‘Satori’ IoT Botnet Operator Pleads Guilty
Krebs on Security
SEPTEMBER 3, 2019
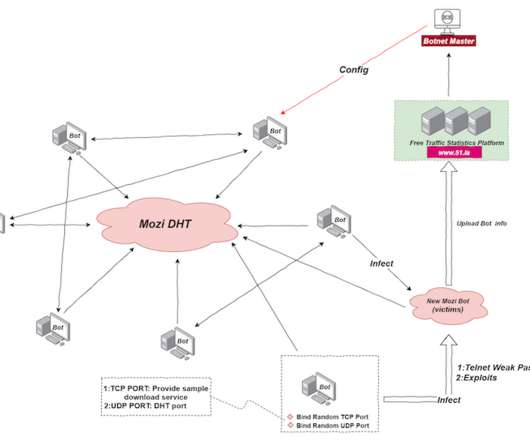
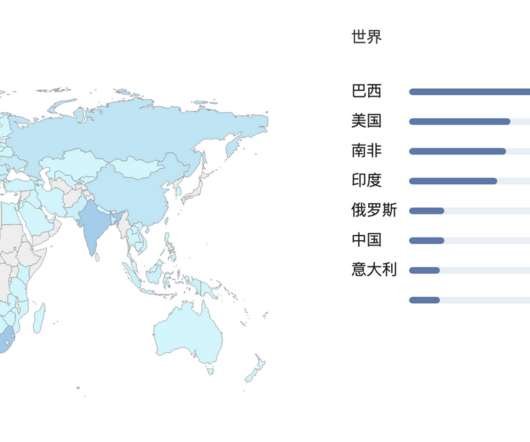
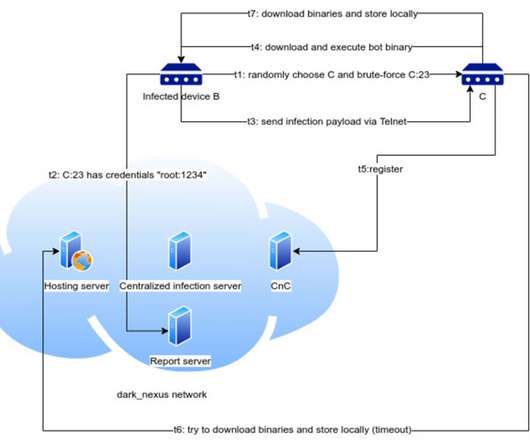
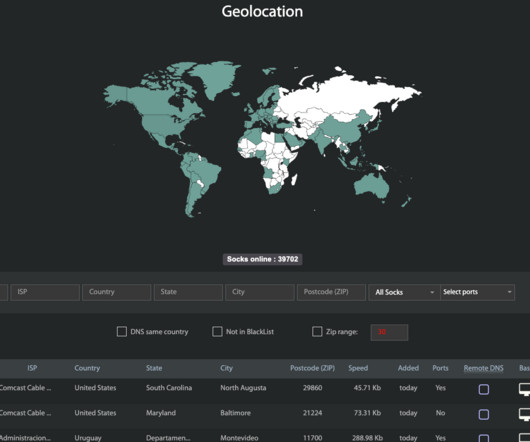
has pleaded guilty to federal hacking charges tied to his role in operating the “ Satori ” botnet, a crime machine powered by hacked Internet of Things (IoT) devices that was built to conduct massive denial-of-service attacks targeting Internet service providers, online gaming platforms and Web hosting companies.

































Let's personalize your content