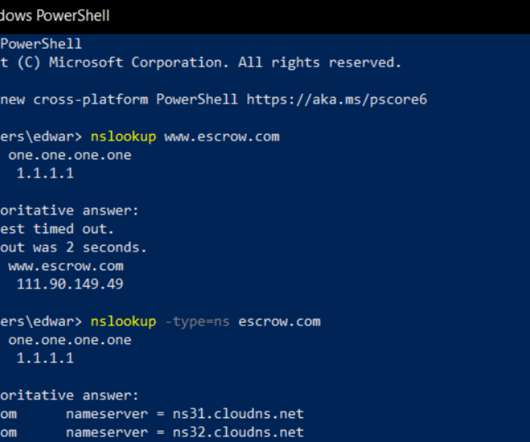
Phish of GoDaddy Employee Jeopardized Escrow.com, Among Others
Krebs on Security
MARCH 31, 2020
The employee involved in this incident fell victim to a spear-fishing or social engineering attack. In cases where passwords are used, pick unique passwords and consider password managers. Any actions done by the threat actor have been reverted and the impacted customers have been notified.















Let's personalize your content