64.ipk The modification to /etc/hosts is required to emulate a man-in-the-middle (or compromised DNS) situation. both released on February 1st 2020. A typical entry in Packages looks like this: Package: attr Version: 2.4.48-2

ForAllSecure
MARCH 25, 2020
or-later Section: utils Architecture: x86_64 Installed-Size: 11797 Filename: attr_2.4.48-2_x86_64.ipk The modification to /etc/hosts is required to emulate a man-in-the-middle (or compromised DNS) situation. both released on February 1st 2020. A typical entry in Packages looks like this: Package: attr Version: 2.4.48-2

eSecurity Planet
JULY 30, 2021
The basic idea is to segment off parts of the network, especially the most sensitive parts, and wall them off with stricter policies and tie them into a zero-trust architecture. For example, Illumio was named a Leader by Forrester Research in The Forrester Wave: Zero Trust eXtended (ZTX) Ecosystem Platform Providers, Q3 2020.
Cisco Security
DECEMBER 8, 2022
In their 2021 Internet Crime Report , the Internet Crime Complaint Center (IC3) said that Non-Payment / Non-Delivery scams such as these led to more than $337 million in losses, up from $265 million in 2020. According to Cisco Umbrella , many of the sites asking for credit card details are known phishing sites, or worse, host malware.

eSecurity Planet
MAY 2, 2024
50,000 DDoS attacks on public domain name service (DNS) resolvers. 553% increase in DNS Flood attacks from 1H 2020 to 2H 2023. DDoS attacks on single networks or websites render them unavailable, but DDoS attacks on DNS resolvers bring down all networks and websites using that DNS resource.

SC Magazine
JULY 12, 2021
29, 2020, in Houston. Between the DNS attacks and ongoing ransomware scourge, it’s beyond time for providers to seek more creative responses to cyber challenges even with limited budgets, in combination with participation in threat-sharing programs and while relying on free or low-cost resources. Photo: Go Nakamura/Getty Images).

Security Affairs
NOVEMBER 29, 2019
Group-IB, has analyzed key recent changes to the global cyberthreat landscape in the “Hi-Tech Crime Trends 2019/2020” report. The new “ Hi-Tech Crime Trends 2019/2020 ” report describes attacks on various industries and critical infrastructure facilities, as well as campaigns aimed at destabilization of the Internet in certain countries.

McAfee
FEBRUARY 4, 2021
And they didn’t even give it a DNS look up until almost a year later. But the code application 2019 was weaponization in 2020. The majority of this tactic took place from a C2 perspective through the partial exfiltration being done using DNS. Ismael: Yep, absolutely.

SecureList
SEPTEMBER 21, 2023
Botnet based on Medusa, working since 2020. See translation Will buy 0day/1day RCE in IoT Escrow See translation Hi, I want to buy IoT exploits with devices located in Korea Any architecture There are also offers to purchase and sell IoT malware on dark web forums, often packaged with infrastructure and supporting utilities.

The Last Watchdog
OCTOBER 19, 2021
This sketch by Joanna Rutkowska, one of the founding scientists, is a visualization of the groundbreaking data management architecture Wildland proposes. Users can create bridges and share part of their file systems with others without relying on any centralized databases or lookup systems like DNS, for example. in June 2021.

Hacker Combat
OCTOBER 13, 2021
’ Wiz was established in January 2020 by Assaf Rappaport – CEO, Roy Reznik, Ami Luttwak, and Yinon Costica. Wiz has built a platform that companies can utilize to scan their cloud structures and workloads, evaluate cloud risk factors and architecture, determine critical risks, and beef up their cloud surroundings.

eSecurity Planet
AUGUST 11, 2023
Redundant architecture and tools should not be eliminated until the SASE solution has been thoroughly tested. Overcoming Edge Computing Risks This article was originally written by Paul Shread on November 24, 2020 and revised by Chad Kime on August 11, 2023. For additional reading: Top SASE Solutions What Is Edge Security?

McAfee
FEBRUARY 5, 2021
Ephemeral C2 servers and single-use DNS entries per asset (not target enterprise) were some of the more well-planned (yet relatively simple) behaviors seen in the Sunburst attack. This blog is a summary of the SOCwise Conversation on January 25th 2020. Watch for the next one! . Additional Analysis into the SUNBURST Backdoor.

eSecurity Planet
JANUARY 26, 2022
Founded in 2010 by veteran SaaS and DevOps industry leaders, Datadog specializes in optimizing the service-oriented architecture, helping organizations monitor user journeys and explore service relationships. Catchpoint Features. Administrators can group traffic by container , team, or office and filter data by tag, device, or host.

SecureList
MAY 1, 2023
uses Transformers (the same architecture that powers ChatGPT) to achieve an even lower FPR. URL: [link] Organization: Adobe Reasoning: The domain name ‘duckdns.org’ is a free dynamic DNS provider which is often used by cyber criminals for hosting phishing sites or other malicious content. ROC curve from Le et al.,

McAfee
DECEMBER 22, 2021
Attack Chain and Defensive Architecture. The file runs on Linux machines and has been uploaded on Virus Total for the first time in December 2020. identify outbound communication attempts to known C2 domains through DNS or Web traffic. KB95091: McAfee Enterprise coverage for Apache Log4j CVE-2021-44228 Remote Code Execution.

Fox IT
JUNE 2, 2020
Publicly discovered in late April 2020, the Team9 malware family (also known as ‘Bazar [ 1 ]’) appears to be a new malware being developed by the group behind Trickbot. Next, the loader fingerprints the Windows architecture. Once the Windows architecture has been identified, the loader carries out the download. Introduction.

SecureList
APRIL 27, 2022
While we were unable to obtain the same results by analyzing the CERT-UA samples, we subsequently identified a different WhiteBlackCrypt sample matching the WhisperKill architecture and sharing similar code. ToddyCat, a relatively new APT actor, is responsible for multiple attacks detected since December 2020. in June 2021.

CyberSecurity Insiders
JANUARY 31, 2021
However, that number has risen dramatically in 2020, a trend that businesses and individuals alike must NOT ignore. That number spiked significantly in 2020, where a Mid-Year Threat Landscape Report 2020 from Bitdefender shows a 715% year over year increase in detected and blocked ransomware attacks in 2020.

eSecurity Planet
SEPTEMBER 26, 2023
Pricing & Delivery Pricing for Versa’s SASE product was originally called Versa Secure Access and announced in 2020 to start at $7.50 IT teams can still apply policies, receive reports, and view analytics using the Versa Titan Portal. per user per month without limitation for the number of devices.

eSecurity Planet
MARCH 10, 2021
The least common of SQL injection attacks, the out-of-band method relies on the database server to make DNS or HTTP requests delivering data to an attacker. . . . With the big news of supply chain compromises in 2020 , many are looking to NIST and other industry-standard security checklists to harden operating systems and applications. .

Fox IT
JUNE 23, 2020
WastedLocker is a new ransomware locker we’ve detected being used since May 2020. We believe it has been in development for a number of months prior to this and was started in conjunction with a number of other changes we have seen originate from the Evil Corp group in 2020. WastedLocker. CobaltStrike C&C Domains.

Kali Linux
FEBRUARY 23, 2021
kali3-amd64 NOTE: The output of uname -r may be different depending on the system architecture. This edition brings enhancements of existing features, and is ready to be downloaded or upgraded if you have an existing Kali Linux installation. The summary of the changelog since the 2020.4 " VERSION_ID="2021.1"

SecureList
OCTOBER 19, 2021
EMBEDDED MODULE PE timestamp:2020-09-17 InternalName:<payload32.dll> It retrieves the DNS names of all the directory trees in the local computer’s forest. EMBEDDED EXE MODULE timestamp:2020-04-23 InternalName:<none>AliasName:mailCollector. This module gathers basic system information. vpnDll32.

Security Boulevard
JANUARY 20, 2022
Overlap of Passive DNS resolution of domain observed on current attack infrastructure with the IP used by Molerats APT group in the past. Additionally, the subdomain “www.msupdata.com” also has a Passive DNS resolution to IP 185.244.39[.]165 Sends processor architecture and computer name. Attack flow. Data from Local System.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content