Yahoo data breach settlement means affected users may get $100
Tech Republic Security
SEPTEMBER 19, 2019
If you had a Yahoo account between January 1, 2012 and December 31, 2016, you may be entitled to a bit of money.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
SEPTEMBER 19, 2019
If you had a Yahoo account between January 1, 2012 and December 31, 2016, you may be entitled to a bit of money.
Krebs on Security
APRIL 16, 2024
For nearly a dozen years, residents of South Carolina have been kept in the dark by state and federal investigators over who was responsible for hacking into the state’s revenue department in 2012 and stealing tax and bank account information for 3.6 said investigators determined the breach began on Aug. million people.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

SecureWorld News
MARCH 24, 2022
Now, headlines about ransomware, cyberattacks, and data breaches pour into social media feeds as steady as a river flows. SecureWorld News takes a look at some of the largest data breaches to ever occur. Top 10 most significant data breaches. Yahoo data breach (2013). Who attacked: no attacker.
Krebs on Security
NOVEMBER 14, 2024
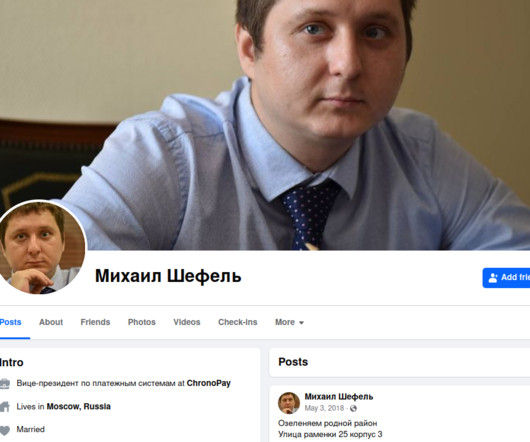
But not long after KrebsOnSecurity reported in April that Shefel/Rescator also was behind the theft of Social Security and tax information from a majority of South Carolina residents in 2012, Mr. Shefel began contacting this author with the pretense of setting the record straight on his alleged criminal hacking activities. Image: U.S.

Security Affairs
JANUARY 20, 2020
. “On June 28, last year, a suspicious behavior was detected and investigated on a terminal in our company, and as a result of unauthorized access by a third party, data was transmitted to the outside,” reads a data breach notification published by the company. SecurityAffairs – data breach, hacking).
Troy Hunt
NOVEMBER 22, 2019
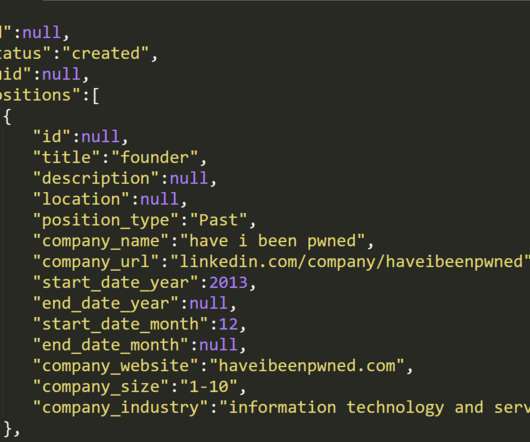
I've become more familiar with this sector over recent years due to the frequency with which it's been suffering data breaches that have ultimately landed in my inbox. i'm also the creator of the data breach aggregation service known as "have i been pwned". Well, almost nothing.
Troy Hunt
JANUARY 19, 2023
Have a look at the video and watch how at about the 4:20 mark he talks about using proxies "to prevent Nike from flagging your accounts" He recommends using the same number of proxies as you have accounts, inevitably to avoid Nike's (automated) suspicions picking up on the anomaly of a single IP address signing up multiple times.

SecureWorld News
DECEMBER 29, 2020
Now headlines about ransomware, cyberattacks and data breaches pour into social media feeds at a steady drumbeat. SecureWorld now takes a look at some of the largest data breaches to ever occur. Top 10 most significant data breaches. Yahoo data breach (2013). Equifax data breach (2017).

Security Affairs
MAY 29, 2019
The news aggregator Flipboard announced that it suffered a breach, unauthorized users had access to some databases storing user account information. The news and social media aggregator Flipboard disclosed on Tuesday that it suffered a breach, unauthorized users had access to some databases storing user information.

Malwarebytes
JULY 12, 2024
In a new episode of Spy vs Spy , the mobile monitoring app mSpy has suffered a data breach that exposed information about millions of its customers. This is the third known mSpy data breach since the company began in around 2010. Such programs are easy to buy and install.

SecureWorld News
NOVEMBER 30, 2021
The Starwood reservation system it was acquiring had been hacked, because of a data breach that began long before the two companies became one. DNA testing company data breach impacts personal information. The impacted database was associated with a national genetic testing organization system that DDC acquired in 2012.
Security Affairs
FEBRUARY 26, 2021
Data Breach: WizCase team uncovered a massive data leak containing private information about Turkish Citizens through a misconfigured Amazon S3 bucket. Inova has been operating since 2012 and has handled thousands of cases since then. How Did the Data Breach Happen? How and Why We Discovered the Breach.
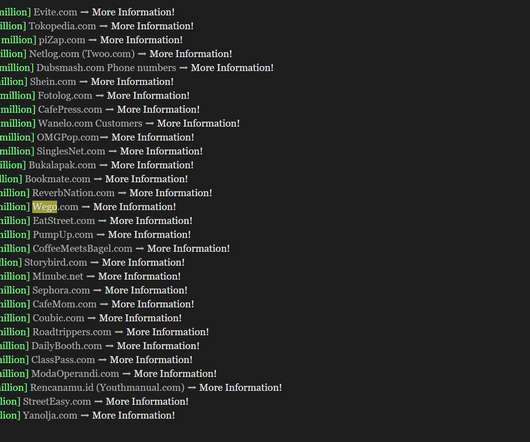
Security Affairs
MAY 15, 2020
Data appears to come from past data breaches, the oldest one dates back as 2012 while the latest one dates April 2020. million phone numbers that are part of Dubsmash data breach that occurred in 2018. million April 2018 Netlog.com (Twoo.com) 57 million November 2012 Dubsmash.com Phone numbers 47.1
Krebs on Security
DECEMBER 3, 2021
Cyber intelligence platform Constella Intelligence told KrebsOnSecurity that the operns@gmail.com address was used in 2016 to register an account at filmai.in , which is a movie streaming service catering to Lithuanian speakers. The username associated with that account was “ bo3dom.” com back in 2011, and sanjulianhotels[.]com

Krebs on Security
FEBRUARY 16, 2022
Asked to comment on Sheriff’s claims, the ICRC issued the following statement: “Right now, we do not have any conclusive evidence that this information from the data breach has been published or is being traded. Our cybersecurity team has looked into any reported allegation of data being available on the dark web.”

Security Affairs
FEBRUARY 11, 2019
620 million accounts stolen from 16 hacked websites (Dubsmash, Armor Games, 500px, Whitepages, ShareThis) available for sale on the dark web. The Register revealed in exclusive that some 617 million online account details stolen from 16 hacked websites are available for sale on the dark web. “I need the money. Pierluigi Paganini.

Krebs on Security
JUNE 25, 2019
An online search for the term “yehuo” reveals an account on the Chinese Software Developer Network which uses that same nickname and references the domain blazefire[.]com. com 2012-11-26 ALIBABA CLOUD COMPUTING (BEIJING) CO., com 2012-11-26 ALIBABA CLOUD COMPUTING (BEIJING) CO., 2333youxi[.]com blazefire[.]com

Security Affairs
JULY 11, 2020
The Russian hacker Yevgeniy Nikulin found guilty for LinkedIn, Dropbox, and Formspring data breach back in 2012 and the sale of their users’ data. Nikulin used data stolen from Linkedin to launch spear-phishing attacks against employees at other companies, including Dropbox. Source: US Defense Watch.com.

Troy Hunt
NOVEMBER 6, 2023
I like to think of investigating data breaches as a sort of scientific search for truth. You start out with a theory (a set of data coming from an alleged source), but you don't have a vested interested in whether the claim is true or not, rather you follow the evidence and see where it leads. accounts expands out to 5.8M

Troy Hunt
JUNE 10, 2019
Back in 2013, I was beginning to get the sense that data breaches were becoming a big thing. Increasingly, I was writing about what I thought was a pretty fascinating segment of the infosec industry; password reuse across Gawker and Twitter resulting in a breach of the former sending Acai berry spam via the latter.

Security Affairs
JULY 24, 2024
Remote attackers can exploit the flaw to execute arbitrary code via a crafted web site that triggers access to an object that (1) was not properly allocated or (2) is deleted, as demonstrated by a CDwnBindInfo object, and exploited in the wild in December 2012. is a use-after-free issue in Microsoft Internet Explorer 6 through 8.

Duo's Security Blog
NOVEMBER 20, 2023
“It took nearly 11 months (328 days) to identity and contain data breaches resulting from stolen or compromised credentials.” – IBM’s Cost of Data Breach Report 2023 I recently came across a 2012 article from CSO Online , and realized that it has been more than 11 years since the phrase “Identity is the new perimeter” was coined!

SiteLock
AUGUST 27, 2021
It’s been a busy time for data breaches in the social media world with Myspace, LinkedIn and Twitter all experiencing them. In each of these cases, the cybercriminals behind the breaches were after usernames and passwords. Peace stole data from over 360 million Myspace accounts. 29 milliseconds to crack them.

Krebs on Security
JULY 18, 2023
com , a service that sold access to billions of passwords and other data exposed in countless data breaches. LeakedSource was advertised on a number of popular cybercrime forums as a service that could help hackers break into valuable or high-profile accounts. An administrator account Xerx3s on Abusewithus.
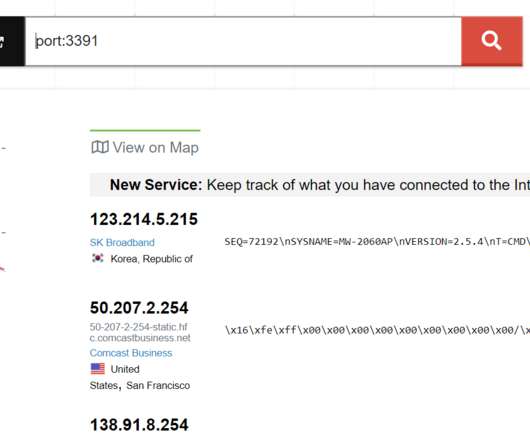
Security Affairs
JANUARY 25, 2020
“On June 28, last year, a suspicious behavior was detected and investigated on a terminal in our company, and as a result of unauthorized access by a third party, data was transmitted to the outside,” reads a data breach notification published by the company. An attempted attack requires user authentication.”

Malwarebytes
JUNE 30, 2021
Note that account credentials and banking details don’t appear to be part of the proof. This suggests that the data was scraped rather than breached. Scraping happens when somebody uses a computer program to pull public data from a website, using the website in a way it wasn’t intended to be used.

Krebs on Security
JUNE 25, 2019
An online search for the term “yehuo” reveals an account on the Chinese Software Developer Network which uses that same nickname and references the domain blazefire[.]com. com 2012-11-26 ALIBABA CLOUD COMPUTING (BEIJING) CO., com 2012-11-26 ALIBABA CLOUD COMPUTING (BEIJING) CO., 2333youxi[.]com blazefire[.]com
Krebs on Security
JANUARY 8, 2024
KrebsOnSecurity began researching Icamis’s real-life identity in 2012, but failed to revisit any of that research until recently. In December 2023, KrebsOnSecurity published new details about the identity of “Rescator,” a Russian cybercriminal who is thought to be closely connected to the 2013 data breach at Target.

SC Magazine
JUNE 2, 2021
A woman speaking on a mobile phone walks past a cloud computing presentation ahead of the CeBIT technology trade fair in 2012. While this raises some concerns, the Thales 2021 Data Threat Report , based on a study by 451 Research, pointed to some improvement in regulated industries. Sean Gallup/Getty Images).
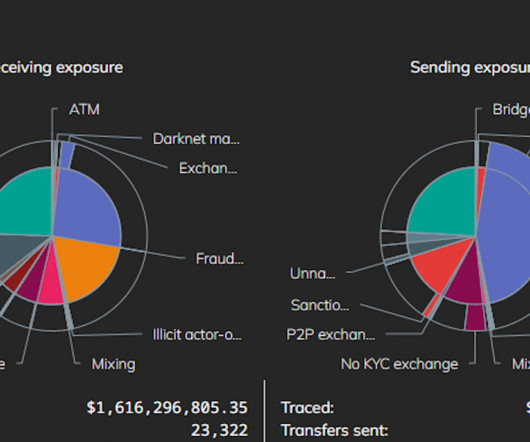
Krebs on Security
SEPTEMBER 26, 2024
The United States today unveiled sanctions and indictments against the alleged proprietor of Joker’s Stash , a now-defunct cybercrime store that peddled tens of millions of payment cards stolen in some of the largest data breaches of the past decade. This batch of some five million cards put up for sale Sept.

Security Affairs
NOVEMBER 7, 2022
The bad actors claim to have stolen a significant volume of data, including CRM records, personal information, email communications, contracts, and account credentials. The same day, Justice Blade also set up a Telegram account with a private communications channel. According to Resecurity, Inc.

Security Affairs
DECEMBER 21, 2022
A company spokesman declared that there are no indications of a data breach. Thyssenkrupp is currently the target of a cyberattack — presumably by organized crime” and that “at the present time, no damage has been done, nor are there any indications that data has been stolen or modified.”
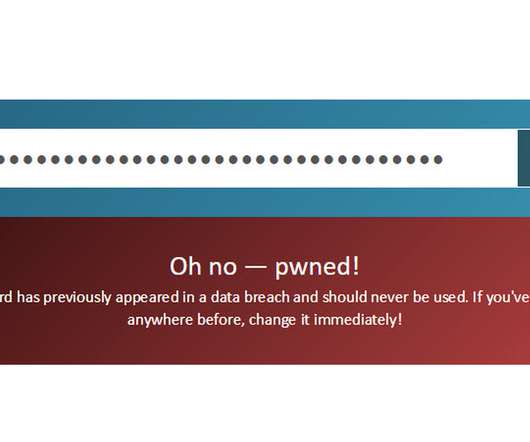
Malwarebytes
DECEMBER 21, 2021
(HIBP) allows users to type in an email address, phone number or password and find out how many times they’ve been involved in a data breach. So, what do you do now, knowing that your account might have been compromised? Lastly, use two-factor authentication (2FA) to add a layer of protection to your accounts.

Hot for Security
FEBRUARY 23, 2021
Credit reporting agency Tokyo Shoko Research (TSR), which compiled the data, says the number is the highest since it began collecting it in 2012, reported the Japan Times. million people was compromised, but the real figure is likely much higher since many unlisted companies also suffered breaches and / or data leaks.
Security Affairs
MARCH 10, 2023
The NetWire Remote Access Trojan (RAT) is available for sale on cybercrime forums since 2012, it allows operators to steal sensitive data from the infected systems. DomainTools further shows this email address was used to register one other domain in 2012: wwlabshosting[.]com, ” reads the press release published DoJ.
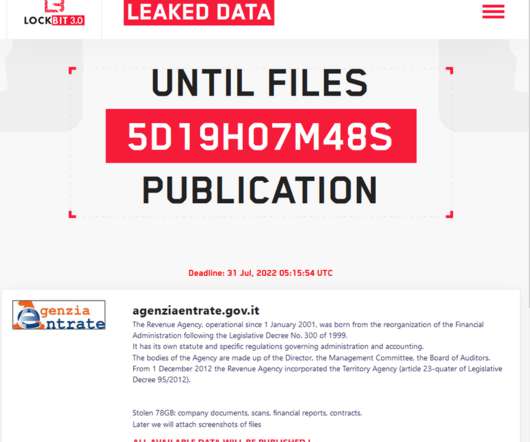
Security Affairs
JULY 25, 2022
It has its own statute and specific regulations governing administration and accounting. “From 1 December 2012 the Revenue Agency incorporated the Territory Agency (article 23-quater of Legislative Decree 95/2012).” The bodies of the Agency are made up of the Director, the Management Committee, the Board of Auditors.”
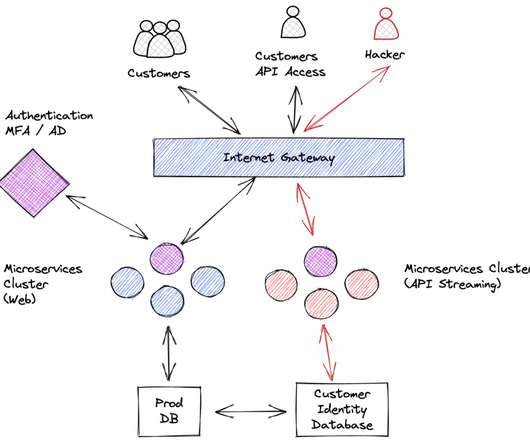
Security Boulevard
SEPTEMBER 26, 2022
On Thursday this week, Australia’s second-largest telecom company , Optus, announced it had suffered a major data breach that had compromised sensitive customer information. Jeremy Kirk on Twitter: "Someone is claiming to have the stolen Optus account data for 11.2 million users. million users. What happened?

Thales Cloud Protection & Licensing
NOVEMBER 14, 2017
The modern era of mass data breaches perhaps began in 2009, with the hack of 32 million account credentials held by software developer RockYou, in which a SQL injection attack revealed that passwords were simple held in cleartext in a database table. The following year saw a leak from Gawker Media’s servers, with another 1.5
Troy Hunt
SEPTEMBER 17, 2020
— Scott Hanselman (@shanselman) April 4, 2012 I was reminded of this only a few days ago when I came across yet another Windows virus scam, the kind that's been doing the rounds for a decade now but refuses to die. Maybe they're plugging into the API directly from the account page there? " It means "this is private."

Malwarebytes
JULY 21, 2021
We’ve written at length about account compromise and identity theft , and how criminals will often hijack accounts belonging to dead people. The amount of abandoned accounts due to death can only ever go up, and nobody is really paying attention if someone accesses them illicitly. By that point it could already be too late.

Security Affairs
JULY 18, 2023
Introduced in 2012, FIA WEC features eight endurance races across the world, including its cornerstone stage – 24 hours at Le Mans. They may engage in fraudulent activities, create bank accounts, apply for loans. Both combined, they contained over 1.1 million files.

SiteLock
AUGUST 27, 2021
In its annual Data Breach Investigations Report , published at the beginning of 2013, Verizon revealed that businesses with fewer than 100 employees made up the single largest group of victims of data breaches. bank accounts in 2012 by cybercrooks using malware like keyloggers.

McAfee
NOVEMBER 10, 2021
Under the guidance of Dan Meacham, VP of Global Security and Corporate Operations and CSO/CISO, the multi-billion dollar organization transitioned from on-premises data centers to the cloud in 2012. MVISION CNAPP helps me keep my system administrators and developers accountable for what they are doing. Learn more.

SiteLock
AUGUST 27, 2021
And we know this because of another major security problem, data breaches. Thanks to hundreds of data breaches that have exposed millions of personal files and passwords, we now know exactly what kinds of passwords users are using. Focus on your most important passwords.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content