Breach Exposes Users of Microleaves Proxy Service
Krebs on Security
JULY 28, 2022
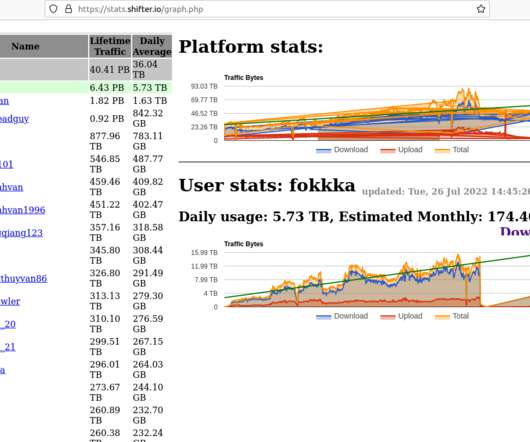
The service, which accepts PayPal, Bitcoin and all major credit cards, is aimed primarily at enterprises engaged in repetitive, automated activity that often results in an IP address being temporarily blocked — such as data scraping, or mass-creating new accounts at some service online. Which hints at a possible BOTNET. “Online[.]io
























Let's personalize your content