Financial cyberthreats in 2023
SecureList
MAY 6, 2024
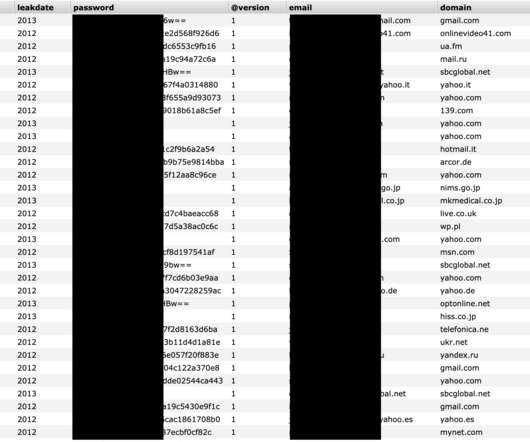
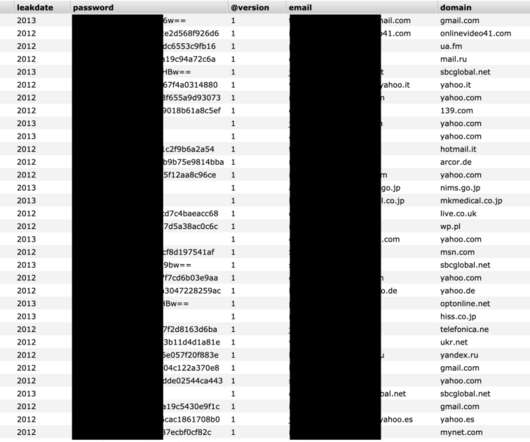
A significant share of scam, phishing and malware attacks is about money. Methodology In this report, we present an analysis of financial cyberthreats in 2023, focusing on banking Trojans and phishing pages that target online banking, shopping accounts, cryptocurrency wallets and other financial assets. million in 2022.














Let's personalize your content