Chinese hackers exploited a Trend Micro antivirus zero-day used in Mitsubishi Electric hack
Security Affairs
JANUARY 25, 2020
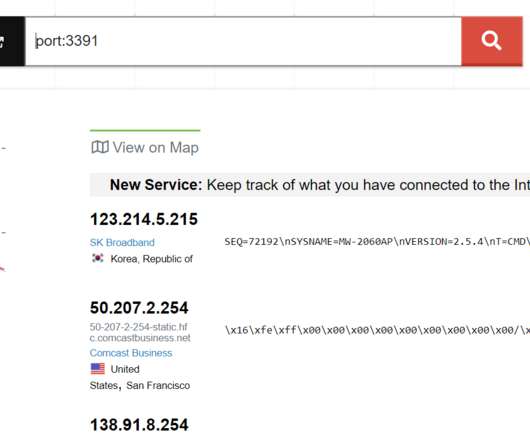
Chinese hackers have exploited a zero-day vulnerability the Trend Micro OfficeScan antivirus in the recently disclosed hack of Mitsubishi Electric. Now ZDNet has learned from sources close to the investigation that the Chinese hackers have used a zero-day flaw in the Trend Micro OfficeScan antivirus in the attack on Mitsubishi Electric.

































Let's personalize your content