PlayStation Network outage has been going on for over 24 hours
Security Affairs
FEBRUARY 8, 2025
The PSN breach exposed the data of millions of users, costing Sony $15 million in settlements and a year of identity theft protection for subscribers.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Security Affairs
FEBRUARY 8, 2025
The PSN breach exposed the data of millions of users, costing Sony $15 million in settlements and a year of identity theft protection for subscribers.

Security Affairs
NOVEMBER 10, 2024
government agency created in 2011 to protect consumers in the financial sector, ensuring fair, transparent, and competitive financial markets The agency has issued a directive to employees to reduce the use of their phones and invite them to use Microsoft Teams and Cisco WebEx for their meetings and conversations that involve nonpublic data.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
FEBRUARY 6, 2024
“According to the indictment, between 2011 and July 2017, Aliaksandr Klimenka, 42, allegedly controlled BTC-e, a digital currency exchange, with Alexander Vinnik and others.” The authorities reported that since 2011, 7 million Bitcoin had gone into the BTC-e exchange and 5.5 ” reads the press release published by DoJ.

Security Affairs
MAY 31, 2020
.” The EU agency launched this project to improve the detection of network security incidents in the EU, by: Providing an inventory of available measures and information sources; Identifying good practices; Recommending possible areas for development. 2- Report – Measures and information sources.

Security Affairs
JUNE 9, 2023
Gox in 2011 and money laundering. Gox in 2011 and the operation of the illicit cryptocurrency exchange BTC-e. Bilyuchenko is also charged with conspiring with Alexander Vinnik to run the virtual currency exchange BTC-e from 2011 to 2017. Two Russian nationals have been charged with the hack of the cryptocurrency exchange Mt.
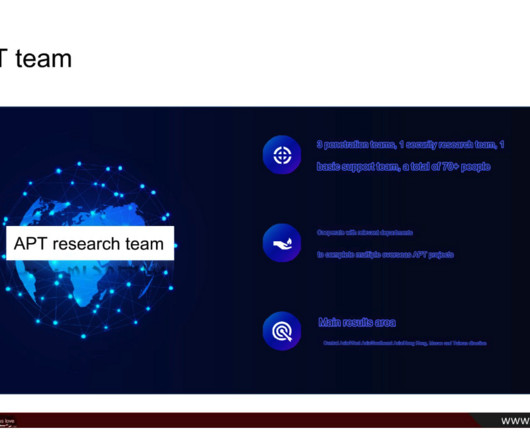
Krebs on Security
FEBRUARY 22, 2024
Security experts who reviewed the leaked data say they believe the information is legitimate, and that i-SOON works closely with China’s Ministry of State Security and the military. In 2021, the Sichuan provincial government named i-SOON as one of “the top 30 information security companies.”

Security Affairs
OCTOBER 4, 2020
Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->.

Security Affairs
MARCH 18, 2024
This isn’t the first incident suffered by IMF, the agency suffered a major security breach in 2011. Bleeping computer contacted IMF, which confirmed that that despite it uses the Microsoft 365, the incident does not appear to be part of Microsoft targeting recently disclosed.

Security Affairs
SEPTEMBER 9, 2022
Last week, Google rolled out emergency fixes to address a vulnerability, tracked as CVE-2022-3075 , in the Chrome web browser that is being actively exploited in the wild.
SecureWorld News
MAY 26, 2022
But instead of using this information for the sole purpose of improving security, Twitter profited by allowing advertisers to use this data to target individuals. This action violated a 2011 FTC order that prohibited the social media site from misrepresenting its privacy and security practices. FTC Chair Lina M.

Security Affairs
NOVEMBER 15, 2021
I launched Security Affairs for passion in 2011 and millions of readers walked with me. Ten years ago I launched Security Affairs, the blog over the past decade obtained important successes in the cyber security community, but the greatest one is your immense affection. Ten years together! I’m very excited.
Security Affairs
OCTOBER 16, 2021
FinCEN analyzed a data set composed of 2,184 SARs filed between 1 January 2011 and 30 June 2021 and identified 177 CVC (convertible virtual currency) wallets addresses that were used in ransomware operations associated with the above ransomware variants.

Security Affairs
APRIL 21, 2022
Security researchers at Check Point Research have discovered a critical remote code execution that affects the implementation of the Apple Lossless Audio Codec (ALAC) in Android devices running on Qualcomm and MediaTek chipsets. ALAC was developed in 2004 and Apple open-sourced it in 2011, since then many third-party vendors used it.

Security Affairs
SEPTEMBER 5, 2022
It has already happened in the past that the popular antivirus software has identified Chrome as a malicious code, the website The Register reported a similar problem in 2011. The post Windows Defender identified Chromium, Electron apps as Hive Ransomware appeared first on Security Affairs. on September 4, 2022. Pierluigi Paganini.

Security Affairs
JULY 19, 2021
US DoJ indicted four members of the China-linked cyberespionage group known as APT40 for hacking various entities between 2011 and 2018. Ltd. (????)

Security Affairs
MAY 29, 2022
He joined the gang in August 2011 and worked for the organization for five-and-a-half years, DoJ states that he was among the most prolific and active members of the gang. Security Affairs is one of the finalists for the best European Cybersecurity Blogger Awards 2022 – VOTE FOR YOUR WINNERS.
Security Affairs
MAY 15, 2020
The vendor also fixed a high-severity vulnerability, tracked as CVE-2020-2011 , that could be exploited by a remote, unauthenticated attacker to trigger a denial-of-service (DoS) condition to all Panorama services by sending specially crafted registration requests.

Security Affairs
APRIL 29, 2021
According to the researchers who discovered the issue, the flaw was introduced in November 2011. The vulnerability stems from improper sanitization of URLs for repositories in root composer.json files and package source download URLs that could be interpreted as options for system commands executed by Composer.

Security Affairs
APRIL 22, 2024
Compromised data vary by individuals and organizations, it includes names, passport numbers, Social Security numbers, online crypto account identifiers and bank account numbers, and more. Curiously, in 2011, Thomson Reuters acquired World-Check, then in October 2018, Thomson Reuters closed a deal with The Blackstone Group.
Security Affairs
DECEMBER 15, 2020
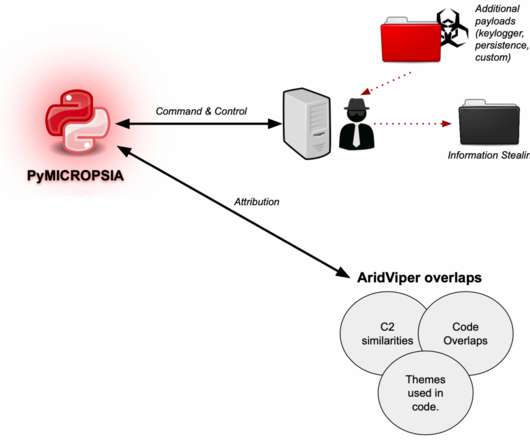
AridViper is an Arabic speaking APT group that is active in the Middle East since at least 2011. Experts spotted the PyMICROPSIA info stealer while investigating attacks of the AridViper group (also tracked as Desert Falcon and APT-C-23 ).
Security Affairs
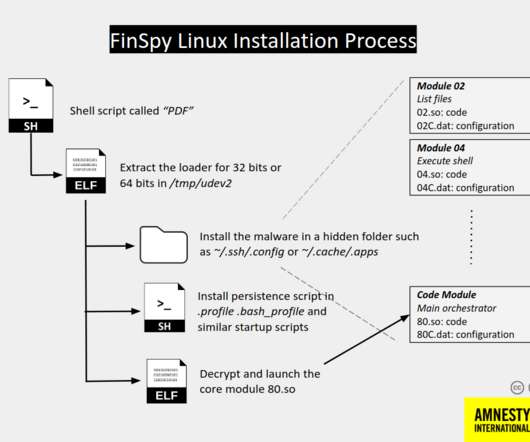
SEPTEMBER 27, 2020
Since 2011 it was employed in attacks aimed at Human Rights Defenders (HRDs) in many countries, including Bahrain, Ethiopia, UAE, and more. FinSpy can spy on most popular desktop and mobile operating systems, including Android, iOS, Windows, macOS, and Linux.

Security Affairs
NOVEMBER 22, 2021
The US had sanctioned Mahan Air in 2011 for providing financial, material, or technological support to Iran’s Islamic Revolutionary Guard Corps. . #????? #??_??_??????_?????? #IranProtests #MahanAir pic.twitter.com/bBkfBKJ4uK — Hooshyarane Vatan (@Hooshyaran1) November 21, 2021.

Security Affairs
MAY 22, 2021
million of its customers, exposed data includes the personal information of customers registered between August. 26, 2011 and February. Air India has disclosed a data breach that impacted 4.5

Security Affairs
DECEMBER 17, 2021
and above 2011 Workspace ONE UEM patch 20.11.0.40 .” Below is the list of impacted versions: I mpacted Versions Fixed Version 2109 Workspace ONE UEM patch 21.9.0.13 and above 2105 Workspace ONE UEM patch 21.5.0.37 and above 2102 Workspace ONE UEM patch 21.2.0.27 and above 2101 Workspace ONE UEM patch 21.1.0.27 and above.

Security Affairs
OCTOBER 19, 2020
The authorities reported that since 2011, 7 million Bitcoin went into the BTC-e exchange and 5.5 In 2017, Greek Police arrested the Russian national Alexander Vinnik and they accused the man of running the BTC-e Bitcoin exchange to launder more than US$4bn worth of the cryptocurrency. million withdrawn.

Security Affairs
JULY 26, 2019
According to FBI, between February of 2011 and July 2013, Silk Road managed $1.2 Silk Road was seized by law enforcement in 2013 and his founder Ross William Ulbricht (aka Dread Pirate Roberts) was arrested, later it was sentenced to life in prison after being convicted on multiple counts related to the Silk Road activity.

Security Affairs
JANUARY 12, 2022
Russian state-sponsored APT actors’ global Energy Sector intrusion campaign, 2011 to 2018. Some of the hacking campaigns that were publicly attributed to Russian state-sponsored APT actors by U.S. Russian state-sponsored APT actors’ campaign against Ukrainian critical infrastructure, 2015 and 2016. . Pierluigi Paganini.

Security Affairs
FEBRUARY 13, 2020
We spent searching holes in Italian universities (and not only, we remember that dozens of universities were hacked in 2011), to try to show you that security in the academic environment must be taken seriously since the university is the den of the excellent minds of our future. Below the translation of message published by the group.

Security Affairs
JANUARY 2, 2022
It is estimated that the cryptocurrencies stolen between January 2011 and December 2021 amount to $12.1 The countries where cryptocurrencies were most popular suffered major losses, including Japan, South Korea, the United States, the United Kingdom, and China. ” reads the report published by Invezz. .

Security Affairs
NOVEMBER 15, 2022
Happy BirthDay Security Affairs! I launched Security Affairs for passion in November 2011 and since then the blog was visited by tens of millions of readers. Eleven years ago I decided to launch Security Affairs, a blog that is considered today one of the most valuable sources of the cybersecurity industry.

The Last Watchdog
JUNE 21, 2020
Balaban This ransomware was doing the rounds over spam generated by the Gameover ZeuS botnet, which had been originally launched in 2011 as a toolkit for stealing victim’s banking credentials and was repurposed for malware propagation.
Security Affairs
OCTOBER 14, 2020
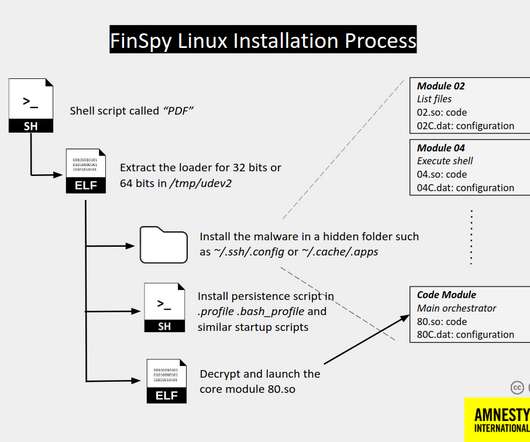
Since 2011 it was employed in attacks aimed at Human Rights Defenders (HRDs) in many countries, including Bahrain, Ethiopia, UAE, and more. FinSpy can spy on most popular desktop and mobile operating systems, including Android, iOS, Windows, macOS, and Linux.

Security Boulevard
APRIL 26, 2022
The cyber kill chain is an adaptation of a military concept to the world of information security. Developed by technology corporation Lockheed Martin back in 2011, the cyber kill chain outlines the stages common to most cyberattacks. The post Analyzing the 7 Cyber Kill Chain Steps appeared first on Nuspire.
Security Affairs
DECEMBER 7, 2021
The blockchain-enabled botnet has been active since at least 2011, researchers estimate that the Glupteba botnet is currently composed of more than 1 million Windows PCs around the world.

Security Affairs
NOVEMBER 21, 2019
According to a report published by Symantec in 2017, Longhorn is a North American hacking group that has been active since at least 2011. The new DePriMon downloader was used by the Lambert APT group, aka Longhorn, to deploy malware.
Security Affairs
MAY 23, 2020
The source code of the Zeus Trojan is available in the cybercrime underground since 2011 allowing crooks to develop their own release since. Experts found multiple variants in the wild, many of them belonging to the Terdot Zbot/Zloader malware family.

Security Affairs
SEPTEMBER 11, 2023
Microsoft has been tracking the threat actors at least since 2013, but experts believe that the cyberespionage group has been active since at least 2011 targeting journalists and activists in the Middle East, as well as organizations in the United States, and entities in the U.K., Israel, Iraq, and Saudi Arabia.
Security Affairs
OCTOBER 26, 2020
“During our research we witnessed its evolution from a medium-volume botnet with basic abilities to a massive infrastructure that is here to stay,” Imperva concludes.

Security Affairs
JULY 17, 2020
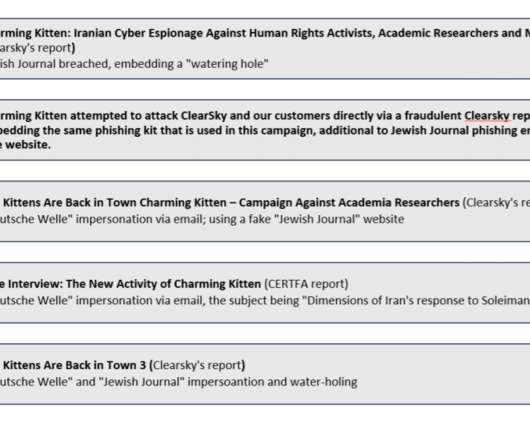
Iran-linked Charming Kitten group, (aka APT35 , Phosphorus , Newscaster , and Ajax Security Team) made the headlines in 2014 when experts at iSight issued a report describing the most elaborate net-based spying campaign organized by Iranian hackers using social media. continues IBM.
Security Affairs
AUGUST 28, 2020
Iran-linked Charming Kitten group, (aka APT35 , Phosphorus , Newscaster , and Ajax Security Team) made the headlines in 2014 when experts at iSight issued a report describing the most elaborate net-based spying campaign organized by Iranian hackers using social media. Israel, Iraq, and Saudi Arabia.

Security Affairs
MAY 6, 2024
Alexander Vinnik , a Russian national, pleaded guilty to conspiracy to commit money laundering for his involvement in operating the cryptocurrency exchange BTC-e from 2011 to 2017. Alexander Vinnik, a Russian operator of virtual currency exchange BTC-e pleaded guilty to participating in a money laundering scheme.

Security Affairs
JULY 21, 2021
Justice Department (DoJ) indicted four members of the China-linked cyber espionage group APT40 (aka TEMP.Periscope , TEMP.Jumper , and Leviathan ) for hacking tens of government organizations, private businesses and universities around the world between 2011 and 2018. Follow me on Twitter: @securityaffairs and Facebook.

Security Affairs
AUGUST 6, 2023
At the time of this writing, no ransomware group has claimed responsibility for the security breach. CDHE provides free access to the identify theft monitoring Experian IdentityWorks SM for 24 months.

Cisco Security
AUGUST 3, 2021
Pam joins us with 25 years experience in the IT industry, with her most recent role being Deputy Chief Information Security Officer at Anthem, Inc. I took an active role in understanding what the Security team were trying to achieve, and how my work and my team could help them.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content