Another 0-Day Looms for Many Western Digital Users
Krebs on Security
JULY 2, 2021
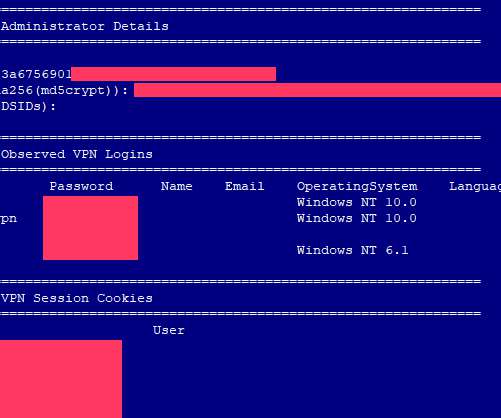
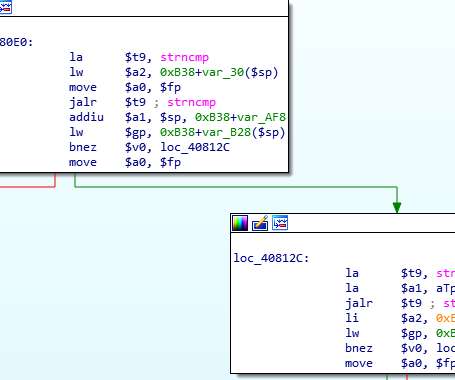
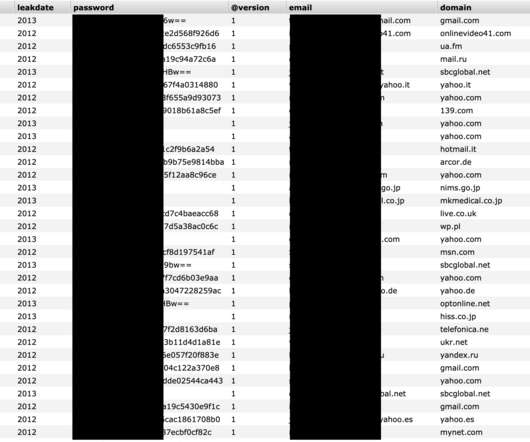
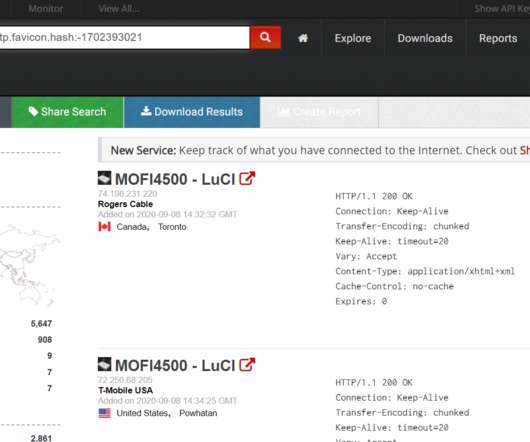
Countless Western Digital customers saw their MyBook Live network storage drives remotely wiped in the past month thanks to a bug in a product line the company stopped supporting in 2015, as well as a previously unknown zero-day flaw. “We strongly encourage moving to the My Cloud OS5 firmware,” the statement reads.


































Let's personalize your content