Russian Cybersecurity Executive Arrested for Alleged Role in 2012 Megahacks
Krebs on Security
JUNE 29, 2023
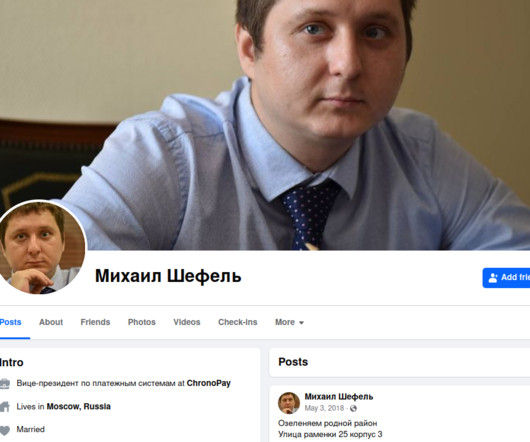
Kislitsin is accused of hacking into the now-defunct social networking site Formspring in 2012, and conspiring with another Russian man convicted of stealing tens of millions of usernames and passwords from LinkedIn and Dropbox that same year. Nikita Kislitsin, at a security conference in Russia. prison system.






















Let's personalize your content