New Leak Shows Business Side of China’s APT Menace
Krebs on Security
FEBRUARY 22, 2024
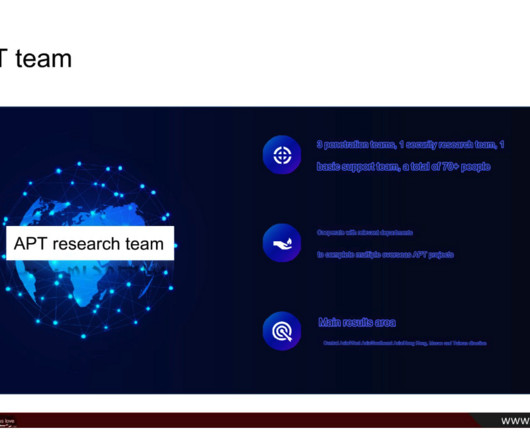
Security experts who reviewed the leaked data say they believe the information is legitimate, and that i-SOON works closely with China’s Ministry of State Security and the military. In 2021, the Sichuan provincial government named i-SOON as one of “the top 30 information security companies.”




















Let's personalize your content