Ransomware: 8 Things That You Must Know
Joseph Steinberg
APRIL 6, 2021
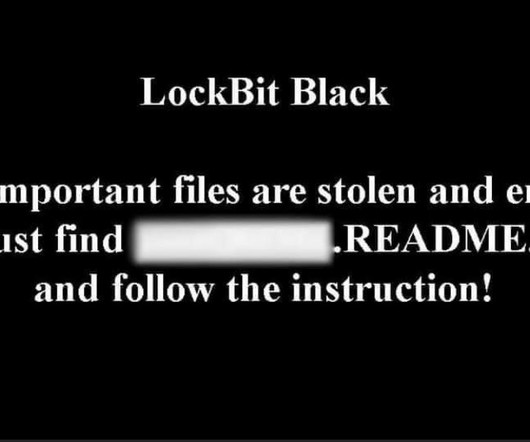
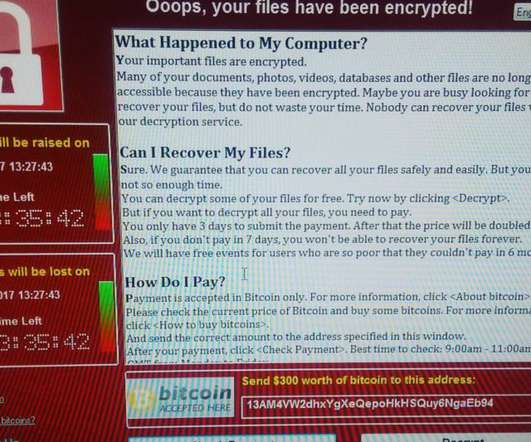
Ransomware comes in multiple flavors – sometimes involving far more than just the unauthorized encryption of data. Remember to keep backups disconnected from your computer and network so that if any ransomware (or other malware) gets onto the network it cannot infect the backups.











































Let's personalize your content