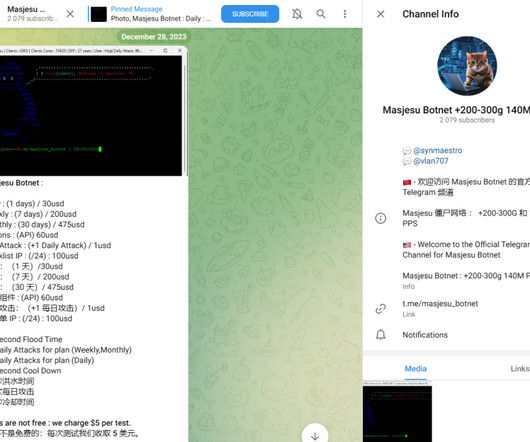
XorBot Botnet Resurfaces with Advanced Evasion and Exploits, Threatens IoT Devices
Penetration Testing
NOVEMBER 27, 2024
NSFOCUS has identified a resurgence of the XorBot botnet, a potent threat to Internet of Things (IoT) devices worldwide.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Penetration Testing
NOVEMBER 27, 2024
NSFOCUS has identified a resurgence of the XorBot botnet, a potent threat to Internet of Things (IoT) devices worldwide.

Security Affairs
SEPTEMBER 21, 2020
House of Representatives passed the IoT Cybersecurity Improvement Act, a bill that aims at improving the security of IoT devices. House of Representatives last week passed the IoT Cybersecurity Improvement Act, a bill designed to improve the security of IoT devices. Mark Warner (D-Va.) Pierluigi Paganini.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
OCTOBER 13, 2020
The number of sensors and smart devices connected to the internet is exponentially rising, which are the 5 Major Vulnerabilities for IoT devices. If you take a look at the global market for IoT, you can easily spot the trend. IoT devices are exposed to cybersecurity vulnerabilities. IoT is a complicated concept.

Security Affairs
JULY 28, 2020
How to hack IoT & RF Devices with BürtleinaBoard. Few months ago I have presented #FocacciaBoard : a similar multipurpose breakout board that uses the famous FT232H to handle multiple protocols commonly found in (I)IoT devices (i.e. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->.
Security Affairs
SEPTEMBER 20, 2020
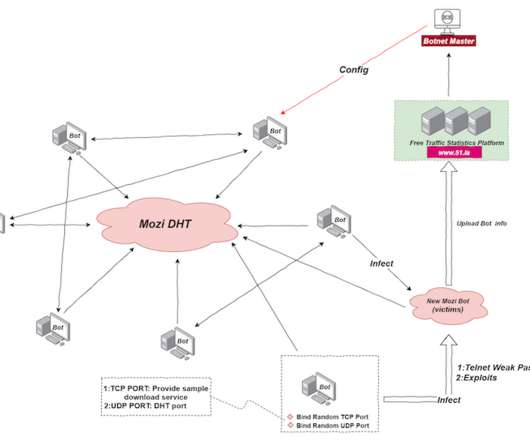
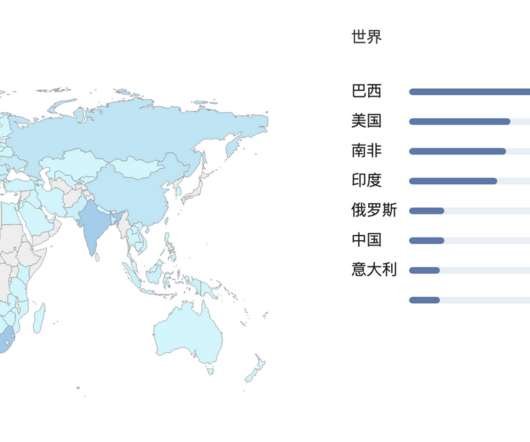
The Mozi botnet accounted for 90% of the IoT network traffic observed between October 2019 and June 2020, IBM reported. Mozi is an IoT botnet that borrows the code from Mirai variants and the Gafgyt malware , it appeared on the threat landscape in late 2019. ” reads the report published by IBM. ” continues the analysis.
Security Affairs
OCTOBER 5, 2020
Security researchers provided technical details about an IoT botnet dubbed Ttint that has been exploiting two zero-days in Tenda routers. Security researchers at Netlab, the network security division Qihoo 360, have published a report that details an IoT botnet dubbed Ttint. Pierluigi Paganini.
Security Affairs
MAY 5, 2020
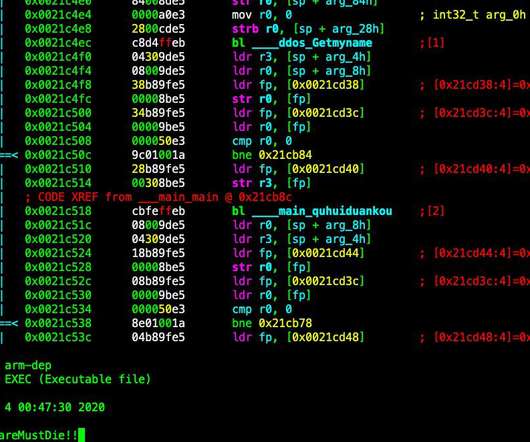
Security researchers spotted a new piece of DDoS bot dubbed Kaiji that is targeting IoT devices via SSH brute-force attacks. Last week, the popular security researcher MalwareMustDie and the experts at Intezer Labs spotted a new piece of malware dubbed Kaiji, that is targeting IoT devices via SSH brute-force attacks.

Security Affairs
MARCH 28, 2019
Shodan IoT search engine announced the launch of a new service called Shodan Monitor designed to help organizations to maintain track of systems connected to the Internet. Shodan Monitor is a precious tool for organizations that can determine their surface of attack assessing their Internet-exposed systems. Pierluigi Paganini.

Security Affairs
DECEMBER 21, 2018
2018 was the year of the Internet of Things (IoT), massive attacks and various botnets hit smart devices, These are 5 IoT Security Predictions for 2019. IoT Attacks in 2018. Do the increased attacks mean the industry is becoming accustomed to IoT cyber attacks? Insights from VDOO’s leadership.

Security Affairs
JANUARY 19, 2020
The availability online of a new collection of Telnet credentials for more than 500,000 servers, routers, and IoT devices made the headlines. The list appears to be the result of an Internet scan for devices using default credentials or easy-to-guess passwords. 33000+ telnet credentials of IoT devices exposed on pastebin.
Security Affairs
FEBRUARY 8, 2020
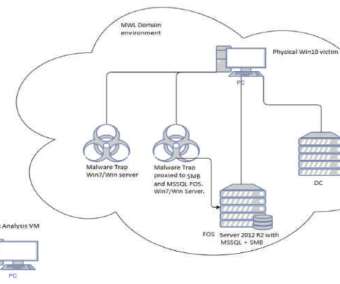
Hackers have infected with a piece of malware some IoT devices running Windows 7 designed by three of the world’s largest manufacturers. Security experts from TrapX reported that some IoT devices running Windows 7 have been infected with a piece of malware, is it a supply chain attack? Pierluigi Paganini.

Security Affairs
OCTOBER 22, 2018
Researchers found that one of the most popular Internet of Things real-time operating system, FreeRTOS, is affected by serious vulnerabilities. Researchers at Zimperium’s zLabs team have found that one of the most popular Internet of Things real-time operating system, FreeRTOS , is affected by serious vulnerabilities. Information Leak.

Thales Cloud Protection & Licensing
NOVEMBER 6, 2019
As most of us know, IoT devices are on the rise in enterprise networks. According to McKinsey & Company , the proportion of organizations that use IoT products has grown from 13 percent in 2014 to 25 percent today. The issue is that these tens of billions of new devices will likely amplify the inherent security risks of IoT.
Security Affairs
JUNE 15, 2020
Attackers could leverage a compromised identifier to use mobile Internet at the legitimate user’s expense and carry out fraud and impersonation, Attackers can also hijack user session data containing relevant identifiers (e.g., phone number) of a real subscriber and impersonate him to access the Internet. Pierluigi Paganini.

Security Affairs
SEPTEMBER 30, 2019
After 2 years of waiting, MalwareMustDie returns with an excellent page of malware analysis of a new IoT malware: Linux/AirDropBot. The beginning of the story: another IoT malware in the wild? Coming to the core topic: IoT botnet threat and their ecosystem.

Security Affairs
MAY 5, 2019
Hacker “Subby” brute-forces the backends of 29 IoT botnets that were using weak or default credentials. A hacker that goes online with the moniker ‘Subby’ took over 29 IoT botnets in the past few week s with brute-force attacks. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->.

Security Affairs
AUGUST 31, 2019
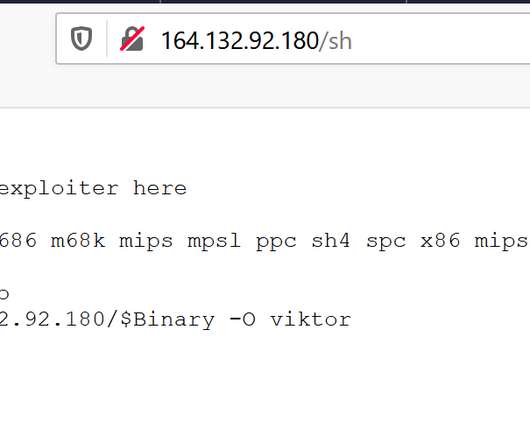
Researchers from WootCloud Labs have uncovered a new IoT botnet named Ares that is targeting Android-based devices. Experts from WootCloud Labs have spotted a new IoT botnet tracked as Ares that is targeting Android-based devices that have a debug port exposed online. IoT #malware branches seen in ???????? .
Security Affairs
MAY 19, 2020
Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->. The post Both Mirai and Hoaxcalls IoT botnets target Symantec Web Gateways appeared first on Security Affairs. Pierluigi Paganini.

Security Affairs
SEPTEMBER 29, 2018
Avast spotted a new IoT botnet, tracked as Torii, that appears much more sophisticated and stealth of the numerous Mirai variants previously analyzed. Security researchers spotted a new IoT botnet, tracked as Torii, that appears much more sophisticated and stealth of the numerous Mirai variants previously analyzed. Pierluigi Paganini.

Krebs on Security
JANUARY 14, 2019
On Friday, a 34-year-old Connecticut man received a whopping 10-year prison sentence for carrying out distributed denial-of-service (DDoS) attacks against a number of hospitals in 2014. dual citizen, admitted attacking an African phone company in 2016, and to inadvertently knocking out Internet access for much of the country in the process.

Security Affairs
SEPTEMBER 19, 2018
Security experts from Kaspersky have published an interesting report on the new trends in the IoT threat landscape. What is infecting IoT devices and how? The researchers set up a honeypot to collect data on infected IoT devices, the way threat actors infect IoT devices and what families of malware are involved.

Security Affairs
DECEMBER 4, 2018
Security experts from Trend Micro discovered that some machine-to-machine (M2M) protocols can be abused to attack IoT and industrial Internet of Things (IIoT) systems. attackers abuse M2M protocols to target IoT and IIoT devices. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->.

Security Affairs
SEPTEMBER 2, 2019
Akamai researcher Larry Cashdollar reported that a cryptocurrency miner that previously hit only Arm-powered IoT devices it now targeting Intel systems. The researchers revealed that one of his honeypots was hit by this IoT malware that targets Intel machines running Linux. “This one seems to target enterprise systems.”

Security Affairs
SEPTEMBER 4, 2019
Kenneth Currin Schuchman (21) from Vancouver, Washington pleaded guilty to creating and operating multiple DDoS IoT botnet , including Satori. Kenneth Currin Schuchman (21) from Vancouver, Washington, aka Nexus Zeta, pleaded guilty to creating and operating multiple DDoS IoT botnets. Pierluigi Paganini.
Krebs on Security
APRIL 18, 2023
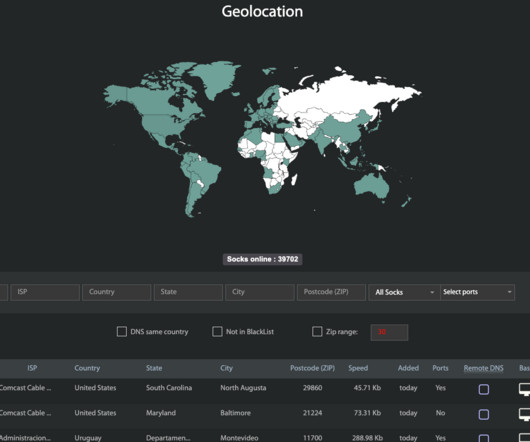
Kilmer said Faceless has emerged as one of the underground’s most reliable malware-based proxy services, mainly because its proxy network has traditionally included a great many compromised “Internet of Things” devices — such as media sharing servers — that are seldom included on malware or spam block lists.

Security Affairs
OCTOBER 23, 2018
Security experts from Sophos Labs have spotted a new piece of IoT malware tracked as Chalubo that is attempting to recruit devices into a botnet used to launch DDoS attacks. The IoT malware ran only on systems with an x86 architecture. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->.

Security Affairs
JUNE 26, 2019
Security experts warn of a new piece of the Silex malware that is bricking thousands of IoT devices, and the situation could rapidly go worse. Silex is not the first IoT malware with this behavior, back in 2017 BrickerBot bricked millions of devices worldwide. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->.
Security Affairs
NOVEMBER 11, 2021
Researchers at AT&T discovered a new BotenaGo botnet that is using thirty three exploits to target millions of routers and IoT devices. BotenaGo is a new botnet discovered by researchers at AT&T that leverages thirty three exploits to target millions of routers and IoT devices. v001 / 3.40(ULM.0)b31 Pierluigi Paganini.
Security Affairs
APRIL 8, 2020
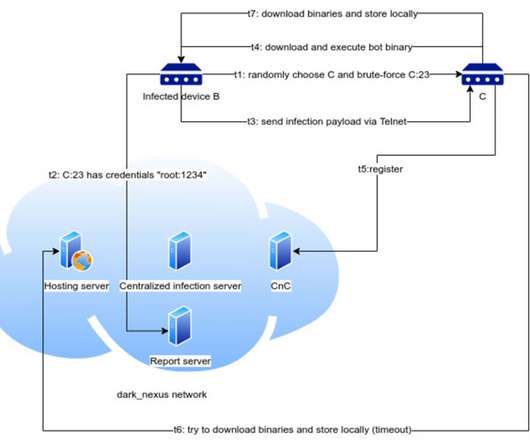
Cybersecurity researchers discovered a new IoT botnet, tracked as Dark Nexux, that is used to launch distributed denial-of-service (DDoS) attacks. Dark Nexux is the name of a new emerging IoT botnet discovered by Bitdefender that is used to launch DDoS attacks. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->.

Security Affairs
SEPTEMBER 10, 2019
A security researcher disclosed zero-day flaws in Telestar Digital GmbH IoT radio devices that could be exploited by remote attackers to hijack systems without any user interaction. Kunz and his colleagues were able to brute-force the IoT radio in just 10 minutes and achieve root access with full privileges. . Pierluigi Paganini.

Security Affairs
NOVEMBER 12, 2018
The author of an IoT botnet is distributing a backdoor script for ZTE routers that also includes his own backdoor to hack script kiddies. A weaponized IoT exploit script is being used by script kiddies, making use of a vendor backdoor account to hack the ZTE routers. Backdooring rival IoT botnet operator can have several purposes.

Security Affairs
OCTOBER 1, 2019
Security Labs discovered a new IOT bot named “GUCCI”. It seems like the IOT botnet is named after an Italian luxury brand of fashion and leather goods. The IOT threat detection engine picked the infection IP has shown below hosting number of bins for different architectures. Figure 4: Gucci Bot – Source of Distribution.

Security Affairs
NOVEMBER 5, 2018
“The group distributes the bot by exploiting a common command injection vulnerability on internet of things (IoT) devices and Linux servers. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->. Pierluigi Paganini.
eSecurity Planet
NOVEMBER 1, 2021
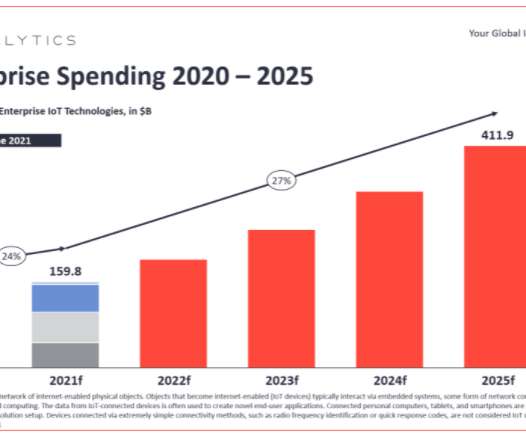
The European Union is poised to place more demands on manufacturers to design greater security into their wireless and Internet of Things (IoT) devices. has made some strides on IoT security at the federal level; it remains to be seen if the EU initiative will spur the U.S. IoT market growth. IoT Security Neglected.

Security Affairs
DECEMBER 24, 2018
Security researchers discovered some flaws in the Twinkly IoT lights that could be exploited display custom lighting effects and to remotely turn off them. ’ ~ Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->.

Krebs on Security
JANUARY 24, 2023
First advertised in the cybercrime underground in 2014, RSOCKS was the web-based storefront for hacked computers that were sold as “proxies” to cybercriminals looking for ways to route their Web traffic through someone else’s device. A copy of the passport for Denis Emelyantsev, a.k.a. Denis Kloster, as posted to his Vkontakte page in 2019.

Security Affairs
APRIL 26, 2019
Experts discovered security flaws in the iLnkP2P peer-to-peer (P2P) system that exposes millions of IoT devices to remote attacks. The iLnkP2P system allows users to remotely connect to their IoT devices using a mobile phone or a PC. Potentially affected IoT devices include cameras and smart doorbells. Pierluigi Paganini.

Security Affairs
FEBRUARY 18, 2020
Even before the appearance of the word (I)IoT, I was breaking hardware devices, as many of you, with a multitude of debuggers (i.e. But it saves my time while hacking (I)IoT targets. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. SecurityAffairs – hacking IoT, Focaccia board).

Security Affairs
AUGUST 6, 2019
The STRONTIUM Russia-linked APT group is compromising common IoT devices to gain access to several corporate networks. Researchers at Microsoft observed the Russia-linked APT group STRONTIUM abusing IoT devices to gain access to several corporate networks. ” IoT risk must be taken seriously. ” continues Microsoft.

Malwarebytes
MAY 25, 2022
XorDDoS, a Linux Trojan known for its modularity and stealth, was first discovered in 2014 by the white hat research group, MalwareMustDie (MMD). Security IoT devices. If you have an IoT device at home, know there are ways to secure it. If you plan to get an IoT device soon, buy from a well-known brand.

Security Affairs
OCTOBER 19, 2020
The news is not surprising, unfortunately in many cases IoT devices, including IP cameras, are deployed without proper security measures. As worrying as it may seem, this comes as a clear reminder that when cameras are placed on the internet, they must be properly installed with security in mind. ” continues the article.
Security Affairs
JULY 14, 2020
Researchers spotted a new version of the Mirai IoT botnet that includes an exploit for a vulnerability affecting Comtrend routers. Malware researchers at Trend Micro have discovered a new version of the Mirai Internet of Things (IoT) botnet that includes an exploit for the CVE-2020-10173 vulnerability impacting Comtrend routers.

Security Affairs
AUGUST 27, 2020
To perform the experiment, we used Internet of Things (IoT) search engines to search for open devices that utilized common printer ports and protocols. After filtering out most of the false positives, we were left with more than 800,000 printers that had network printing features enabled and were accessible over the internet.
Security Affairs
APRIL 24, 2020
The Hoaxcalls IoT botnet expanded the list of targeted devices and has added new distributed denial of service (DDoS) capabilities. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->. SecurityAffairs – Hoaxcalls, IoT botnet).
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content