This Service Helps Malware Authors Fix Flaws in their Code
Krebs on Security
MAY 18, 2020
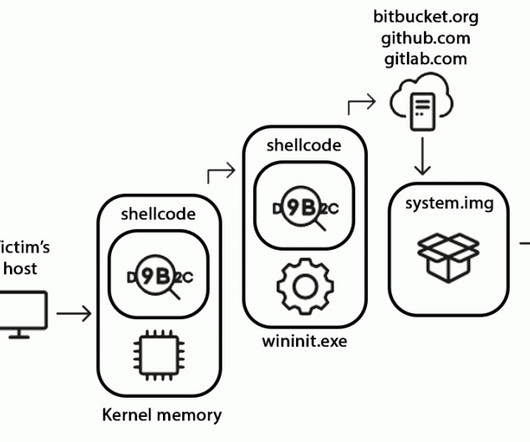
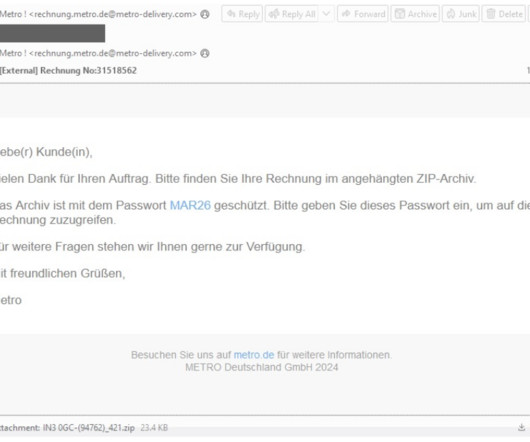
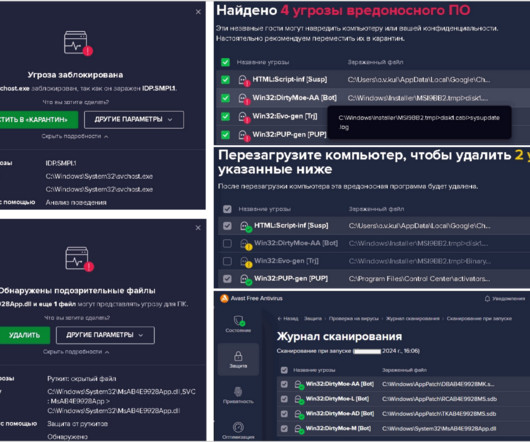
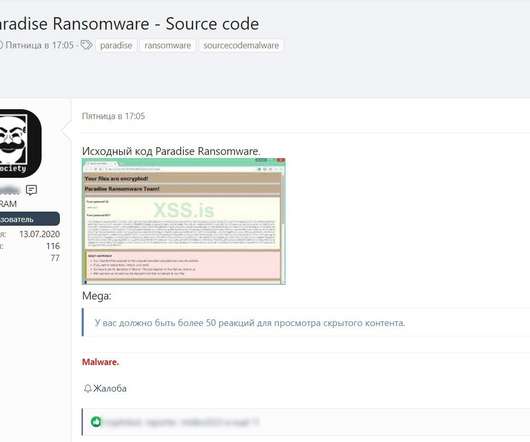
Almost daily now there is news about flaws in commercial software that lead to computers getting hacked and seeded with malware. Here’s a look at one long-lived malware vulnerability testing service that is used and run by some of the Dark Web’s top cybercriminals. is cybercrime forum.



























Let's personalize your content